Table of Contents
With all of the hype around new tools and acronyms across the cybersecurity market, it can give organizations a sense of incompletion when it comes to their security strategy. However, the reality is that these sophisticated tools often aren’t always as effective as they need to be. Cybersecurity Analysts are struggling to deal with these demanding security tools and deliver the protection that companies need. We are still seeing large organizations that have access to all of the latest tools and resources being breached.
This happens for a variety of reasons, but two of the biggest contributing factors are the time it takes to implement the solutions, and their limited integration capabilities. Many of these technologies require a great deal of time and money to configure according to a company’s needs and security teams don’t always have the bandwidth to follow through fully. When you combine that with a solution that is limited in its ability to integrate with other tools, you end up with a very siloed cybersecurity operation.
Cybersecurity doesn’t have to be complicated and you don’t always need the next new thing.
Selecting the right solution(s) to complement your strategy can seem like an overwhelming process, but there are a few rules of thumb that can point you in the right direction. We like to call these Lumu’s 7 Habits of Highly Effective Cybersecurity Analysts. They are a guideline to what you should consider when developing your cybersecurity practice.
1. Enable Threat Hunting
A cohesive cybersecurity strategy requires well-developed threat hunting abilities. However, cybersecurity teams are stretched thin and as Allie Mellen, Forrester Senior Analyst, mentioned during the Illumination Summit “You think about a typical detection engineering function it requires not only a detection engineer but also a threat intel manager, and a threat hunter to be able to find more threats and that combination that is expensive that is hard to find.”
Since resources are limited, it’s important to find the technology that has automated threat hunting capabilities. It should be able to automatically identify and report threats, providing all of the details and context needed to respond in real time, or for future forensic analysis/attack prevention. This will provide your team with the visibility they need to respond with speed and precision.
2. Advocate for Tools that Empower Your Team
We often forget that the tools need people to operate them. A habit of highly effective security teams is focused on selecting tools that empower our teams to operate cybersecurity better each and every day. When deciding which tools work best for you there are a few things to consider:
- Does this tool provide the visibility we need?
- Do these tools work with my existing solutions?
- Should have automation capabilities.
- They should be easy to use.
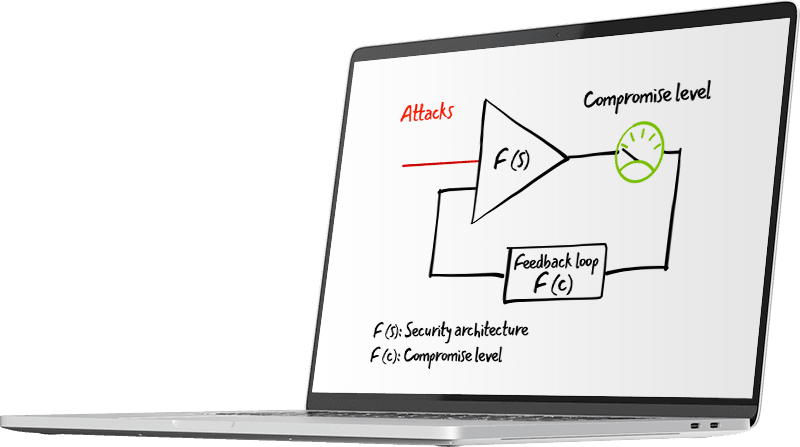
3. Close the Feedback Loop for Better Decision Making
Implementing the technology is not enough, you have to enable communication between tools. We implement layers of cybersecurity to avoid being compromised but without communication between these layers, there are only silos.
Once the feedback loop is closed, you can focus on other things that matter across your organization through the power of the visibility the system provides.
4. Visibility Is the Only Cure for Anxiety
When it comes to securing your network, ignorance is not bliss. In fact, we should not worry about what we see, we should be worried about what we are not seeing. Visibility is the single thing that will make that feeling of uncertainty better. When you know what is happening you can better react and prevent it from getting worse or happening again. It’s the only way to continue improving your security posture.
5. Mitigation & Remediation: Don’t Skip Either
This is a very important habit of effective security teams – they mitigate and remediate to ensure the adversary’s access is terminated from the core. Mitigation and remediation are two different things and understanding that difference can be the hallmark of a high performance cybersecurity security pro.
Mitigation is only the first step: Mitigation should be used as a way to gain time but not as an end itself. Depending on your cyber defense, blocking, isolating, or shutting down may be enough to prevent damage and give your security team time to eliminate the threat.
Remediation is where you go back to the specific device and understand what it’s attempting to do, this is the only way to eliminate the residual effects of the compromise itself.
6. Curate Your Vendor Ecosystem
It’s key to be aware that supply chain is presenting a big problem for organizations. We live in a connected world and we should treat it as such. It’s important to become more proactive with your vendor ecosystem. Get on the same page as vendors when it comes to cybersecurity.
When you’re selecting a vendor, ask questions about their cybersecurity practice. Ask them if they have any network security tools implemented, or make it a requirement that your vendors must have network level visibility across their assets to minimize the risk to your own business.
7. Make Cybersecurity Mainstream
Cybersecurity is such an important topic and it’s crucial that all employees understand the risk and understand how to contain it or report anything they may come across. Cybersecurity needs to be a mainstream topic inside the company, not just a concern for Cybersecurity Analysts. Everyone should be involved in some type of training. Everyone must understand the risks involved and the potential loss of time, money, and customer trust that may occur as a result of neglecting cybersecurity.
Conclusion
At Lumu, we believe these 7 habits are fundamental to developing a well-rounded cybersecurity operation while also making a positive impact on the daily lives of Cybersecurity Analysts. Organizations, regardless of their size or industry, should be able to operate cybersecurity proficiently and with confidence. That’s why finding the right solution is the first step.
Understanding the value you may get from a new solution is important when making purchasing decisions. This is why we recently released the Lumu ROI calculator. This tool helps organizations get an idea of the time and money they can save using Lumu. The 8-question assessment is designed to enable informed decision-making when it comes to finding the right solution. You can access the Lumu ROI Calculator here.
This happens for a variety of reasons, but two of the biggest contributing factors are the time it takes to implement these solutions, and their limited integration capabilities. Many of these technologies require a great deal of time and money to configure according to a company’s needs and Cybersecurity Analysts don’t always have the bandwidth to follow through fully. When you combine that with a solution that is limited in its ability to integrate with other tools, you end up with a very siloed cybersecurity operation.