Table of Contents
The Local Government and Education sectors have embraced rapid technological advancements, driven by connectivity and AI, with a 2024 budget of $138.9 billion. This surge aims to improve service delivery but also increases cybersecurity risks. Recognizing these threats, the U.S. government designated the education sector as critical infrastructure and established the Education Facilities Subsector Government Coordinating Council (GCC). The GCC enhances cybersecurity by promoting collaboration among federal, state, and local agencies. This advisory outlines the significance of safeguarding sensitive data, the impact of ransomware, and essential strategies for protecting local government and education institutions against cyber threats.
Accelerating Technology Adoption in SLED
Increased inter-connectivity and Artificial Intelligence (AI) propels technological advancements within the State, Local Government, and Education (SLED) sector. According to statistics, the education sector is poised to lead this technological surge, aiming to enhance competitiveness in delivering services to students. Significant allocations have been made for technology spending, with a total budget of $138.9 billion across SLED for 2024. IT services account for $59 billion within this budget, while software products represent $13 billion. Forecasts indicate a notable increase in these figures by 2025, with IT services expected to rise to $61 billion and software products to $14 billion, reflecting the sector’s commitment to continuous innovation and advancement.
However, these new technologies, automation processes, and interconnected systems are giving rise to fresh challenges and risks. Within local government and education institutions, there’s a growing dependence on technology for essential functions, including the storage of sensitive data such as financial records, student information, and research findings. This heavy reliance expands the potential attack surface, providing cybercriminals with greater opportunities for exploitation.
Designation of Education as Critical Infrastructure
In recognition of the growing cyber threats facing educational institutions, the U.S. government has officially designated the education sector as critical infrastructure. This designation underscores the importance of protecting the sensitive data and technological systems used in schools. In response, the Department of Education, in collaboration with the Cybersecurity and Infrastructure Security Agency (CISA), has established the Education Facilities Subsector Government Coordinating Council (GCC). This council aims to enhance cybersecurity resilience across K-12 schools by fostering collaboration between federal, state, and local agencies. Through information sharing and strategic defense measures, the GCC seeks to safeguard educational environments against cyber threats, ensuring the security of student and institutional data. However, this move also implies that schools may encounter increased oversight, regulation, and reporting requirements.
The sensitivity of information held by educational institutions is often underestimated, yet it encompasses a wealth of records that could be exploited in detrimental ways. These records may include details on students with health issues, specific ethnic backgrounds, drug usage reports, and disciplinary records. If such information were to become public, the potential harm to these students could be irreparable.
Impact of Ransomware on Local Government and Education
In 2023 Ransomware groups have achieved an unprecedented milestone by extracting over $1 billion in cryptocurrency payments from their victims. Aditionally, over the past two years, more than a hundred educational institutions have fallen victim to ransomware attacks perpetrated by various criminal groups, and the cost of recovery is estimated at $1.8 million USD. In secondary schools, according to the latest Emisoft report, the number of affected institutions has nearly doubled compared to two years ago, totaling 108.
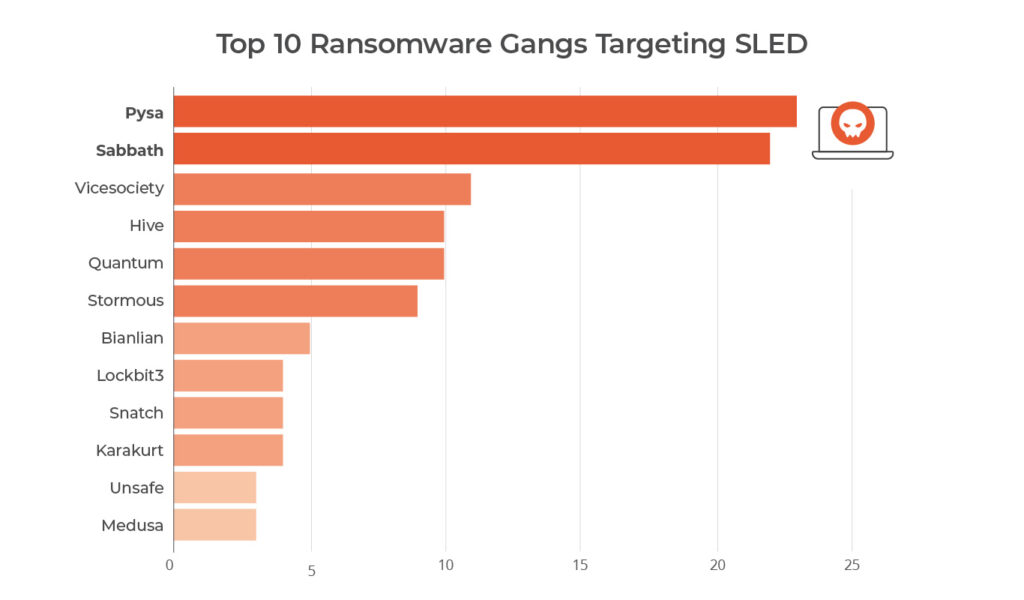
Pysa Ransomware Group
Pysa ransomware emerged as a significant threat in 2023, primarily targeting educational institutions and local government organizations in the U.S. Originally known as Mespinoza, the group began operations in late 2018, producing .locked files. However, in December 2019, they rebranded to Pysa ransomware, changing the file extension to .pysa.
Notably, at least three variants of this ransomware have been detected to date, all characterized by the use of Living-off-the-Land (LotL) techniques with PowerShell, Python, and Bash scripts. Like most ransomware groups, this gang employs phishing as an initial attack vector, along with frequent usage of infostealers and the exploitation of misconfigured and exposed RDP access.
Notable Recent Ransomware Incidents
In 2023, several high-profile attacks targeted educational infrastructure, leaving a significant impact. Among the notable incidents were the following:
- Clark County School District, Nevada (September 2023):
- Over 200,000 students were affected, resulting in the compromise of profiles and sensitive information.
- Los Angeles Unified School District (LAUSD) (October 2023):
- More than 2,000 student records were exposed on the dark web, including COVID-19 certificates.
- Anoka-Hennepin Public Schools, Minnesota (May 2023):
- Sensitive data, particularly related to allegations of sexual violence, was unlawfully disclosed.
- The ransom demanded amounted to a staggering $1 million USD.
More than 670,000 students were affected in the last year and the tendency is on the rise. These incidents underscore the pressing need for enhanced cybersecurity measures within the education sector to safeguard student data and maintain trust in educational institutions.
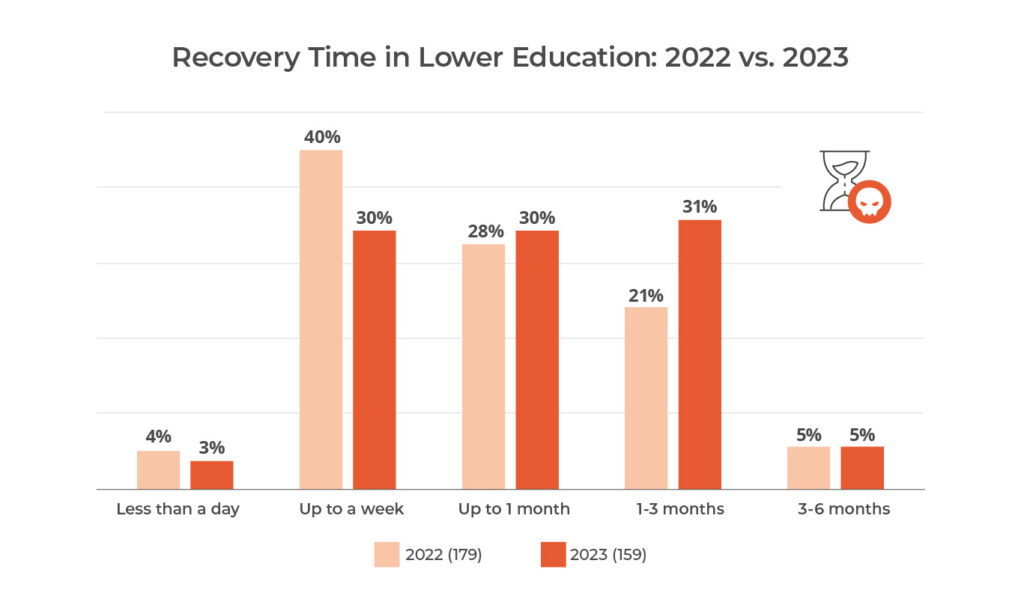
Education Sector Vulnerability & Recovery Time
The Education sector stands as one of the most vulnerable to the impacts of ransomware attacks, experiencing recovery times slower than in previous years. The increasing complexity of these attacks has posed significant challenges in maintaining operational continuity.
Common Attack Vectors and Techniques
However, sophisticated cyberattacks are comprised of elaborate chains of multiple steps, often involving a combination of automated and manual processes. Regardless of the level of automation at each step, criminals exploit some vulnerabilities in defense systems. Typically, initial access is facilitated through smaller artifacts like infostealers or Remote Access Trojans (RATs), commonly distributed via email or phishing attempts. The emergence of Initial Access Brokers (IAB) has streamlined these initial steps, emphasizing the significance of every threat in the cybersecurity landscape.
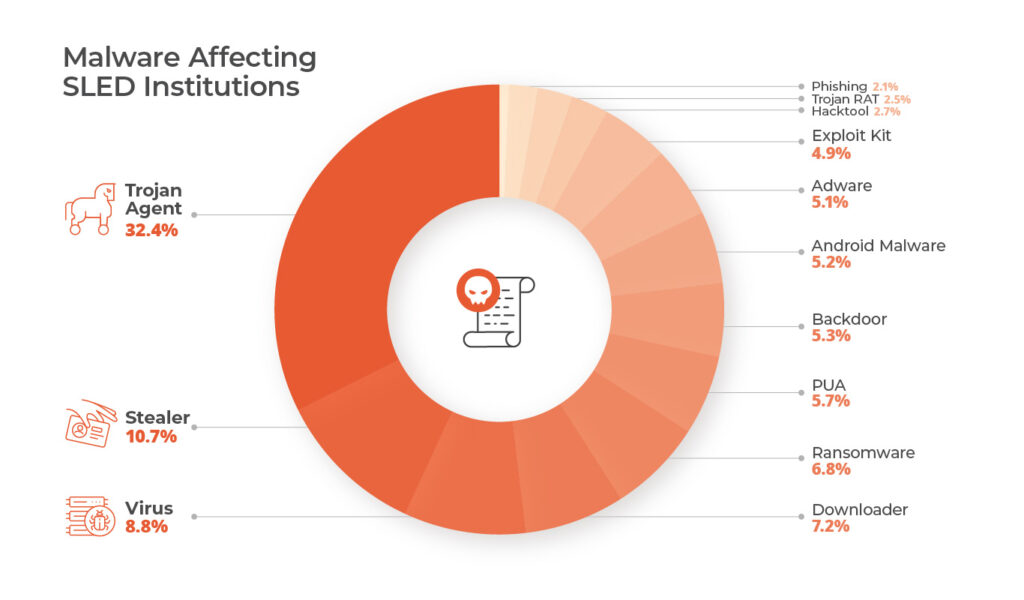
The Achilles heel of this attack chain is that at some point the attacker must use the network to communicate with the attack process, in 2023 Lumu detected an interesting variety of malware in SLED sector, highlighting the high presence of stealers, trojans, RATs and related with initial access:
Malware Affecting SLED Institutions
MITRE ATT&CK Matrix™ for SLED Ransomware
Considering the most important ransomware gangs that have targeted the SLED sector, the MITRE ATT&CK Matrix provides a detailed overview of the common techniques through the cyber kill chain employed by these attackers. This information is invaluable for fortifying defense systems and being prepared to detect these types of adversaries. The following table shows the adversarial TTPs (Tools Techniques and Procedures) that most commonly affect SLED organizations, as identified by Lumu.
TTP | TTP Number | *Heat |
Data Encrypted for Impact | T1486 | 4 |
Exfiltration | TA0010 | 4 |
Phishing | T1566 | 3 |
Inhibit System Recovery | T1490 | 3 |
Valid Accounts | T1078 | 3 |
External Remote Services | T1133 | 2 |
Windows Management Instrumentation | T1047 | 2 |
Command and Scripting Interpreter | T1059 | 2 |
Deobfuscate/ Decode Files or Information | T1140 | 2 |
Scheduled Task/Job: Scheduled Task | T1053.005 | 2 |
Create or Modify System Process: Windows Service | T1543.003 | 2 |
Masquerading | T1036.003 | 2 |
Impair Defenses | T1562 | 2 |
OS Credential Dumping | T1003 | 2 |
Remote Services: Remote Desktop Protocol | T1021.001 | 2 |
Service Stop | T1489 | 2 |
Exfiltration Over C2 Channel | T1041 | 2 |
Indicator Removal on Host: File Deletion | T1070.004 | 2 |
System Information Discovery | T1082 | 2 |
*Heat represents how frequently this TTP is used by ransomware gangs that most commonly target SLED sectors.
Cybersecurity Recommendations for SLED
Embrace Automation: SLED organizations often don’t have the same resources available as other entities that have to operate cybersecurity. To compensate, technology needs to step up by automatically detecting and responding to threats, without overwhelming cybersecurity staff.
Develop Network Visibility: Every successful attack manages to bypass one or more cybersecurity defenses like firewalls, email security, or endpoint detection and response. It’s therefore critical to deploy additional measures to find threats that have already bypassed those other defenses in real time.
General Ransomware Preparedness: Deploy standard defenses against ransomware attacks, like backup and recovery planning, network segmentation, and privilege management.
Reduce your attack surface and external threats by investigating possible compromises in credentials and accounts related to your company, infostealers are the most common method used by attackers to gain initial access in ransomware attack chains.
CONCLUSIONS
The constant evolution of interconnected technologies and information processes, specifically designed for the government and education sectors has made them one of the most attractive targets for ransomware groups. These groups capitalize on the sector’s comparatively weaker security systems to orchestrate attacks. Considering the prolonged recovery times, these attacks result in substantial operational disruptions. Consequently, many institutions are compelled to pay substantial sums to decrypt their data.
Local government and education institutions must recognize the critical sensitivity of student and operational data and take prompt measures to monitor their systems and networks. It’s imperative to prepare institutions to modernize the continuous monitoring of systems and networks and streamline incident response actions, ensuring agility and effectiveness in addressing potential cybersecurity threats.
Learn more about the cybersecurity challenges SLED organizations face here.