Much has been said about the ‘end of the perimeter.’ However, no one could have predicted how the coronavirus pandemic would force enterprises to adopt remote work and thereby change their security posture. Systems that have been built with the assumption that their users would be within their perimeter of defenses now have to work with most of their workforce being outside the perimeter. While there might not be anything wrong with a system like this, being forced to make the change overnight—in some cases without the necessary planning, testing, or oversight—exposes businesses to novel risks.
Network Defenses Before and After COVID-19
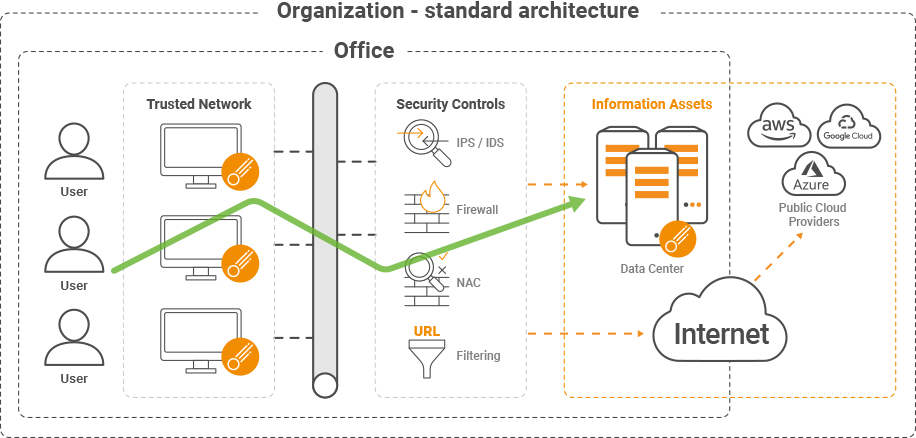
The standard network architecture model is built for and only works when the user is situated in the system. Overnight, every employee has migrated to a connection via VPN or modern Software Defined Perimeters (SDP), exposing those devices to the unsecured internet. The assumption that the physical network is a chokepoint through which all traffic flows, has been undone. IT teams might have been focused on business continuity, but security continuity is crucial in this case. For example, phishing attacks have always sought to bypass defenses by targeting email. The difference is that now the end-users don’t have the same layers of protection that guard against clicking on malicious content, as well as prevent that content from compromising your organization. Relying on the end-user not to engage with malicious content is a risky roll of the dice.
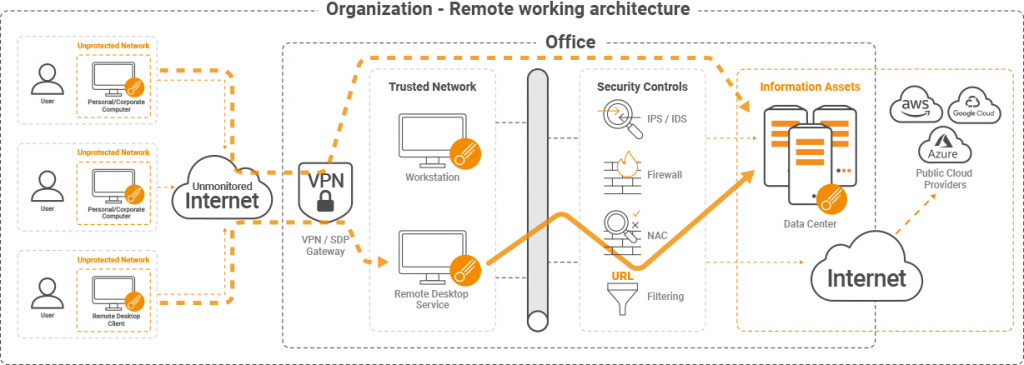
The location of an enterprise’s assets has not changed. The data is still hosted in the cloud or in on-site data centers, but more than ever, they are exposed to compromise coming from unprotected users. That is why there is an unprecedented need to assume that you have already been compromised, and prove otherwise. This state of affairs demands uninterrupted compromise visibility.
We are in a position to help organizations enhance their visibility into the compromise level of their critical assets with the free version of Lumu. By integrating Lumu DNS servers with an enterprise’s VPN configuration, Lumu Free can also determine if a user’s remote endpoints are communicating with adversarial infrastructure. This gives them the information they wouldn’t have otherwise, in a way that is simple and consumable. If you want to learn how Lumu and your VPN or SPD solutions can work in tandem to maintain your compromise visibility during the remote workforce era, click here. If you want to learn about Lumu Free, click here.
Security teams have had to rapidly adapt to working away from the tools, amenities, and direct access that they have at their offices. Meanwhile, they are getting bombarded with alerts. Getting visibility into what is real, confirmed compromise and what is a false negative is essential. The quicker security organizations can be exposed to all communication between their infrastructure and infrastructure from the adversary, the quicker they can mitigate and move on.