Table of Contents
Over the last year, there has been a marked increase in activity on dark web forums that sell access to compromised networks. A new report released by Lumu titled “Flashcard Report: Monetization of Cybercrime” shows how this increase is more sinister than it appears at first glance.
The Credential-selling Business is Booming
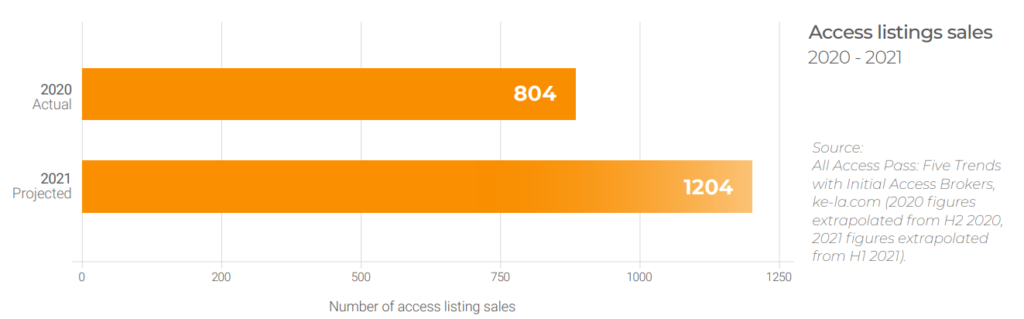
Individual sales of access to compromised networks have increased by 50% in 2021. What’s more, the market has diversified a lot. A couple of years ago, these markets were primarily just selling credit card details; now you can purchase access to remote desktop connections, mail servers, and much more. The already-compromised networks of businesses representing every country and industry can be bought and sold.
Your Network Means Money
Cybercriminals will monetize access to your network however they can, depending on their skills and resources. Among the techniques for turning your network into elicit gains, the easiest is to deploy a cryptomining botnet. But as the cybercriminal digs deeper into your network, they will try to develop an attack that can be more lucrative for them and more damaging for the victim, such as a ransomware attack. If they are not able to develop such an attack themselves, then the access can be sold to another APT group that does have the skills and resources to do so.
Lumu’s Take on the Monetization of Cybercrime
We’ve seen at Lumu that ransomware attacks never happen in isolation. There is always another type of threat like malware or a botnet that shows up first. The result is that there is no such thing as a ‘minor threat’. One type of compromise can easily turn into another. As Lumu CEO Ricardo Villadiego points out in his article on DarkReading, cryptomining botnets are the ‘canary in the mine’: an early indication that something is very wrong.
We invite you to download the full report “Flashcard Report: Monetization of Cybercrime” for a more detailed look into this phenomenon.