Table of Contents
The United Kingdom’s National Crime Agency (NCA) has struck a significant blow against the notorious LockBit Ransomware gang. The joint operation, which involved numerous countries and agencies, resulted in the arrest of 4 criminals affiliated with LockBit. Despite this victory, LockBit’s swift migration to backup servers signals a resilient and looming challenge, as the group gears up to resume its criminal activities. This advisory provides an overview of the LockBit takedown and essential insights into the current situation, along with actionable recommendations and
What is LockBit?
LockBit is a ransomware-as-a-service (RaaS) operation that has been active since September 2019. It is one of the most prolific ransomware threats in the world and has been responsible for attacks on a wide range of organizations, including businesses, government agencies, and healthcare providers.
The group initially surfaced under the name ‘ABCD’ ransomware and changed months later to LockBit. Over time, it evolved into LockBit 2.0 in 2021, followed by the release of LockBit 3.0 in June 2022. In September of the same year, the source code was leaked, resulting in the creation of multiple variants derived from it.
How Does It Work?
LockBit Ransomware encrypts the files on a victim’s computer, making them inaccessible. The attackers then demand a ransom payment in cryptocurrency in exchange for decrypting the files. If the victim does not pay the ransom, the attackers may threaten to delete the files or leak them to the public.
LockBit operates on a subscription-based service model, providing members with the tools and administration portals necessary to orchestrate attack chains including payment services. This ransomware exhibits the capability to autonomously spread within an organization, leveraging tools like Windows PowerShell and Server Message Block (SMB) among others. Particularly, it boasts a self-propagation feature driven by predefined automated processes, distinguishing it from ransomware attacks reliant on manual network infiltration. Once an initial host is compromised, LockBit identifies and connects to other vulnerable hosts, spreading the infection via a script without human intervention.
Furthermore, LockBit employs sophisticated techniques to evade detection by endpoint security systems. This combination of autonomous spreading, native tool usage, and deceptive file disguises presented serious challenges to the cybersecurity ecosystem.
Infection Vectors
LockBit, being a notorious RaaS operation, employs a diverse arsenal of infection vectors to infiltrate victim systems. The RaaS model itself attracts various affiliates with their own malware and tools, expanding potential infection vectors. Here’s a breakdown of some common methods they utilize
Precursor Malware
Other strains of malware such as infostealers have evolved to become some of the most relevant vectors of initial access today. While these malware strains were initially developed as credential stealers and banking trojans, they now perform lateral movement and can deploy the final ransomware payload. Additionally, the data acquired by infostealers, such as credentials, are used by ransomware gangs to gain privileged access as they prepare to deploy ransomware.
Social Engineering
Phishing and Spear Phishing: These involve sending deceptive emails containing malicious links or attachments that, when clicked, download LockBit or provide initial access to attackers.
Business Email Compromise (BEC): This targeted attack impersonates legitimate individuals or companies to trick victims into sending sensitive information or making fraudulent payments, potentially giving attackers access to systems.
Exploiting Vulnerabilities
Public-facing Applications: LockBit affiliates scan for and exploit unpatched vulnerabilities in publicly accessible applications like web servers or VPNs to gain initial entry.
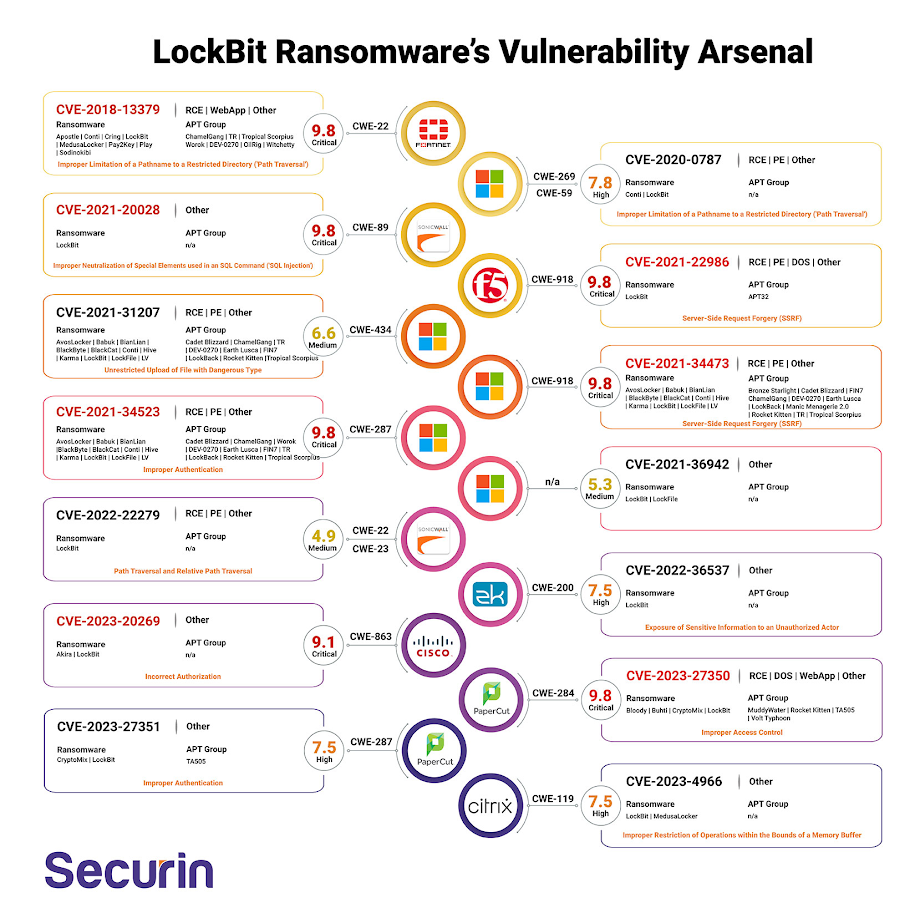
Zero-day Exploits
They might use newly discovered, unpatched vulnerabilities (zero-days) before vendors release fixes, granting them unauthorized access.
Some recent zero-days used by LockBit were:
Cisco ASA: CVE-2023- 20269
Citrix Netscaler “CitrixBleed”: CVE-2023-4966
ProxyShell Exploitation Chain: CVE-2021-34473, CVE-2021-34523, CVE-2021-31207
PaperCut Exploit: CVE-2023-27350
SonicWall SRA: CVE-2022-22279
Other Techniques
Brute-force Attacks: Attackers attempt to guess weak passwords or use automated tools to crack them, allowing unauthorized access to accounts.
Supply Chain Attacks: Compromising trusted software or service providers can give attackers access to their clients’ systems, potentially including LockBit deployment.
Misconfigured Services: Leaving remote desktop protocol (RDP) ports open or using weak configurations creates vulnerability points for attackers to exploit
LockBit Infection Chain
This is a summary of the typical LockBit infection, for detailed technical information you can refer to CISA’s guide.
- Initial Infection: LockBit employs various methods to gain initial access to a victim’s system, as mentioned earlier (phishing, exploiting vulnerabilities, brute-forcing passwords, etc.).
- Privilege Escalation: Once inside, attackers aim to escalate their privileges within the system, granting them broader control and access to critical files and resources.
- Lateral Movement: They may move laterally across the network, compromising additional systems and expanding their foothold.
- Data Exfiltration: In a tactic known as “double extortion,” LockBit often steals sensitive data alongside encryption, increasing pressure on victims to pay the ransom.
- Data Encryption: The core ransomware payload is deployed, encrypting valuable files on the victim’s system, rendering them inaccessible.
- Ransom Demand: A ransom note is displayed, demanding payment in cryptocurrency (often Bitcoin) in exchange for the decryption key and potentially stolen data.
- Pressure Tactics: Attackers may use intimidation tactics like threatening to leak stolen data or permanently delete encrypted files if the ransom isn’t paid.
What We Know About the Current LockBit Takedown
A joint operation by the U.S., U.K., and international partners has disrupted LockBit, dismantling the group’s infrastructure, potentially preventing over $120 million in ransom payments, and offering hope to hundreds of victims with potential data recovery through provided decryption keys.
The coordinated operation seized servers, disrupted online infrastructure, and gained control of the “affiliate panel” used by affiliated cybercriminals, effectively crippling LockBit’s attack capabilities. The joint operation has released decryption keys, potentially enabling hundreds of victims to regain access to their locked data.
Additionally, U.S. authorities indicted two Russian nationals linked to LockBit attacks, with charges detailing their alleged involvement in deploying the ransomware against various targets.
While this operation delivers a significant blow to LockBit, the fight against ransomware persists. Victims can contact the FBI for potential data recovery, and resources are available to help organizations protect themselves from future attacks.
Was LockBit Really Taken Down?
The LockBit takedown has undoubtedly disrupted LockBit’s operations significantly. Seizing servers, infrastructure, and the affiliate panel significantly hinders their ability to launch attacks and extort victims. This operation sends a strong message to other ransomware groups and highlights the international collaboration against cybercrime, potentially deterring future attacks and affiliates’ confidence in Lockbit’s operations took a big hit
Most notoriously, seizing decryption keys provided the authorities with information and tools that offer immediate relief to hundreds of victims, potentially saving them millions in ransom payments and allowing them to regain access to their data.
The full extent of the disruption may take time to reveal. It’s unclear if all major infrastructure was captured, and dormant affiliates might still pose a threat. History suggests that even major takedowns are rarely permanent. As seen with Qakbot, criminal groups rebuild or rebrand, often leveraging existing infrastructure or partnerships. The LockBit team might attempt to resurrect under a different name or through affiliates who weren’t directly impacted. The core developers or affiliates might shift operations to new and more hardened infrastructure, with adapted spread and exploiting techniques or targeting different victim profiles, making it harder for law enforcement to track them.
By the time of publishing, the gang already made available a backup site with all the leaked information and some reports suggest that they sent a communication reassuring their affiliates that the operation is safe.
Key Takeaways
- This operation is a significant win against LockBit, but the fight against ransomware is ongoing.
- Expect LockBit or its successors to adapt and reappear in some form.
- Organizations and individuals need to remain vigilant, practice good cybersecurity hygiene, and report suspicious activity to authorities.
- The Qakbot botnet returned 4 months after a similar operation claimed victory. In this case, the LockBit Ransomware gang was able to maintain business continuity for their illegal operations 4 hours after this takedown, indicating that ransomware actors have already learned and developed strategies for responding to this kind of attention from authorities.
- In our cybersecurity predictions for 2024, we noted that governments needed to learn lessons from the Qakbot exercise to have a meaningful impact on limiting the ransomware epidemic. It does seem that some lessons were learned in that this time, arrests were made. However, the swift response from Lockbit shows that the cybercriminals have also learned.
Recommendations
Enhanced Network Monitoring: Deploy Continuous Compromise Assessment to detect any communication with known Lockbit C2 servers . or any other malicious activity. This real-time monitoring can alert you to potential breaches or malware activity.
Incident Response Planning: Have a robust incident response plan in place. Lumu’s incident management feature can aid in quickly identifying and mitigating threats.
SecOps Enablement: Leverage SecOps capabilities to actively monitor and respond to threats. Lumu’s platform can provide valuable insights for SecOps teams to act upon.
Employee Awareness Training: Educate your staff about the risks of phishing emails, which are a common delivery method for Lockbit Ransomware. Promote vigilance in identifying and reporting suspicious emails.
Regular Updates and Patching: Ensure that all systems are regularly updated and patched to mitigate vulnerabilities that could be exploited by Qakbot.
Threat-Informed Defense: Stay informed about the latest developments in Lockbit’s tactics and techniques. Use this information to inform your cybersecurity strategies and defenses.
Attack Surface Reduction: Minimize exposure by securing public services and implementing rigorous access controls, effectively blocking paths commonly exploited in cyber attacks.
General Ransomware Preparedness: Be sure to institute other standard defenses against ransomware attacks, like backup and recovery planning, network segmentation, and privilege management.
Report LockBit Attacks: If you suspect that you have been targeted by LockBit, report the incident immediately at https://lockbitvictims.ic3.gov
Further Advice: Learn how to protect your systems at StopRansomware.gov
ONION domains
lockbitapt2d73krlbewgv27tquljgxr33xbwwsp6rkyieto7u4ncead[.]onion
lockbitapt2yfbt7lchxejug47kmqvqqxvvjpqkmevv4l3azl3gy6pyd[.]onion
lockbitapt34kvrip6xojylohhxrwsvpzdffgs5z4pbbsywnzsbdguqd[.]onion
lockbitapt5x4zkjbcqmz6frdhecqqgadevyiwqxukksspnlidyvd7qd[.]onion
lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd[.]onion
lockbitapt72iw55njgnqpymggskg5yp75ry7rirtdg4m7i42artsbqd[.]onion
lockbitaptawjl6udhpd323uehekiyatj6ftcxmkwe5sezs4fqgpjpid[.]onion
lockbitaptbdiajqtplcrigzgdjprwugkkut63nbvy2d5r4w2agyekqd[.]onion
lockbitaptc2iq4atewz2ise62q63wfktyrl4qtwuk5qax262kgtzjqd[.]onion
lockbit7z2jwcskxpbokpemdxmltipntwlkmidcll2qirbu7ykg46eyd[.]onion
lockbitsupa7e3b4pkn4mgkgojrl5iqgx24clbzc4xm7i6jeetsia3qd[.]onion
lockbitsupdwon76nzykzblcplixwts4n4zoecugz2bxabtapqvmzqqd[.]onion
lockbitsupn2h6be2cnqpvncyhj4rgmnwn44633hnzzmtxdvjoqlp7yd[.]onion
lockbitsupo7vv5vcl3jxpsdviopwvasljqcstym6efhh6oze7c6xjad[.]onion
lockbitsupq3g62dni2f36snrdb4n5qzqvovbtkt5xffw3draxk6gwqd[.]onion
lockbitsupqfyacidr6upt6nhhyipujvaablubuevxj6xy3frthvr3yd[.]onion
lockbitsupt7nr3fa6e7xyb73lk6bw6rcneqhoyblniiabj4uwvzapqd[.]onion
lockbitsupuhswh4izvoucoxsbnotkmgq6durg7kficg6u33zfvq3oyd[.]onion
lockbitsupxcjntihbmat4rrh7ktowips2qzywh6zer5r3xafhviyhqd[.]onion
Conclusion
While the LockBit takedown marks a significant achievement in the fight against ransomware, it also serves as a reminder of the persistent and evolving threat posed by cybercriminals. Continuous improvement of cybersecurity practices, along with international cooperation and intelligence sharing, remains crucial in mitigating these threats. Every attack and every counterattack contains lessons for the future cybersecurity landscape. To effectively combat ransomware and cybercrime, these lessons must be taken to heart and applied.