
Advisory Alert: PowerSchool Data Breach
Reading Time: 4 minsThe December 2024 breach of a student information software solution for K-12 educational institutions, PowerSchool, leaves us asking: what can we learn from it?

Reading Time: 4 minsThe December 2024 breach of a student information software solution for K-12 educational institutions, PowerSchool, leaves us asking: what can we learn from it?
Reading Time: 5 minsFollowing the release of data from over 15,000 Fortinet devices, what can we do to protect against further compromise?
Reading Time: 4 minsDetecting and stopping attacks using anonymization techniques can give your team the upper hand against cyber criminals — but how do attackers use anonymization and how can we defend against it?
Reading Time: 4 minsLumu has worked hand-in-hand with MSPs throughout a year that consolidated the need for cybersecurity in the role of MSPs.
Get the latest cybersecurity articles and insights straight from the experts.
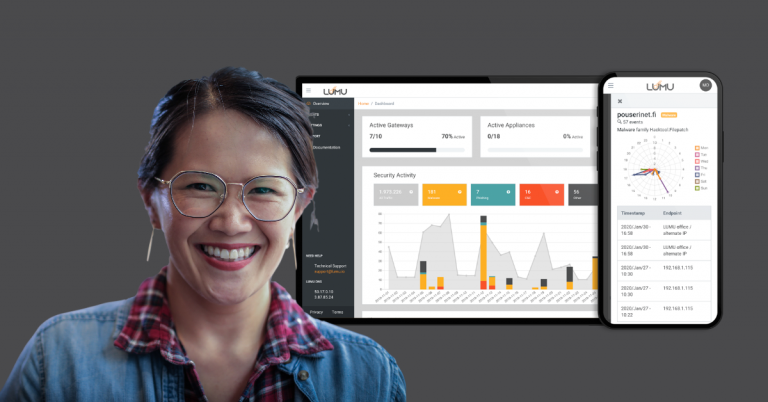
Reading Time: 2 minsThe Lumu Portal always manages to delight our customers. We looked at some of the most pleasantly surprising factors.

Reading Time: 3 minsAnalyzing spam metadata lets Lumu’s portal present insights on which users are being targeted and how your company is being compromised.

Reading Time: 4 minsLumu’s Illumination Summit has come and gone, but you can still relive every talk and discussion in our highlight video or blog.

Reading Time: 4 minsMalware Delivery as a Service is a specialized service designed to meet ransomware’s demand for access to compromised networks.

Reading Time: 3 minsLumu’s Illumination Summit is a unique experience for cybersecurity professionals. Here’s how it came about.

Reading Time: 4 minsArtificial intelligence and Machine Learning are increasingly popular in cybersecurity, but like all tools, the key is how you use them.

Reading Time: 2 minsCybersecurity Strategy needs to be more adaptable and resilient following the revelations brought about by the Covid-19 pandemic

Reading Time: 3 minsLumu now provides compromise context in one place, providing more insight into the nature of attacks and improving incident response

Reading Time: 2 minsNetwork metadata has the power to efficiently answer the most important question in cybersecurity: Is my network compromised?

Reading Time: < 1 minWe are thrilled to announce a new illumination milestone: 500 enterprises have embraced the power of Continuous Compromise Assessment™.

Reading Time: 2 minsThe economic downturn caused by the coronavirus will place financial pressure on cybersecurity budgets, forcing more intelligent spending.

Reading Time: 2 minsThe coronavirus pandemic has forced enterprises into a rushed transition to working remotely that exposes them to security breaches.

Reading Time: 2 minsThe coronavirus is an unprecedented challenge, but cybercriminals won’t lose focus. Neither should security practitioners.

Reading Time: 2 minsContinuous Compromise Assessment identifies cybercriminals in real time by using several cutting-edge technologies.

Reading Time: 2 minsLumu attended RSA Conference 2020, featuring on cybersecurity news sites including Dark Reading, CSO.com, and CRN.
© Lumu Technologies All rights reserved. | Legal information.