Table of Contents
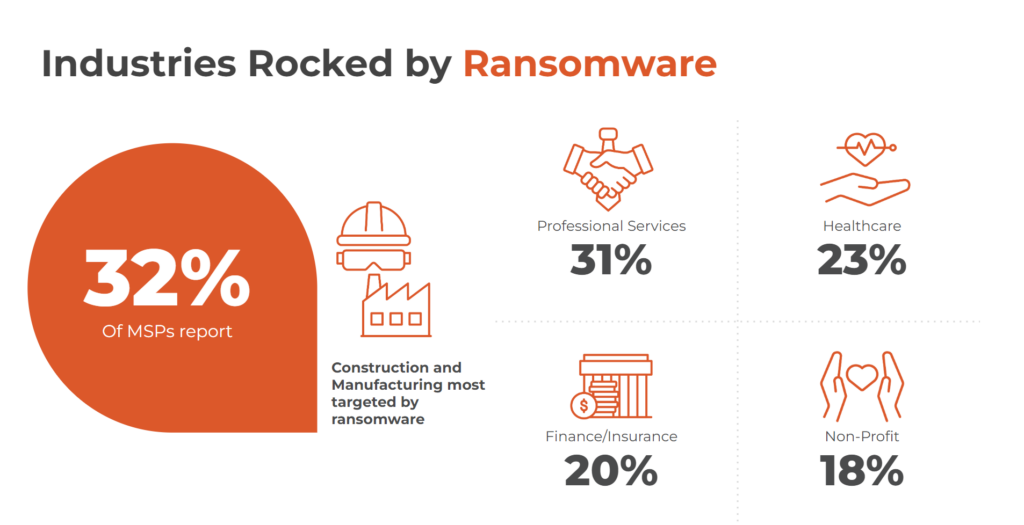
The Manufacturing industry is targeted by ransomware more than any other industry. You might be forgiven for thinking the financial or professional services industry would hold that unfortunate distinction. However, industrial systems provide threat actors with critical opportunities and the incentive to strike manufacturers.
Why is the Manufacturing Industry a Cause for Concern?
What makes this so worrying to the public, is that the manufacturing industry includes many industries defined by CISA as critical:
- Primary Metals. Including steel mills, aluminum producers, and nonferrous metal production, this sub sector includes 5,500 companies in the USA.
- Machinery Manufacturing. Including engine, turbine, transmission equipment, mining, and construction manufacturers, this sub sector includes 3,982 companies in the USA
- Electrical Equipment, Appliance & Component Manufacturing. Including electric motor, transformer, and generator manufacturers.
- Transportation equipment. Including vehicle, ship, aerospace, locomotive, and railroad manufacturers.
Other critical industries face some of the same challenges as those faced by manufacturers, including the chemicals, defense, food, energy, and transportation industries.
The colonial pipeline attack of 2021 serves as an example of the damage that can be done by attacking these critical industries. But with a little imagination, we can see the further catastrophes that hackers could cause in this sphere: derailed trains, blackouts, and tainted water supplies.
Why Is the Manufacturing Industry So Vulnerable to Ransomware?

Industrial Control Systems and SCADA
In the first couple of months of 2023, CISA released 72 advisories on newly discovered ICS vulnerabilities.
The manufacturing industry relies heavily on industrial control systems (ICS). These systems are used to monitor and control industrial processes by connecting them to operational technology. Supervisory control and data acquisition (SCADA) is a type of ICS that interfaces with operators for high-level management.
In aging manufacturing sectors, many ICSs were designed during a time when security wasn’t considered a primary concern. Therefore these legacy systems don’t include modern security features such as strong authentication features or zero trust principles.
ICS and SCADA systems connect to dispersed equipment and corporate networks through connections that might expose the system to outside threat actors while also providing an opportunity for lateral movement. Ironically, it’s not the complexity of these systems that causes problems, but rather their simplicity. ICS and SCADA tend to cover simple analog tasks like opening and closing valves. Since the tasks are so simple, the processors used to control them are simple, small, and cheap. Security is none of those 3 things. That’s why security is usually performed by isolating these systems (and their ports) and strictly controlling how they can communicate.
One of the most famous early malware attacks targeting ICS was when Stuxnet was used to target SCADA systems used in Iran’s uranium enrichment program.
Operational Technology (OT) Vulnerabilities
Operational Technology refers to any system or device that connects to the internet. An example is a programmable logic controller used for opening and closing valves, a sensor, or an actuator. OT offers some similar vulnerabilities to ICS, if at a smaller scale.
They also include internet connections and offer limited protections. It can also be difficult to deploy endpoint monitoring or protection to this type of machinery.
There have been multiple cases where OT was used as the entry point for attacks that eventually led to ransomware incidents. In 2021 Hexion, a US-based chemical manufacturer, suffered a ransomware attack that affected its operations worldwide. The attack is believed to have started with a vulnerability in the company’s OT systems.
Lack of Cybersecurity Maturity & Visibility
The manufacturing sector is inherently less mature in its security infrastructure and sophistication. Their security departments have historically been understaffed. As a result, they typically do not have the network visibility in place to detect and respond to malicious activity before it escalates to a ransomware attack. A study by Davos showed that 48% of manufacturers surveyed scored a “C” or below for security resilience.
Complex Supply Chains
Manufacturing companies are often part of complex supply chains, making them vulnerable to attacks that originate from suppliers or third-party vendors.
Supply chains are important because they can affect the manufacturer in two ways.
- They can be the source of a breach. A security system is only as strong as its weakest link. Your supply chain needs to take security as seriously as you do. It needs to be a team effort.
- If they are attacked and can no longer supply you with the materials you need to manufacture your product it has the same effect on production as if you were attacked directly. If you can’t get a critical part you can’t produce your product.
NotPetya is an example of a supply chain attack that spread to manufacturers. The attack originated from a Ukrainian tax software supplier and spread to their customers, including several shipping and manufacturing companies.
Threat Actors Are Motivated
Incentivized to Cause Damage
Because of the critical nature of manufacturing to the global economy, malicious actors are often motivated to attack companies in this sector. The victim will be extra incentivized to pay the ransom when the repercussions could be devastating.
Additionally, manufacturing companies play a critical role in providing goods and services that are essential to the public and public safety. Disruption of these services can cause serious public relations damage.
Large Payoffs
Threat actors like to target companies that are likely to pay large sums for the restoration of their systems. Manufacturers tend to have the means to pay and rely heavily on their systems
Intellectual Property
Manufacturers are in possession of valuable intellectual property that could be stolen or held ransom. Proprietary designs, processes, and trade secrets could be of great interest to nation-state actors and companies could be willing to pay ransom to keep these assets.
Recently, Lockbit threatened to release thousands of SpaceX’s blueprints acquired through a breach at one of their parts manufacturers.
How Manufacturers Need to Fight Against Ransomware
Manufacturers should follow general cybersecurity best practices to mitigate the risks they face from ransomware, including maintaining backups, segmenting networks, and training employees on cyber threats. Preparation and good cyber hygiene are critical. However, for manufacturers, there are some specific precautions that need to be taken.
Secure OT/ICS Blindspots
Many manufacturing operations have already started bringing together their information technology (IT) and operational technology (OT) ecosystems in a bid to improve operational efficiency and customer service. This has resulted in new security challenges. A Deloitte analysis report says that “there are a number of areas where people, process, and technology overlap between the IT and OT ecosystems―areas where respective strategies need to be in sync. The reality of these technologies and how they are used, however, is often markedly different.”
OT expenditure and acquisitions are generally decided by factory floor point persons with minimal involvement from corporate IT departments or cybersecurity teams. This creates a weakness in the cyber defense posture of organizations with multiple technologies employed and some that do not go through the scrutiny and monitoring of the IT department.
Moreover, the use of IoT devices in manufacturing is blurring the separation between information technology and operational technology. It makes it inevitable to confront the need to establish better security policies and measures that can help prevent the emergence of new security flaws, some of which take time to be discovered amid the hustle and bustle in the manufacturing business setting.
Develop Network Visibility
Visibility is the cure to cybersecurity anxiety. In manufacturing more so than any other industry, cybersecurity operators worry about the things they can’t see, not the things they do see.
Network visibility is essential to combat the spread of malware that aims to make use of ICS and OT for initial access and lateral movement. Since these systems often include zero-day vulnerabilities, it’s essential to detect threat actors in near-real time. Additionally, since it is often difficult to deploy endpoint-specific tools to these systems, the network is the ultimate source of truth as to whether it is in contact with the adversary. All remote attacks have two things in common. They come in over the network and they originated from somewhere.
Monitoring network metadata is critical to determining the source and blocking those attacks.
Keep Software Up to Date
As we’ve seen, the amount of vulnerabilities present in the manufacturing sector, especially for ICS, is staggering. Be sure to stay up to date on the latest ICS advisories issued by CISA and ensure that vulnerable software is promptly updated.
Sophisticated cyber crime syndicates reverse engineer vulnerabilities when they are released and seek to exploit them to introduce back doors that can be exploited even after the original vulnerability is closed with patching. Therefore time is of the essence with patching. A prime example of this was with the Microsoft Exchange Hafnium exploit, where threat actors installed a back door using what was called a ChinaChopper PowerShell to give access after patching.
Pay Attention to the Supply Chain
It is key to be aware that the supply chain is presenting a big problem for manufacturers. We live in a connected world and we should treat it as such.
Manufacturing is a generational industry where most started long before even the internet was invented. Security at that point was strictly physical security and the brilliance of the system was focused on the mechanical engineering space. The need for interconnectivity and connections to the intra- and internet was required for business efficiency and cost-cutting not initially for actually manufacturing the product.
I believe this mindset contributed to the lag in acceptance or perceived need for secure systems. A combination of the automation of those processes and the effectiveness of Ransomware has totally changed the calculus in the manufacturing industry. What once was not considered a core competency in the business is now the critical backbone to the business and the manufacturing industry finds itself in a position of playing catch up both financially and in sophistication in the cyber security space.
Like driving a car, safety doesn’t only depend on one driver, but all drivers. You need to do everything right, but so do your vendors. We need to be a lot more proactive. Get on the same page as vendors. Ask them to implement some network detection and response program, or make it a requirement to have network-level visibility across their assets to minimize the risk to your own business.
Conclusion
Inherent Cyber Security immaturity compounded by security blind spots in ICS and SCADA systems for both the manufacturer and their supply chain has created a profitable and easily executed environment for the threat actors. If the security level and network visibility (you can’t hit what you can’t see) don’t change rapidly the trend will undoubtedly continue.
At Lumu, we recently released a freely available ransomware response playbook and checklist that you can incorporate into your procedures. Ensure that your ransomware preparedness is aligned with the latest developments in cybersecurity and the threat landscape.