
Advisory Alert: Snowflake Supply Chain Attack
Reading Time: 3 mins Explore the Snowflake supply chain attack, how infostealer malware impacted hundreds of major companies, and essential measures to protect your organization from similar threats
Get the latest cybersecurity articles and insights straight from the experts.

Reading Time: 3 mins Explore the Snowflake supply chain attack, how infostealer malware impacted hundreds of major companies, and essential measures to protect your organization from similar threats

Reading Time: 4 mins Platformization can limit flexibility and innovation. Discover why an open SecOps Platform is essential for cybersecurity

Reading Time: 2 mins This VPN vulnerability highlights a typical risks associated with perimeter defenses, which can allow attackers to access networks. Stay informed and secure your network promptly.
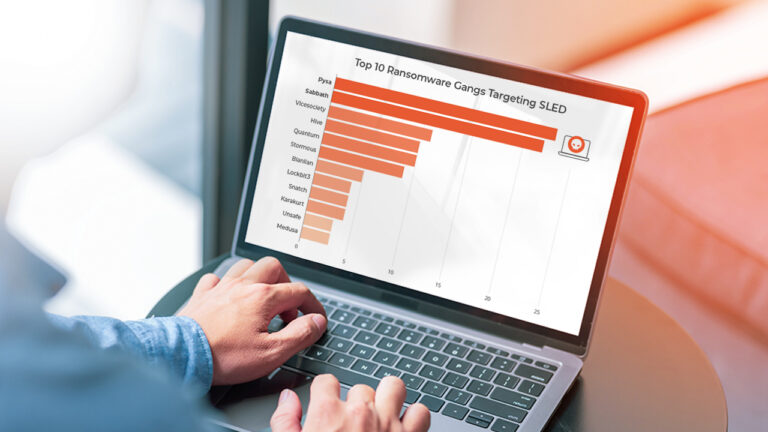
Reading Time: 6 mins Local Government and Education Institutions are under increasing threat from cyber criminals. Explore how these critical sectors can level up their cybersecurity posture.

Reading Time: 4 mins The Palo Alto Networks PAN-OS firewall vulnerability exemplifies critical flaws in traditional perimeter defenses. Understand how Lumu’s detection capabilities safeguard networks.

Reading Time: 2 mins Efficiently confirm and address ConnectWise ScreenConnect vulnerabilities with our guide and user-friendly tool.

Reading Time: 7 mins LockBit takedown news and guidance: arrests made, resilience shown, and future cybersecurity steps.

Reading Time: 7 mins Explore how Infostealers compromise global security, silently stealing data and offering adversaries initial access.

Reading Time: 3 mins Qakbot resurges with new updates, posing a greater cyber threat. Discover how it’s evading defenses in our latest advisory

Reading Time: 3 mins The recently discovered MOVEit vulnerability is an actively exploited zero-day threat, which is leading to significant breaches in large and critical enterprises. Gain insight into the nature of this vulnerability, its exploitation by the CL0P Ransomware Group, who is at risk, and the necessary remedial measures to be taken.

Reading Time: 4 mins This story is based on true events and dives into what happens when initial contact is made with some of the most pervasive strains of

Reading Time: 2 mins Our Threat Intelligence Team has discovered approximately 70,000 instances potentially exposed to a dangerous vulnerability in the 3CX Desktop App currently being exploited by threat actors. Learn how it could impact your company and how to respond in case adversaries leveraged this vulnerability to enter your organization.

Reading Time: 6 mins Clop Ransomware is currently being unleashed in a blitz of attacks against organizations across the globe. To help you stay informed and safeguard your organization, Cristian Torres has prepared a detailed analysis examining this emerging threat.

Reading Time: 8 mins The Manufacturing industry is targeted by ransomware more than any other industry in the USA. Take a look at the motivations and opportunities driving threat actor activity in this critical vertical.

Reading Time: 2 mins There’s a lot of information available about ransomware, but most of what exists focuses on how to prevent ransomware rather than what to do when ransomware hits. Our latest ransomware incident response playbook details comprehensive defense and response strategies against ransomware.
© Lumu Technologies All rights reserved. | Legal information.