
Advisory Alert: CrowdStrike Outage – What We Know
Reading Time: 3 mins Learn about the recent CrowdStrike outage affecting Microsoft devices, its impact, recovery steps, and how Lumu can help ensure continued network security.

Reading Time: 3 mins Learn about the recent CrowdStrike outage affecting Microsoft devices, its impact, recovery steps, and how Lumu can help ensure continued network security.
Reading Time: 3 mins Learn how Lumu helps MSPs meet CIS compliance with real-time malware detection, network defense, and automated incident response.
Reading Time: 4 mins Essential cybersecurity tips to safeguard K-12 schools during the back-to-school season.
Reading Time: 3 mins Explore the Snowflake supply chain attack, how infostealer malware impacted hundreds of major companies, and essential measures to protect your organization from similar threats
Get the latest cybersecurity articles and insights straight from the experts.

Reading Time: 3 mins ‘Dr. Zero Trust’ Chase Cunningham looks at Zero Trust, network visibility’s importance, and the Forrester Wave™: Network Analysis and Visibility Q2 2023

Reading Time: 5 mins Lumu’s threat intelligence team has identified a new Advanced Persistent Threat (APT) actor named ‘Copode 1.0’, leveraging the LockBit Black code leaks for cyberattacks. This emerging threat underlines the need for stringent security practices and Lumu’s real-time monitoring offers an efficient response to such evolving challenges.

Reading Time: 3 mins Lumu has been named a leader in Forrester Research’s latest report, The Forrester Wave™: Network Analysis and Visibility Q2 2023. Lumu Founder and CEO Ricardo Villadiego reflects on the key takeaways from this report.

Reading Time: 3 mins The recently discovered MOVEit vulnerability is an actively exploited zero-day threat, which is leading to significant breaches in large and critical enterprises. Gain insight into the nature of this vulnerability, its exploitation by the CL0P Ransomware Group, who is at risk, and the necessary remedial measures to be taken.

Reading Time: 8 mins Managed Security Service Providers (MSSPs) have become pivotal allies for businesses, providing expert services and robust technological defenses. MSSPs must understand that they are not infallible and that challenges in their growth and operational model can lead to potential gaps in security coverage.

Reading Time: 4 mins This story is based on true events and dives into what happens when initial contact is made with some of the most pervasive strains of

Reading Time: 4 mins RSAC 2023 brought the cybersecurity world together in San Francisco. While there is a general consensus that a paradigm shift is needed in cybersecurity, it is clear that we would be stronger still if there were consensus around what that paradigm shift needs to look like.
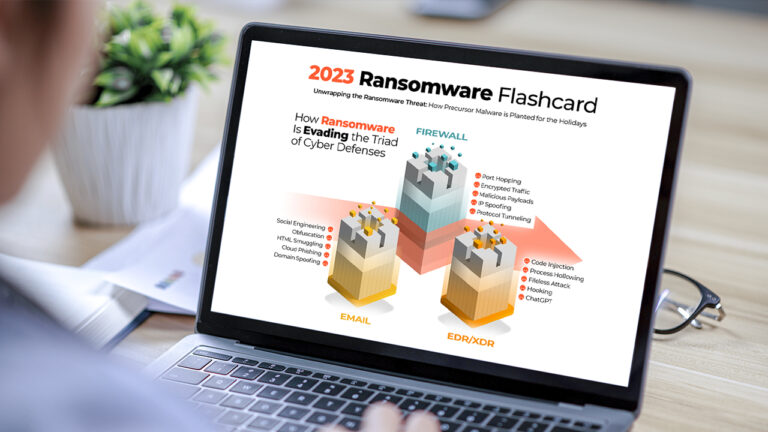
Reading Time: 3 mins Explore the key insights and trends from our 2023 Ransomware Infographic Flashcard. Learn about how hackers are evading defenses, the precursor malware they use, and ransomware’s devastating impact.

Reading Time: 11 mins EDR Evasion includes a suite of techniques that hackers use to elude endpoint defenses. Discover how hackers evade Endpoint Detection and Response (EDR) systems using various techniques. Learn about the common tactics used by cyber attackers to bypass endpoint defenses and how to better protect against these stealthy attacks.

Reading Time: 2 mins Our Threat Intelligence Team has discovered approximately 70,000 instances potentially exposed to a dangerous vulnerability in the 3CX Desktop App currently being exploited by threat actors. Learn how it could impact your company and how to respond in case adversaries leveraged this vulnerability to enter your organization.

Reading Time: 6 mins Clop Ransomware is currently being unleashed in a blitz of attacks against organizations across the globe. To help you stay informed and safeguard your organization, Cristian Torres has prepared a detailed analysis examining this emerging threat.

Reading Time: 8 mins The Manufacturing industry is targeted by ransomware more than any other industry in the USA. Take a look at the motivations and opportunities driving threat actor activity in this critical vertical.

Reading Time: 2 mins There’s a lot of information available about ransomware, but most of what exists focuses on how to prevent ransomware rather than what to do when ransomware hits. Our latest ransomware incident response playbook details comprehensive defense and response strategies against ransomware.

Reading Time: 2 mins We surveyed 213 U.S. cybersecurity executives on their priorities for the new year. Here’s what their responses tell us about how cybersecurity is evolving amid the recession.
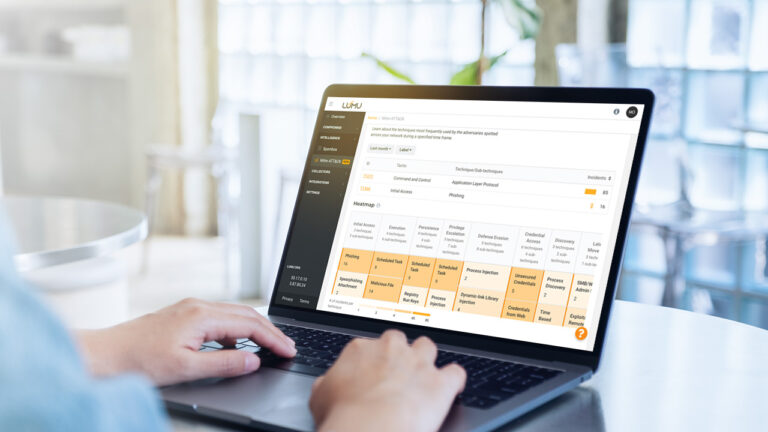
Reading Time: 6 mins Threat-informed defense is a strategic approach to risk-based cybersecurity that even smaller organizations can get up and running easily.
© Lumu Technologies All rights reserved. | Legal information.