
Advisory Alert: CrowdStrike Outage – What We Know
Reading Time: 3 mins Learn about the recent CrowdStrike outage affecting Microsoft devices, its impact, recovery steps, and how Lumu can help ensure continued network security.

Reading Time: 3 mins Learn about the recent CrowdStrike outage affecting Microsoft devices, its impact, recovery steps, and how Lumu can help ensure continued network security.
Reading Time: 3 mins Learn how Lumu helps MSPs meet CIS compliance with real-time malware detection, network defense, and automated incident response.
Reading Time: 4 mins Essential cybersecurity tips to safeguard K-12 schools during the back-to-school season.
Reading Time: 3 mins Explore the Snowflake supply chain attack, how infostealer malware impacted hundreds of major companies, and essential measures to protect your organization from similar threats
Get the latest cybersecurity articles and insights straight from the experts.

Reading Time: 3 mins Learn how Lumu helps MSPs meet CIS compliance with real-time malware detection, network defense, and automated incident response.

Reading Time: 3 mins Learn about the recent CrowdStrike outage affecting Microsoft devices, its impact, recovery steps, and how Lumu can help ensure continued network security.

Reading Time: 4 mins Essential cybersecurity tips to safeguard K-12 schools during the back-to-school season.

Reading Time: 3 mins Explore the Snowflake supply chain attack, how infostealer malware impacted hundreds of major companies, and essential measures to protect your organization from similar threats

Reading Time: 4 mins Platformization can limit flexibility and innovation. Discover why an open SecOps Platform is essential for cybersecurity

Reading Time: 2 mins This VPN vulnerability highlights a typical risks associated with perimeter defenses, which can allow attackers to access networks. Stay informed and secure your network promptly.
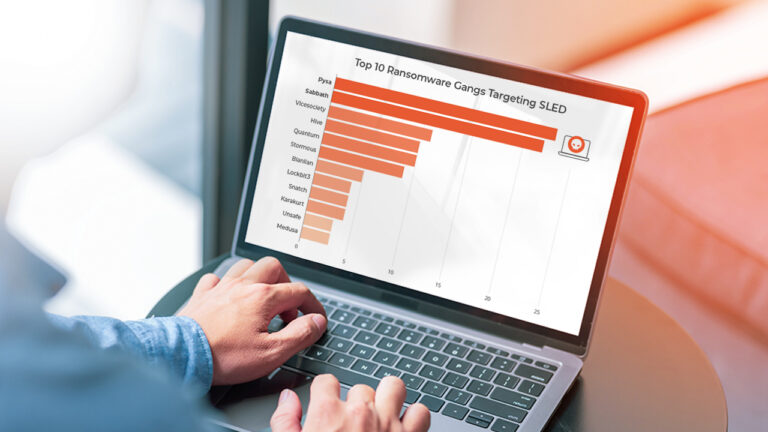
Reading Time: 6 mins Local Government and Education Institutions are under increasing threat from cyber criminals. Explore how these critical sectors can level up their cybersecurity posture.

Reading Time: 4 mins Missed RSA Conference 2024? Explore Lumu CEO and RSAC veteran Ricardo Villadiego’s perspective on the key takeaways from RSAC 2024

Reading Time: 5 mins Introducing Lumu Autopilot, the latest innovation that delivers on our promise to help the world operate cybersecurity proficiently.

Reading Time: 4 mins The Palo Alto Networks PAN-OS firewall vulnerability exemplifies critical flaws in traditional perimeter defenses. Understand how Lumu’s detection capabilities safeguard networks.

Reading Time: 2 mins Efficiently confirm and address ConnectWise ScreenConnect vulnerabilities with our guide and user-friendly tool.

Reading Time: 7 mins LockBit takedown news and guidance: arrests made, resilience shown, and future cybersecurity steps.

Reading Time: 3 mins Explore the challenges faced by a wide range of organizations in affording SOC analyst salaries amidst rising cybersecurity demands and limited budgets

Reading Time: 7 mins Explore how Infostealers compromise global security, silently stealing data and offering adversaries initial access.

Reading Time: 5 mins Dive into the impact and future of MSP Cybersecurity Disruption. Is it a looming threat or a hidden opportunity?
© Lumu Technologies All rights reserved. | Legal information.