Already have an account? Sign in
Sign in
Ransomware is a type of malicious software (malware) designed to provide adversaries with access to sensitive data and block users from that specific data, or an entire computer system. They then hold the data, or access to the system, hostage, and demand a ransom from the victims.
The main objective of these threat actors is to always extract the maximum possible monetary value from the illicit access they have to a network. Ransomware is the most high-risk, high-reward strategy they can employ remotely worldwide. Even the White House released an open letter to all businesses on the escalating threat of ransomware and the need for action.
Many ransomware gangs now also use “double extortion” techniques. In this case, victims are offered two “incentives”: Firstly, agreeing to the extortion payment to regain access to the systems and data they have been locked out of. Additionally, the hackers will return sensitive information that they have already stolen, possibly by agreeing to an additional fee.
The FBI, along with several government agencies in the US, both state and nation wide, advise against paying ransoms to discourage the ransomware cycle. Usually, half of the ransomware victims that pay the ransom get targeted again since cyber criminals know that these companies are willing to cough up the cash.
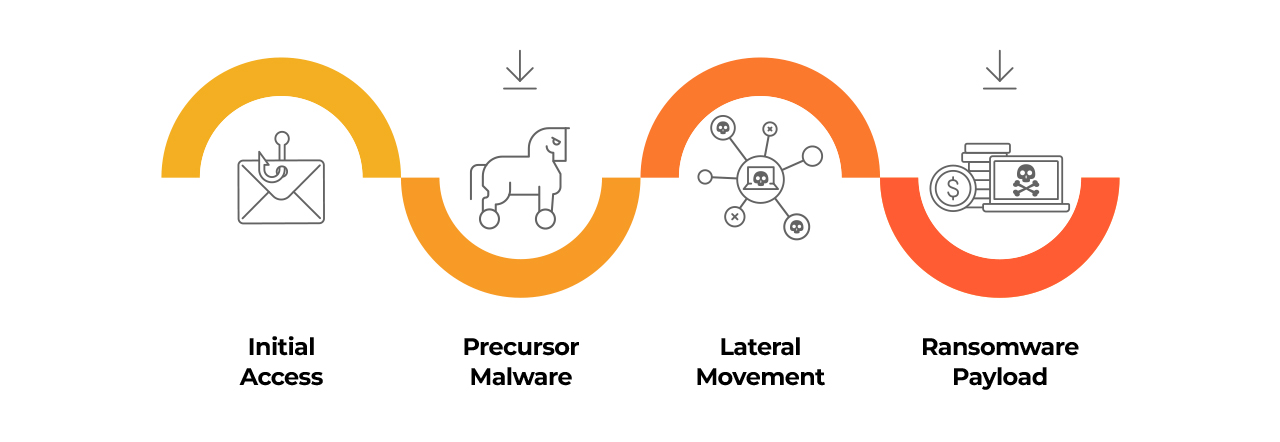
Ransomware doesn’t appear out of thin air. Oftentimes, after gaining initial access, threat actors use other types of malware to spread through the victim’s network. This is referred to as precursor malware.
Ransomware precursor malware is designed to obtain a foothold on a system or network before launching a ransomware attack. Precursor malware is designed to exploit vulnerabilities in your system’s security such as unpatched or outdated software.
Some common malware precursors include:
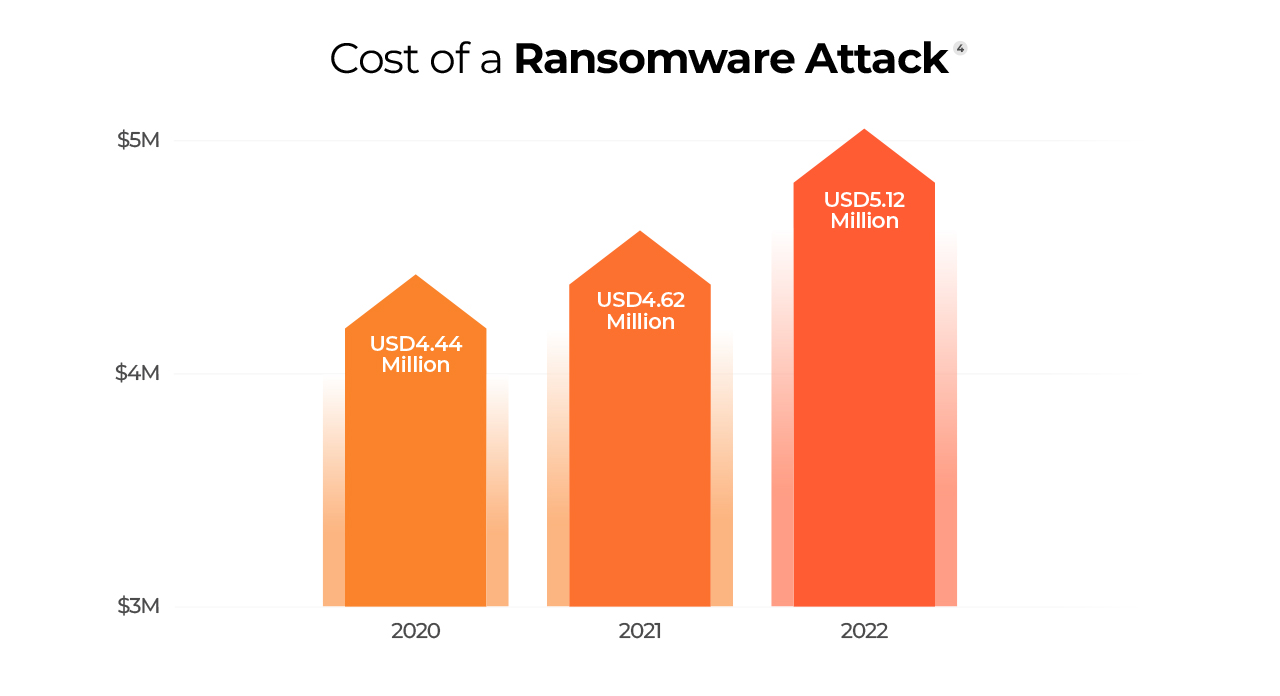
Ransomware attacks can have a significant financial and operational impact on businesses and individuals. In addition to the ransom payment demanded by the attackers, organizations may also face significant downtime, data loss, and harm to their reputation due to an attack.
In extreme cases, some ransomware attacks have a history of forcing companies like Travelex into bankruptcy. Travelex was hit by the infamous Sodinokibi ransomware in 2020 which led to a worldwide temporary shutdown of all its online services and retail branches for two weeks.
Organizations need to consider investing in data recovery and system restoration services, as well as cybersecurity consulting and legal services. According to a study by Cybersecurity Ventures, the global cost of ransomware attacks is expected to reach $265 billion by 2031.
The operational costs of a ransomware attack can also be catastrophic due to day-to-day disruptions and losses. Semiconductor equipment maker, MKS Instruments, suffered a ransomware attack in 2023 that prohibited their ability to process orders, ship products, or provide service, resulting in a $200 million dollar hit in sales.
The aftermath of a ransomware attack often causes reputational damage and loss of customer trust. Would you trust doing business with a company if their operations and services were down for weeks? Regulatory fines and penalties may also apply to businesses if they were found to be in violation of data protection laws.
Preventing ransomware can be simple and straightforward. It often includes steps that are taken for granted but can make a major impact, especially when used as a layered strategy. Here are some common prevention strategies that can help you safeguard your organization’s data:
It’s important to have a general understanding of cybersecurity precautions to lessen the likelihood of a ransomware attack occurring. The following are some cybersecurity best practices you can apply:
It is important to remember that no prevention strategy is 100% foolproof. Be certain to have a solid plan in place for any worst-case scenario if prevention measures fail.
It is important to act quickly since ransomware can spread to other locations in the network. Here are some steps you can take if you suspect that you are infected with ransomware:
Organizations have several options for ransomware prevention tools thanks to the diverse cybersecurity market. Here are some popular tools that infosec professionals highly recommend using :
By using these tools in combination with prevention strategies and best practices, you can create a layer of defense against ransomware and minimize the impact of an attack if one does occur.
Created for organizations that need details on ransomware prevention and response.
It also includes a detailed checklist of tasks to assign to your security team in case of a ransomware attack.
Find out what level of risk your organization is at when it comes to ransomware by taking our free ransomware evaluation quiz.
© Lumu Technologies All rights reserved. | Legal information.