Table of Contents
Ransomware doesn’t appear out of thin air. The victim’s system is usually compromised by malware that paves a way for the ransomware package. With each step, threat actors are able to string various malware compromises together, each building upon its precursor, cultivating a malware ecosystem with the goal of completing a ‘ransomware chain’. Luckily, it’s possible to identify and break the weakest link in the chain.
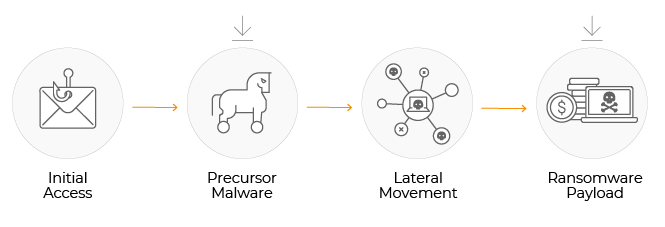
Infiltration & Initial Access
Threat actors use a variety of means to deploy their initial malware packages. Some tactics include:
- Email phishing
- Links in documents
- Batch files
- Executable programs
- Initial access markets
These actors tend to follow a “spray and pray” methodology, hoping to infect as many systems as possible. In this way, personal home computers and industrial systems can become infected. But at some point, the threat actors will reach a corporate system, and decide to achieve maximum monetization through ransomware.
At the end of this step, a precursor malware package will be deployed (see list below). This malware package will give the attacker more options for compromising the network and paving the way for ransomware delivery.
Lateral Movement
Knowing that they are in a corporate network, the malware’s operators will attempt to scout out assets within the network. They will map the network and search for sensitive data, credentials that will confer more privileges, and access to critical infrastructure.
There is a variety of tools that aid ransomware gangs in moving laterally. Some of them, like Cobalt Strike, were designed for legal, white-hat vulnerability assessments or penetration tests. Threat actors also conduct network scans in order to identify open ports and other vulnerabilities in the network.
There are also cases where the ransomware is applied directly by threat actors without the use of a preceding piece of malware. In these situations, the threat actors acquired access to the network through RDP, VPN, or compromised credentials and the lateral movement phase is a more manual task.
Ransomware Payload Delivery
Once the threat actor has gained enough power over the network, they will execute the ransomware package. This will result in data being encrypted, along with users being locked out of their systems. Once these actions have been successfully carried out, the ransomware demand is delivered. It’s also become popular to exfiltrate sensitive data to be used for blackmail and additional incentive to pay the ransom, in a strategy known as “double extortion”.
Ransomware Chain in Action: Trickbot
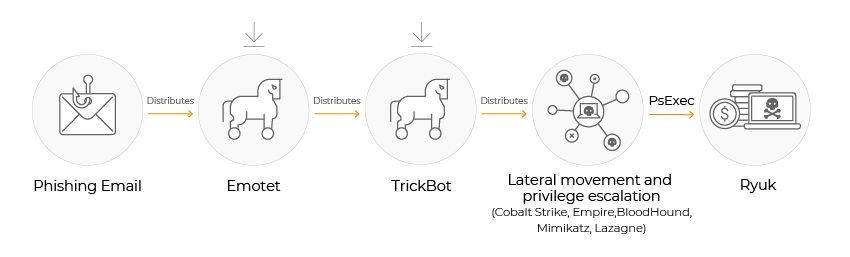
Trickbot is a prime example of the first link in a ransomware chain. It started out as a banking trojan that would target web browsers in order to gather and exfiltrate banking credentials and cookies. However, its capabilities have only expanded with time and each upgrade. Importantly, it self-updates, so that it can adapt to the system it occupies.
Malware researchers have analyzed 61 Trickbot modules that enable it to provide remote access, proxy network traffic, perform brute-force attacks, download other malware, and much more.
Trickbot is used as one of the first links in a chain that results in two of the most popular ransomware compromises: Conti and Ryuk.
Examples of Ransomware Chains
The following are some examples of precursor malware infections that lead to ransomware attacks:
BazarLoader ➡ BazarBackdoor ➡ Ryuk | ZLoader ➡ Ryuk |
TrickBot ➡ Ryuk | Zloader ➡ DarkSide |
Emotet ➡TrickBot ➡ Ryuk | SDBBot ➡ Clop |
Buer ➡Ryuk | Dridex ➡ DoppelPaymer |
Trickbot ➡Conti | Dridex ➡ BitPaymer |
Vatet ➡ PyXie ➡ Defray777 / RansomEXX | Gootkit ➡ REvil/ Sodinokibi |
IcedID ➡ Vatet ➡ Defray777 / RansomEXX | Phorpiex ➡ Avaddon |
IcedID ➡ Egregor | Phorpiex ➡ Nemty |
IcedID ➡ REviL / Sodinokibi | BazarLoader ➡ BazarBackdoor ➡ Conti |
Ursnif ➡ Egregor | DanaBot ➡ NonRansomware |
Qakbot ➡ Egregor | SmokeLoader ➡ Crysis/Dharma |
Qakbot ➡ ProLock | Vidar ➡ GranCrab |
Qakbot ➡ MegaCortex | Redline ➡ STOP/DJVU |
ZLoader ➡ Egregor | SmokeLoader ➡ STOP/DJVU |
Forensic Analysis of a Ransomware Chain
The following is an example of a real-life ransomware chain attack. Following the attack, the victim’s network metadata was injected into Lumu’s Illumination Process for retrospective forensic analysis.
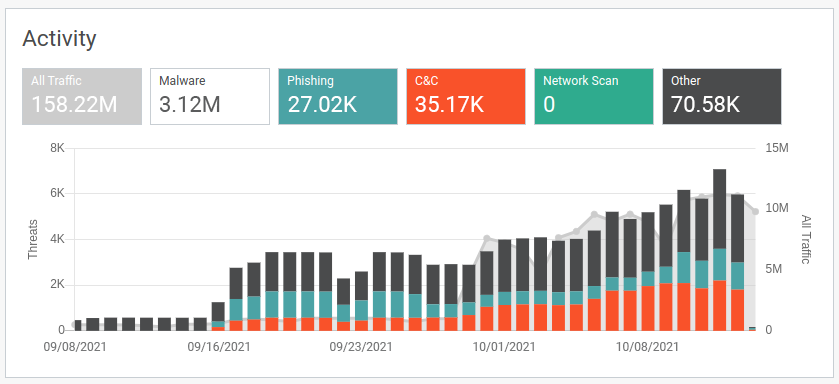
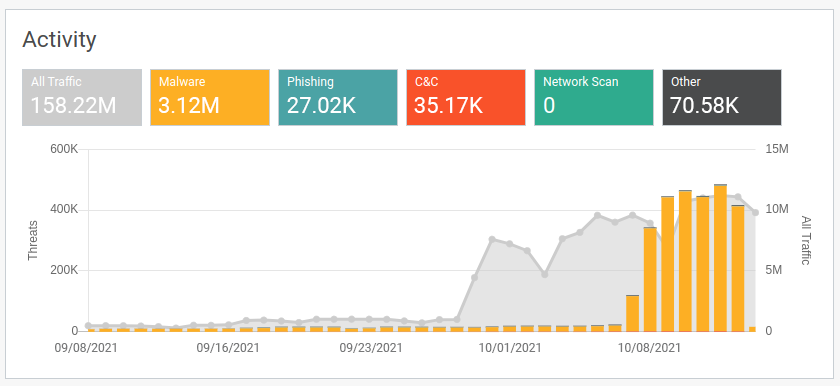
The above two images from the Lumu Portal show an example of where the attackers were successful in deploying a completely avoidable ransomware attack. The second image represents malware contacts (yellow), while the first shows all other types of contacts (phishing, C&C, etc). The data has been separated into two graphs since the scale of the malware contacts would make the other contact types appear marginal.
Initially, there was just some generic Conficker malware activity detected. The ransomware attack truly started with the deployment of an exploit kit based on RIG toolkit, when a user visited a compromised website that redirected the vulnerable web browser (Internet Explorer) to the exploit server, which was then able to load the distributed payload: SmokeLoader malware. Finally, the STOP/DJVU ransomware payload was delivered. As the C&C contacts (red) increased, there was initially no real increase in malware activity. This represents the ‘lateral movement’ phase of the attack. Finally, we can see the drastic increase in malware activity before the ultimate deployment of the STOP/DJVU ransomware. The entire attack, including initial access and lateral movement, took a bit less than 3 months to carry out. At the end, ransomware deployment took just 1 weekend.
There are a couple of key takeaways from this case study. Firstly, the initial compromise could easily have been chalked up as being a ‘minor’ or low-importance threat. In fact, All threats should be eradicated swiftly before they morph into a more serious breach like ransomware.
Secondly, even if the victim had the visibility into the network to see the precursor malware, it would mean little without fast, precise response capabilities. Where the SOC team is not able to manually operate the eradication of compromises, automation and orchestration can be used to integrate detection capabilities with prevention and response tools.
How to Break a Ransomware Chain
Ransomware attacks never happen in isolation. As you can see from both the ‘theory’ of how ransomware chains are propagated and the evidence from the Lumu portal, there are always other malicious contacts that precede it. These first malware contacts are the ‘weakest link’ in any ransomware chain. If they can be swiftly detected and removed, the ransomware chain is not able to progress.
It should also be apparent that ransomware operators have to make use of the network—at every step—in order to achieve their aims. This means that they inevitably leave behind footprints of their actions and movements in the metadata that all networks already create. Continuous Compromise Assessment™ was designed to standardize, ingest, and analyze this metadata in real time and deliver confirmed evidence of compromise.
Lumu looks at both the traffic between the network and the external infrastructure (North-South) and the internal traffic (East-West) to pinpoint the sources of compromises as they happen. In this way, security teams are given the information they need to eradicate compromises before they can turn into encrypted data, inaccessible systems, and a ransomware note.
The popularity of ransomware as a business model is being driven by the perfect storm of ransomware-as-a-service, malware-delivery-as-a-service, and initial access markets. We invite you to open a Lumu Free account so you too can recognize and break the weakest link in the ransomware chain.




