The Power of a Threat-Informed Defense Strategy
Reading Time: 6 minsThreat-informed defense is a strategic approach to risk-based cybersecurity that even smaller organizations can get up and running easily.
Get the latest cybersecurity articles and insights straight from the experts.

Reading Time: 6 minsThreat-informed defense is a strategic approach to risk-based cybersecurity that even smaller organizations can get up and running easily.

Reading Time: 5 minsCybersecurity Analysts can turn to these 7 habits to complement their cybersecurity strategy and be more efficient.

Reading Time: 3 minsThe 2022 Lumu Product Recap brings together all the Continuous Compromise Assessment Improvements we delivered over the last year.

Reading Time: 2 minsAs a partner in Fortinet’s Fabric-Ready Partner Program, Lumu delivers automated attack detection and response across the network. See how to integrate Lumu Defender with Fortinet’s FortiGate NGFW.

Reading Time: 4 minsThe new Lumu Incident View is a single screen that places at the cybersecurity operator’s fingertips the tools and information that they need to outwit cybercriminals at every turn.
Reading Time: 3 minsLumu Free just got a major upgrade. We’ve included more metadata collectors, giving you greater network visibility and more closely reflecting our vision of how cybersecurity needs to be operated.

Reading Time: 3 minsMSPs’ skills and resources make them perfectly positioned to fulfill SMBs’ need for increased cybersecurity resilience.
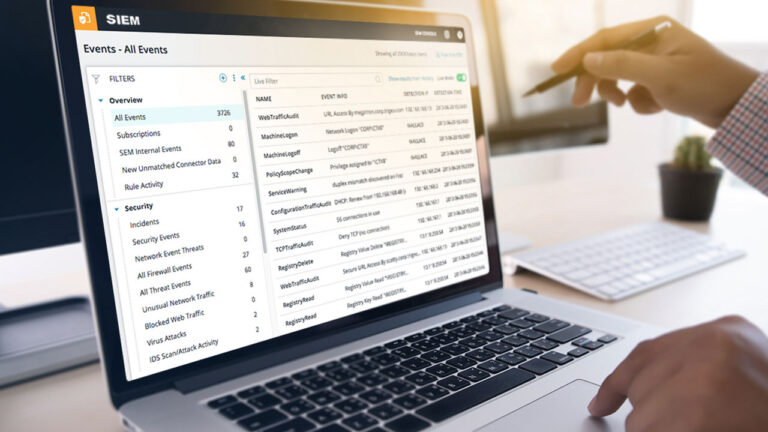
Reading Time: 4 minsVeteran Cybersecurity Operator at Lumu Andrés Argüelles looks at using Lumu with your SIEM to get the most out of both platforms.

Reading Time: 3 minsLumu Defender lets you feed Lumu’s confirmed compromise instances into your existing cybersecurity stack for an automated response to cyber threats.

Reading Time: 2 minsIn this Lumu Insights review, eWeek declares that Lumu makes ‘fighting cyber threats with actionable intelligence a work of IT art.’

Reading Time: 2 minsLumu Academy offers free cybersecurity courses on Lumu products. Get Lumu certification through our self-paced virtual courses.

Reading Time: 2 minsLumu’s New Experience is a game-changer. ‘Incidents’ groups related contacts and improves reporting for reduced alert fatigue and much more.

Reading Time: 2 minsLumu’s new custom collector allows seamless network metadata collection from third-party tools for better, faster compromise assessment.

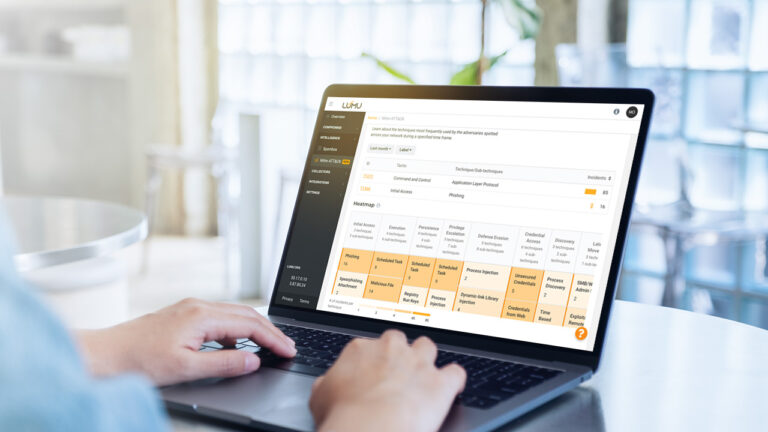
Reading Time: 4 minsAre security budgets spent on solutions that actually matter? Guest blogger Chris Steffen looks at addressing this concern with the automated ATT&CK Matrix.

Reading Time: 3 minsThe powerful MITRE ATT&CK Matrix is now integrated into the Lumu Portal, making it possible to see relevant TTPs for all detected compromises.
© Lumu Technologies All rights reserved. | Legal information.