Table of Contents
Lumu’s threat intelligence team has recently discovered a new threat actor operating in the Americas. This actor self-identified as ‘Copode 1.0’ could emerge as a significant concern within the cybersecurity landscape. Copode is using variations of the LockBit Black code leaks, originally leaked in September 2022 and advanced techniques for pivoting, lateral movement, and maintaining persistence. The adoption of this code signifies a potential alignment with the tactics, techniques, and procedures (TTPs) associated with the LockBit ransomware family.
The Origins of Copode 1.0: Lockbit and Beyond
The observed behavior of the ransomware aligns closely with the characteristics exhibited by the “Black variation” of LockBit or “LockBit 3.0”. Following the completion of the encryption process, the attacker leaves a ransom note in a .txt file containing instructions for data recovery. The note follows the structure commonly associated with LockBit but prominently identifies the ransomware variant as ‘Copode 1.0’. Additionally, the note includes the following notable variations:
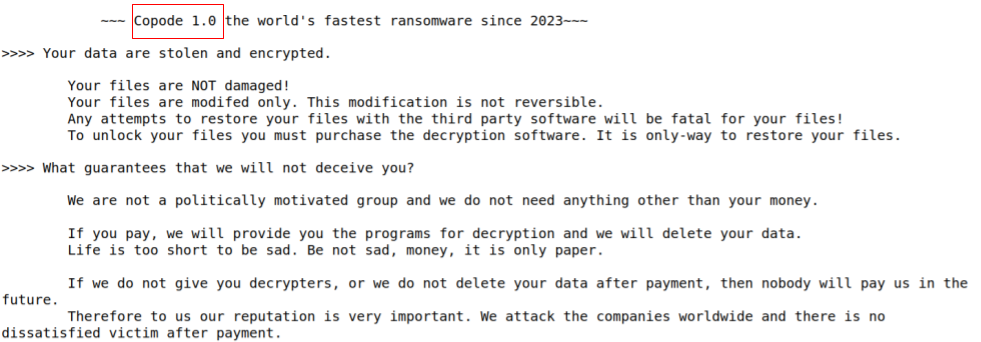
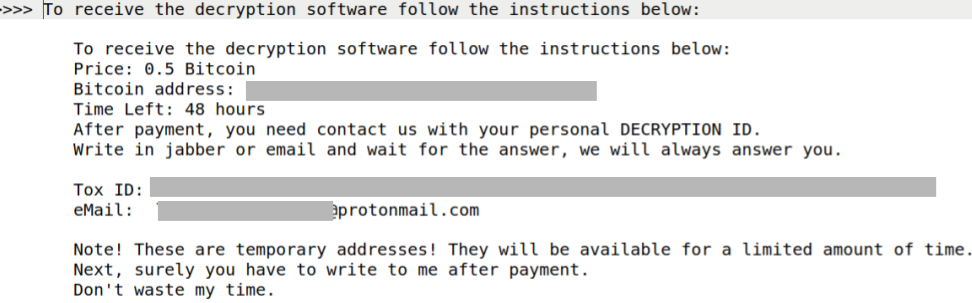
- Absence of .onion Site: Unlike typical practices associated with LockBit, there is no reference to any .onion site for managing the payment process. Instead, it only provides a ProntonMail address for communication after the payment.
- Reduced Extortion Amount: The attackers demand a lower ransom payment compared to the commonly observed price points associated with LockBit. This modified approach may be aimed at incentivizing victims to comply with the payment demands.
- No Mention of Data Leak: The ransom note does not make any mention of the possibility of information leakage at least using the “official” channel of LockBit, nor does it highlight the potential consequences of non-compliance. This omission deviates from the usual strategy employed by LockBit threat actors.
While the cyber kill chain behavior remains consistent with the Black variant, what particularly drew attention from this group was the novel technique employed for compromise and persistence within the victim’s network. Additionally the wallpaper message maintains the original LockBit Black variant code:
Extensive information about the Traditional Black variation can be found in a security blog post by VMware. This article delves into the compromise and persistence techniques employed by this specific variant “Copode 1.0”, providing valuable insights into its operations and characteristics.
Similar to many new ransomware variants, this actor primarily focuses on identifying vulnerable services within the attack surface of potential victims. They exploit various factors such as system obsolescence, unpatched vulnerabilities, misconfigurations, or even leverage zero-day exploits. By meticulously scanning for these weaknesses, the actor seeks to find entry points that can be exploited to gain unauthorized access and launch their ransomware attacks.
Exploiting Vulnerable Services: The Role of GLPI
During the analysis, we found that the GLPI service had been compromised. GLPI is an open-source technology-based asset management solution widely employed for managing IT infrastructure. Additionally, some companies expose the GLPI service to facilitate connectivity and management of roaming devices. In 2022, this service exhibited several vulnerabilities in older versions, including CVE-2022-35947 and CVE-2022-35914.
These vulnerabilities were identified as critical with a severity score of 9.8. The vulnerabilities enabled attackers to execute arbitrary code (RCE) on insecure servers, potentially leading to unauthorized access and compromise of sensitive information. Active exploits and PoC are available to exploit these vulnerabilities. To solve these vulnerabilities, the service provider announced and released patches in October of the previous year.
Additionally to complete this “perfect storm” GLPI requires a generic user with some specific privileges present in every device where the application is installed. This user account is crucial for extracting system data effectively.
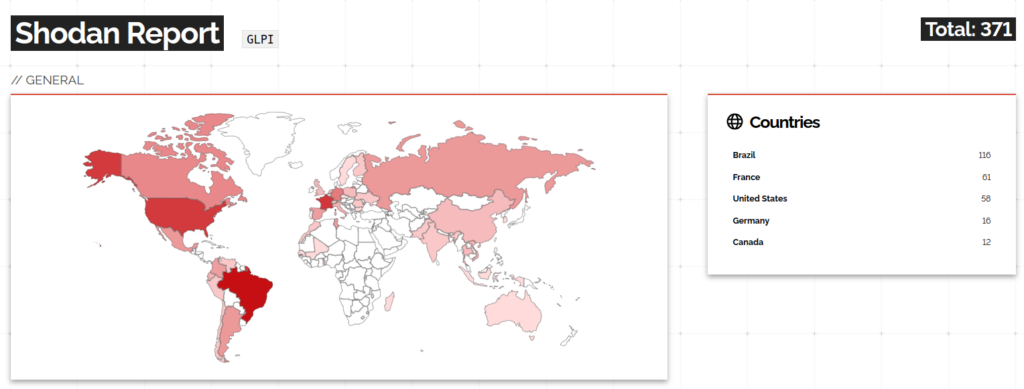
Based on the findings from the Shodan Report, a significant number of companies, at least 371 in total, have exposed this service to the public (version not verified). Most of these exposed instances are observed in Brazil, France, and the United States.
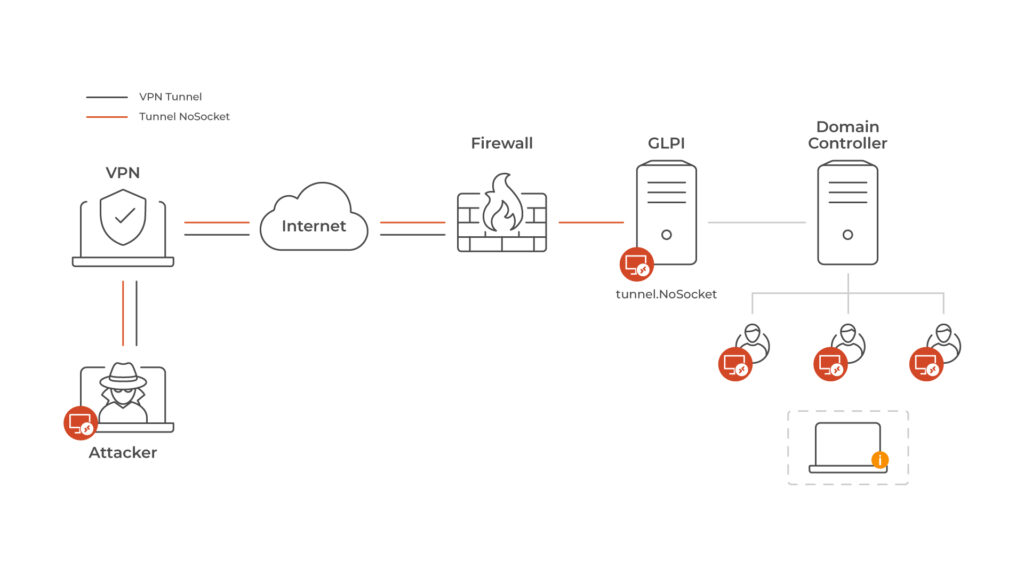
Evading Detection: Establishing a Tunnel
After successfully compromising the victim’s machine and acquiring user privileges, the attacker proceeds to infiltrate the GLPI application by inserting a PHP file in order to create a No Socket proxy via webshell. The code observed exhibits striking similarities to the code available in the related Regeorch GitHub repository “tunnel.nosocket.php”. This file is renamed like a valid service used by GLPI to prevent arousing suspicion.
This technique employed by malicious actors serves as a pivoting method to establish a hidden tunnel within the compromised system. By utilizing existing connections through the firewall and encapsulating the real protocol into another less suspicious, typically, a tunnel no socket utilizes protocols or mechanisms that are allowed through network defenses, such as HTTP or DNS, the attacker can evade monitoring mechanisms and hide suspicious traffic. The creation of such tunnels enables the attacker to maintain persistence, expand their reach within the victim’s network, and potentially conduct further malicious activities undetected
To establish the connection, the attacker uses a script provided by the author ‘reGeorgSocksProxy.py’. The script is configured by the attacker with the URL of the tunnel connection “tunnel.nosocket.php” and the local port in the attacker’s machine.
Python reGeorgSocksProxy.py -u http://victimsdomain.com/GLPI/tunnel.nosocket_renamed.php -p xxxx
Once the tunnel is set up, the attacker employs proxychains tool to articulate the attack redirecting their network traffic through intermediary servers (the victim’s machine in this case) thereby hiding the source of the traffic and bypassing certain network restrictions.
How Copode 1.0 ‘Camouflages’ and Maintains Persistence
In order to add an extra layer of anonymity, the adversary utilizes multiple commercial VPN services to occult their actions. As a result, the direct connections observed to the identified vulnerable paths can be attributed to the VPN infrastructure employed by the attacker. This deliberate use of VPNs helps mask their true identity and location, making it more challenging to trace their activities back to their original source. This behavior has been detected in other recent ransomware campaigns. At this point, the connection has at least 3 layers of security to try to hide their activity.
By utilizing this configuration, the attacker gains the ability to execute commands on their own machine and subsequently propagate throughout the victim’s network enabling a transparent lateral movement. The attacker employs powerful tools such as Mimikatz and Cobalt Strike to assume control of the domain controller. They initiate the final encryption phase through the compromised DC by establishing cascading RDP connections.
The threat actor employs the ‘living off the Land’ technique to execute various routines for network discovery and scanning. To facilitate these activities, they leverage legitimate software licensed by SoftPerfect called Network Scanner, along with other commonly utilized tools listed in the LOLBAS (Living Off The Land Binaries And Scripts) project. This technique allows the threat actor to camouflage their malicious actions within legitimate software, making it more difficult to detect their presence during reconnaissance and scanning operations.
Indicators of Compromise (IoCs): Tracing Copode 1.0
IOC | Background |
194.32.120.221 | Adversary remote access |
43.130.75.191 | Adversary remote access |
45.86.200.81 | Adversary remote access |
194.32.120.24 | Adversary remote access |
Conclusion
The emergence of Copode 1.0 underscores the need for effective security practices including patching vulnerabilities, decreasing the attack surface, and monitoring the network for suspicious activity. As the threat landscape adapts, cybersecurity practices must evolve to remain vigilant to effectively counter these ever-more sophisticated threats.
Lumu lets you monitor connections with adversaries’ infrastructure in real time in order to efficiently detect and respond to this kind of attack.




