Already have an account? Sign in
Sign in
Save time and money with Lumu’s autonomous model for instant threat detection and automated response.




Put your existing cybersecurity infrastructure to work and designate actions against network threats using your existing tools. Configure real-time incident responses and feed incident data to your SecOps tools.
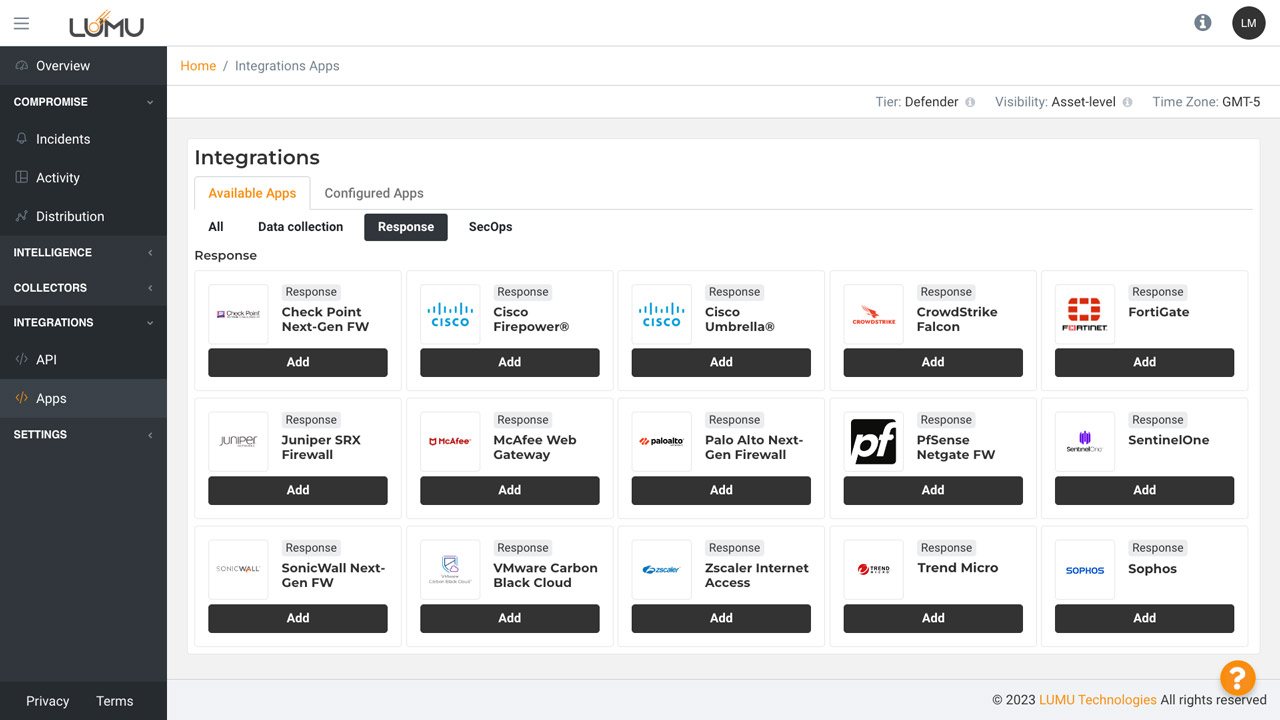
Configure integrations with Lumu’s API
Designate actions against threats with just a few clicks using out-of-the-box integrations.
Select the out-of-the-box integration type.
Click on add to begin configuring your integration with just a few clicks.
Increase efficiency and save time by prioritizing your most critical incidents. This feature provides the ability to filter, search, export, and take action against incidents at scale.
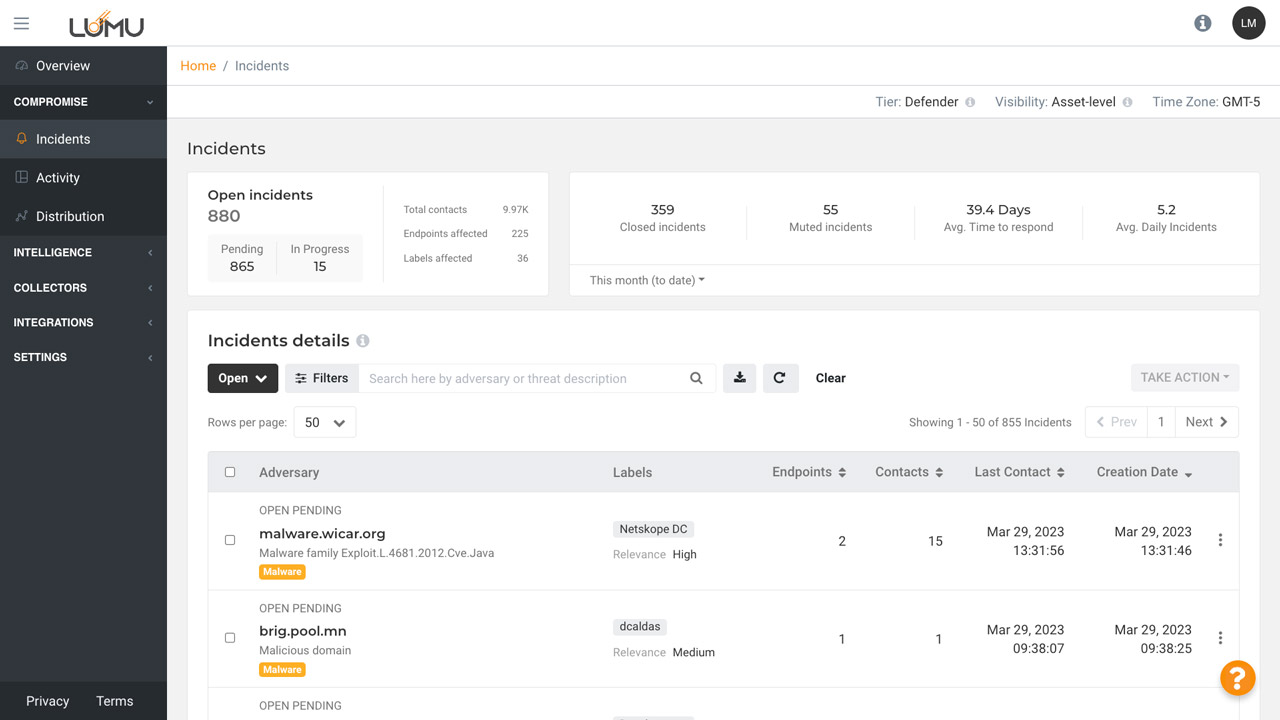
See which incidents are currently open, pending, or in progress.
Number of incidents closed within the selected timeframe below.
Average # of incidents created on a daily basis.
Allows you to select preferred time.
Visualize incidents by their status -open, muted, closed, or all.
Filter incidents based on threat type, labels, contacts and more.
Search for incidents using keywords.
Download incident information based on filters applied.
Take group actions on incidents like closing, muting, or mark pending.
Visualize top attack types impacting your organization with heatmaps to show specific areas of focus. This enables prioritization and shows how attackers are targeting your unique network infrastructure, with the ability to download information.
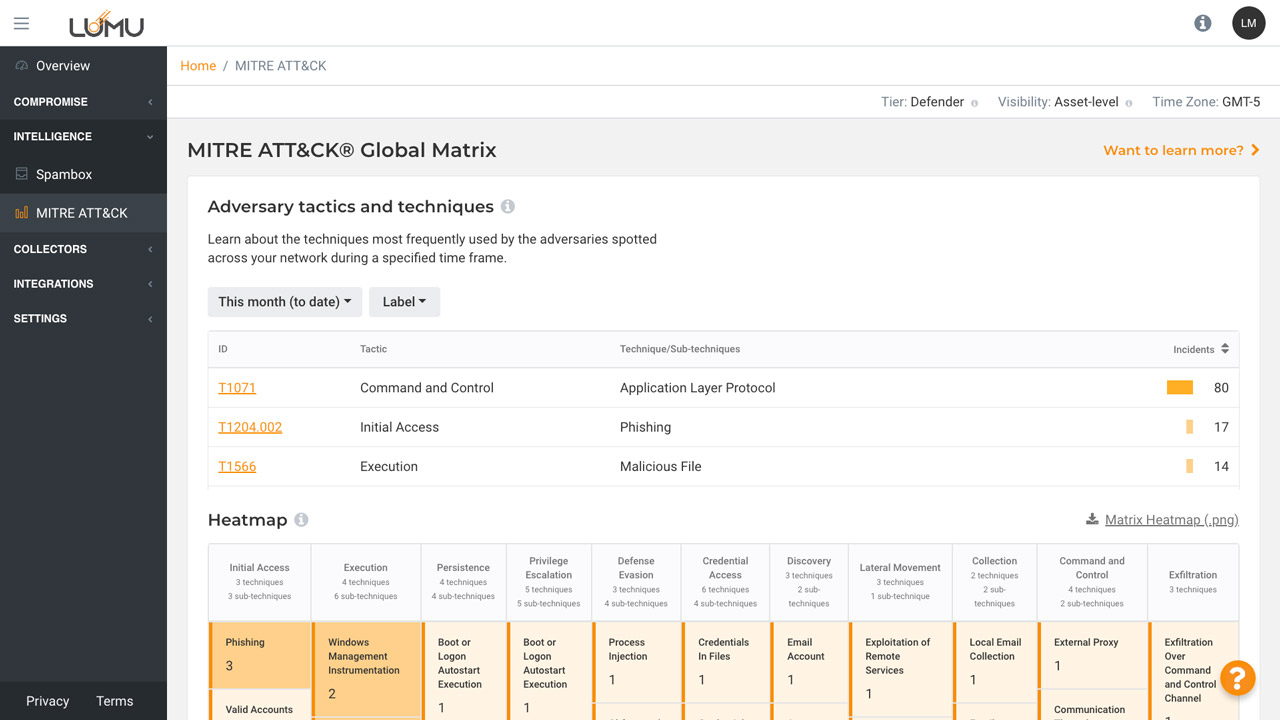
See how attack techniques are most frequently used against your organization.
Filter by labels to prioritize threat types impacting different areas of the business.
Select a timeframe to see the techniques used within a certain period.
See the distribution of techniques within the selected timeframe and prioritize efforts.
Download the heatmap to visualize top attack types and share with others.
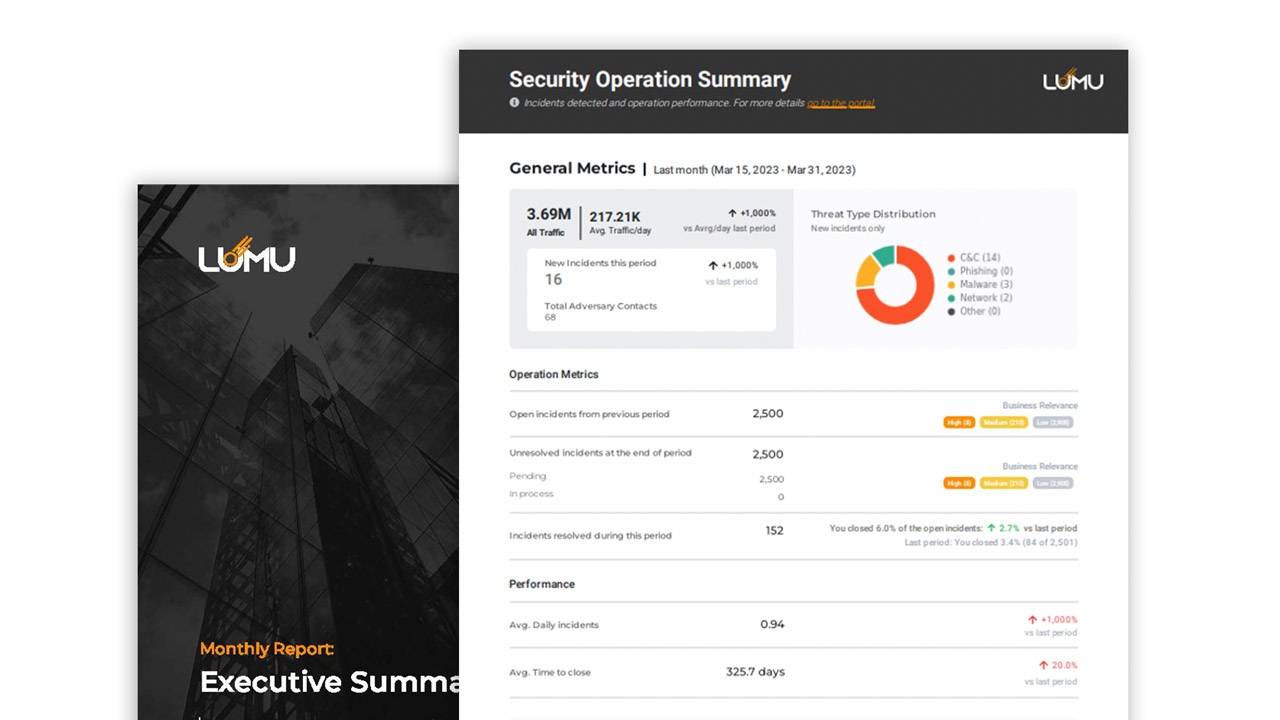
Generate reports to validate malicious activity discovered over a selected period of time and share reports with anyone to show how incidents are being discovered and mitigated. Leverage reports to improve response automation using existing tools.
© Lumu Technologies All rights reserved. | Legal information.