
Advisory Alert: CrowdStrike Outage – What We Know
Reading Time: 3 mins Learn about the recent CrowdStrike outage affecting Microsoft devices, its impact, recovery steps, and how Lumu can help ensure continued network security.

Reading Time: 3 mins Learn about the recent CrowdStrike outage affecting Microsoft devices, its impact, recovery steps, and how Lumu can help ensure continued network security.
Reading Time: 3 mins Learn how Lumu helps MSPs meet CIS compliance with real-time malware detection, network defense, and automated incident response.
Reading Time: 4 mins Essential cybersecurity tips to safeguard K-12 schools during the back-to-school season.
Reading Time: 3 mins Explore the Snowflake supply chain attack, how infostealer malware impacted hundreds of major companies, and essential measures to protect your organization from similar threats
Get the latest cybersecurity articles and insights straight from the experts.

Reading Time: 5 mins Uncover key tactics for navigating SLED cybersecurity challenges, focusing on budget-friendly solutions, advanced threat detection, and automated response.

Reading Time: 8 mins Protect your business from digital risks with cyber insurance, covering data breaches, cyberattacks, and recovery costs.

Reading Time: 3 mins Qakbot resurges with new updates, posing a greater cyber threat. Discover how it’s evading defenses in our latest advisory

Reading Time: 4 mins Discover Lumu’s 2023 MSP breakthroughs: Improved threat detection, incident management, and more.

Reading Time: 4 mins 2023 at Lumu: Pioneering advancements in AI-driven cybersecurity solutions and partnerships, enhancing incident management and operational efficiency.

Reading Time: 2 mins Dr. Chase Cunningham discusses the critical need for state and local governments to secure against ransomware, ensuring essential services.

Reading Time: 4 mins Exploring 2024 Cybersecurity Trends: How mature AI and automation are key to developing sustainable and resilient security strategies.
Reading Time: 3 mins Introducing Lumu for MSPs Lite, a free, AI-driven cybersecurity solution for Managed Service Providers, democratizing advanced threat detection.

Reading Time: 3 mins Alert: Severe Cisco IOS XE Web UI vulnerability risks full system control. Immediate action needed for users with HTTP/HTTPS Server enabled.
Reading Time: 5 mins Explore Online vs Transfer Learning in Cybersecurity: Unpacking Lumu’s adaptive AI use for proactive threat defense and staying ahead of risks.

Reading Time: 3 mins Lumu secures $30M Series B led by Forgepoint Capital, boosting cybersecurity innovation and enhancing real-time threat management.

Reading Time: 3 mins Choosing the right cybersecurity solution is pivotal in today’s threat landscape. Our buyer’s guide zeroes in on cybersecurity integrations, offering key questions to ask vendors about API availability, out-of-the-box solutions, and technical support.
Reading Time: 5 mins Collective Defense already plays a key role in shoring up the cyberdefenses of key industries. Alongside AI, it can do even more for cybersecurity practices.

Reading Time: 4 mins The GigaOm Radar Report for Network Detection and Response (NDR) has just been released and we are pleased to announce that Lumu has been named as a Leader and an Outperformer.
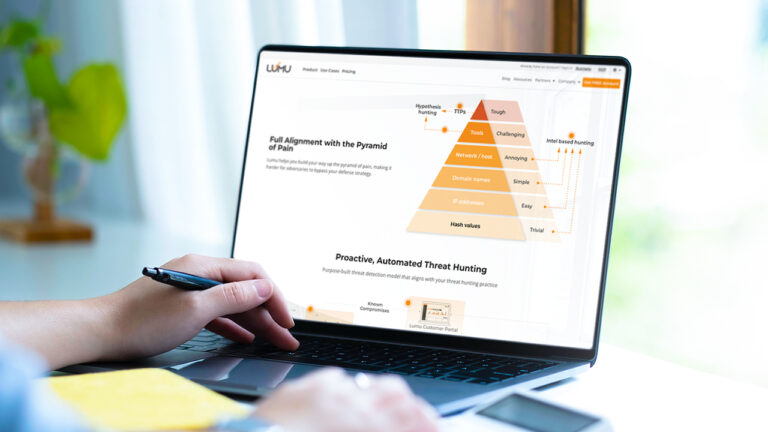
Reading Time: 4 mins Threat hunting in cybersecurity can be a challenging practice. Learn how Lumu helps you build your way up the pyramid of pain and make your cybersecurity posture more difficult for threat actors to target.
© Lumu Technologies All rights reserved. | Legal information.