Table of Contents
EDR Evasion is a tactic widely employed by threat actors to bypass some of the most common endpoint defenses deployed by organizations. A recent study found that nearly all EDR solutions are vulnerable to at least one EDR evasion technique. In this blog, we’ll dive into 5 of the most common, newest, and threatening EDR evasion techniques as well as how you can counter them.
What Is an EDR?
Gartner defines Endpoint Detection and Response (EDR) as “solutions that record and store endpoint-system-level behaviors, use various data analytics techniques to detect suspicious system behavior, provide contextual information, block malicious activity, and provide remediation suggestions to restore affected systems”.
While the EDR landscape is evolving, with vendors expanding their offerings to include Extended Detection and Response (XDR) and Endpoint Protection Platforms (EPP) with new features and a broader scope of coverage, it is possible that these solutions do not provide complete coverage of the attack surface. and it may not be able to keep up with the fast pace of threats and techniques we see today.
Despite the potential for AI and machine learning technologies to improve EDR capabilities, many EDR solutions still rely on rule-based behavior finding patterns and correlations. It’s important to note that EDR technology typically does not involve the analysis of network data or metadata, this means that if a threat actor can evade the set of detection rules, the effectiveness of the EDR is immediately compromised, leaving the endpoint vulnerable to attack. Furthermore, without an effective alert system in place, the blue team may not be able to respond quickly enough to prevent damage or loss of data.
According to a recent study by the University of Pireaus and IMSI, of 26 endpoint detection and response (EDR) solutions and 5 Endpoint Protection Platforms (EPPs)—some of the most prominent solutions on the market today—94% were found to be vulnerable to at least one common evasion technique. These results highlight the significant risk of compromise for customers.
Some of the most common and useful techniques used by real malware to evade EDR detection are described below. Some of them have been active for several years but remain current and functional with the help of minor variations.
EDR Evasion Techniques
CPL (Control Panel) Side-Loading
CPL files were originally created to be associated with the Control Panel in the Microsoft Windows operating system. They are used to represent and provide quick access to various tools available in the Control Panel, making it easier to manage internal tools.
Malicious actors have recently been using .cpl files to hide specific malicious software and execute it instead of legitimate system tools. Having in mind that security EDR solutions focus on identifying and blocking malicious executable files, attackers can bypass these measures by using legitimate .cpl. This technique is known as “CPL side-loading” or “CPL Hijacking”.
While the use of this technique may seem recent, it’s been documented since 2017 when security researchers discovered that the FIN7 cybercrime group was using it to attack financial institutions. Since then, numerous attacks have been identified that employ CPL side-loading as part of the cyber kill chain.
The CPL side-loading technique is relatively easy to perform, as there are several tools available, such as CPLResourceRunner and ScareCrow, that allow for the creation of a malicious embedded CPL file. This seemingly simple technique can be combined with other techniques, such as the use of memory-mapped files (MMFs) to store shellcode, in order to prevent other EDR functionalities from detecting anomalous behavior.
It’s possible to create a malicious .cpl payload and embed various programs using CPLResourceRunner by following these simple steps:
- Create a Payload using “RAW” fully-staged (S) (x86) format in Cobalt Strike
- Run ConvertShellcode.py on the beacon.bin file to convert the beacon file in a useful shellcode.txt payload.
- To encode the contents of the shellcode.txt file in Base64 format and include it in the resource file, use the following command:
cat shellcode.txt |sed ‘s/[, ]//g; s/0x//g;’ |tr -d ‘\n’ |xxd -p -r |gzip -c |base64 > b64shellcode.txt
- Copy the encoded file b64shellcode.txt into Resources.txt in the same folder.
- Compile to x86 and copy CPLResourceRunner.dll to newmalicious.cpl
The study mentioned earlier found that 48% of EDR and EPP solutions tested are not able to detect or block the execution of this technique immediately, which increases the risk of compromise.
DLL Side-Loading
This technique is used by attackers to run malicious code by deceiving an application into loading a malicious DLL (Dynamic Link Library) file instead of a genuine one. In other words, the attackers replace a legitimate DLL with their malicious one and make the application load it, which results in the execution of the attacker’s code on the target system.
A DLL, or Dynamic Link Library, is a type of software library that contains code and data which can be shared and used by multiple programs simultaneously. It works like a shared toolset that different programs can use to accomplish certain tasks.
For example, in Windows Comdlg32 DLL is a commonly used library that provides a functionality for creating dialog boxes. This means that any program that needs to create a dialog box can use the code and data stored in the Comdlg32 DLL, rather than having to create the dialog box from scratch.
Side-loading is a technique similar to DLL Search Order Hijacking, where an attacker hijacks the DLL a program loads. While side-loading contains hijacking, attackers don’t just add the malicious DLL to the search order of a program and wait for the victim application to be launched. Instead, attackers directly side-load their payloads by placing and running their malicious code through a legitimate application. That is to say, they exploit a trusted application to execute their malicious code, rather than waiting for the victim application to call it.
To perform a successful DLL side-load, an attacker must deceive a Windows application into loading a malicious DLL file exploiting the known DLL search order of Microsoft applications, which is a relatively straightforward process.
The default search order for Microsoft application DLLs varies depending on whether DLL safe search mode is enabled or disabled. When safe DLL search is enabled, the application will search for the required DLL files in the following order,
- The directory where it was loaded,
- The system directory,
- The 16-bit system directory,
- The Windows directory,
- The current directory,
- Any directory listed in the PATH Environmental variable.
When DLL safe search mode is disabled, the search order is different, with the application first looking for:
- The directory where it was loaded
- The current directory,
- The system directory,
- The 16-bit directory
- Any directory listed in the PATH environment variable.
When safe DLL search mode is enabled, the current directory where a user executes a program is given less priority in the search order for DLL files. However, when safe search is disabled, the current directory is slightly higher in the hierarchy, making it more likely for an application to search for a DLL file in that directory.
Attackers can take advantage of this default search order by placing a malicious DLL file in a directory that an application will search before it finds the legitimate DLL. In effect they are tricking the application into loading the malicious DLL instead of the legitimate one, leading to a DLL hijacking attack.
The study uses AQUARMOURY, specifically the Brownie module, which is a software tool created to perform DLL hijacking or side-loading and weaponizing DLL preloading attacks. It works by examining the code of a valid application to detect which DLL files it uses during runtime. AQUARMOURY then modifies the Import Address Table (IAT) of the application to direct it to a malicious DLL file instead of the legitimate DLL.
When the application is launched, it loads the malicious DLL file instead of the legitimate one, granting attackers access to execute their code within the application. As a result, the application is compromised, and the malicious code is hidden and legitimated by a trusted application.
The study shows that approximately 68% of all EDR and EPP technologies are vulnerable to this kind of attack.
Code Injection
Code injection is a method employed by attackers to introduce malicious code into a legitimate application or process in order to bypass detection by EDR or EPP systems. This method of executing arbitrary code in the address space of another live process can mask its presence under a legitimate process, making it harder for security products to detect.
CreateRemoteThread() and QueueUserAPC() are two commonly used Windows API functions for code injection. The latter was used in the mentioned study, which involves queuing a user-mode APC to another thread. An APC is a function executed in the context of the target thread when it enters an alertable state. This technique is also referred to as “Early Bird”.
While new code injection techniques have emerged, older ones such as process hollowing remain a popular choice for attackers and are still successful even today. In this technique the attacker must create a new process in a suspended state, for this task he uses the CreateProcess() function of the Windows API. The process then “Hollows out” itself by deallocating the memory pages of the legitimate binary from the new process’s address space using the ZwUnmapViewOfSection() or NtUnmapViewOfSection Windows API functions. This leaves the new process with an empty address space.
In addition, the attacker allocates memory in the address space of the new process using the Windows API function VirtualAllocEx(). After, the malicious code is copied into memory allocated by the Windows API function WriteProcessMemory(). The attacker then modifies the execution context of the new process by setting the entry point to the address of the malicious code.
Finally, the attacker resumes execution of the new process using the ResumeThread() function of the Windows API. The new process will now execute the malicious code instead of the legitimate code.
One of the most recent techniques for code injection is “Atomic Bombing”, this technique takes advantage of the Windows mechanism for interprocess communication (IPC) called “atoms.” An atom is a unique identifier for a string or data that is stored in a global table called an atom table. Each atom has a unique 16-bit identifier, which is used to retrieve the corresponding string or data value.
The attacker then sends an Asynchronous Procedure Call (APC) to the APC queue of a target process thread using the NtQueueApcThread() API. When APC runs, it triggers the target process to call the GlobalGetAtomName function, which retrieves the malicious code from the global atomic table and inserts it into the target process’s memory.
While this technique was an innovative way to write malicious code into the memory space of another process without using WriteProcessMemory, the inserted code is still not executable. An additional step is needed to make the code executable, which involves using another APC call to run Return-Oriented Programming (ROP) and convert the memory region of the code into readable, writable, executable (RWX) memory. Only after this step is the malicious code ready to run.
The study mentioned above used the “Early Bird” technique for code injection and the result shows that approximately 65% of EDR and EPP technologies allow the execution of this method without blocking it.
Userland API Hooking
API hooking is a technique used by many software including security systems such as EDRs or EPPs to try to detect changes while monitoring a process execution. The action of detecting such changes to an application by intercepting API calls between two other applications is called ‘hooking’. To ‘hook to an application’, Windows provides tools for developers to intercept events, messages, and calls between APIs in the Operating System, which are called “hooks”.
However, a technique that permits intercepting applications is not outside of the attacker’s radar and they can also use it to intercept API calls and modify them for their malicious purposes. In this sense, userland hooking is a method employed to intercept function calls that are made by applications to system libraries or APIs in the user space. By redirecting function calls to their own code, attackers can modify the behavior of an application.
To perform API hooking evasion, the first step for the attacker is to identify the API functions that the EDR system hooks, commonly CreateProcess() or LoadLibrary(). They then modify the IAT of the target application to replace the addresses of these API functions with the address of their own malicious code.
To evade the EDR detection in the IAT modification process, attackers may employ additional techniques such as process hollowing or reflexive DLL injection. These techniques enable the attacker to inject malicious code into the target application’s memory space without creating a new process or writing to disk.
ChatGPT
Recently, cybersecurity researchers developed a proof of concept using ChatGPT and created a polymorphic keylogger on the fly, dynamically modifying the code without using any kind of command and control infrastructure, this PoC was called BlackMamba.
According to the own platform, “ChatGPT is a large language model trained by OpenAI, based on the GPT-3.5 architecture”, although OpenAI recently released GPT-4.0
The ultimate goal for the author was to create code according to two main concepts. The first removes any malicious command and control infrastructure and replaces it with intelligent automation that forwards any linked data to the attacker via a benign and trusted communication channel. The second concept is to use AI to create generative code with the ability to synthesize new malware variants, changing the code so that it can evade the detection algorithms of the EDRs.
To conclude, the author’s proof-of-concept “BlackMamba” demonstrates that language learning models can be leveraged to dynamically generate polymorphic keylogger code, which makes it challenging for EDR solutions to detect and intervene. Furthermore, the use of a trusted communication channel, such as MS Teams, to exfiltrate the captured data adds another layer of complexity for security systems to detect the attack.
This scenario presents new challenges for the cybersecurity industry.
The Difference Between EDR and Lumu, and How Lumu Helps
It is evident that there is no perfect cybersecurity system and the data shows how technologies that intend to monitor the behavior of devices are bypassed with increasingly advanced EDR evasion methods. Lumu’s goal is to focus on the Continuous Compromise Assessment™ model that shows how these types of evasions could end up in security compromises. Additionally, Lumu provides network and security administrators with the technical tools to understand the compromise so they can act and mitigate it as quickly as possible.
Lumu helps enterprises to build a continuous loop that improves their overall cybersecurity environment. Lumu’s advanced technology does not just rely on machine behavior that could be intentionally emulated or mimicked by attackers in the ways that we’ve seen above. Lumu takes advantage of the information sent over the network that is analyzed by modern models that can determine the compromise level and alert the blue teams.
Different views such as the Compromise Radar show organizations how the attackers act in their network and the number of potentially affected endpoints.
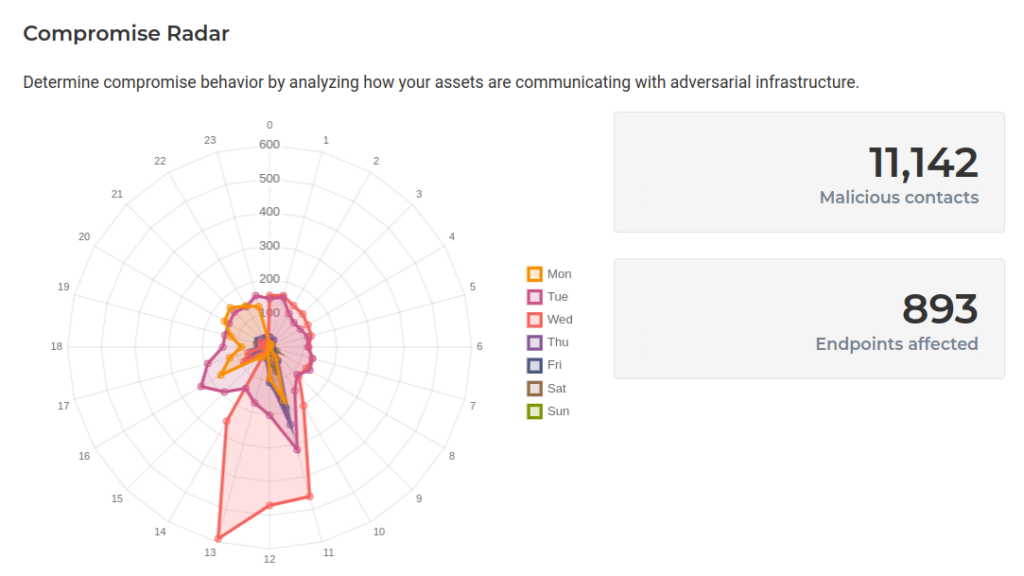
But Lumu’s job starts at the first step in the cyber kill chain. Lumu’s Email system shows how adversary campaigns affect business operations and alert the network administrator to focus on customers or specific users who could be the victims of an initial attack to try to gain access to the network through this vector. So, in addition to showing the level of compromise, it also helps prevent the escalation of attacks.
The increasingly advanced EDR Evasion techniques used by attackers require an advanced system that can detect their actions on the network and alert on time, providing enough context and information to response teams to act on the fly and mitigate the compromise before significant damage can be done.
Learn more about how Lumu detects active threats affecting organizations’ networks here.