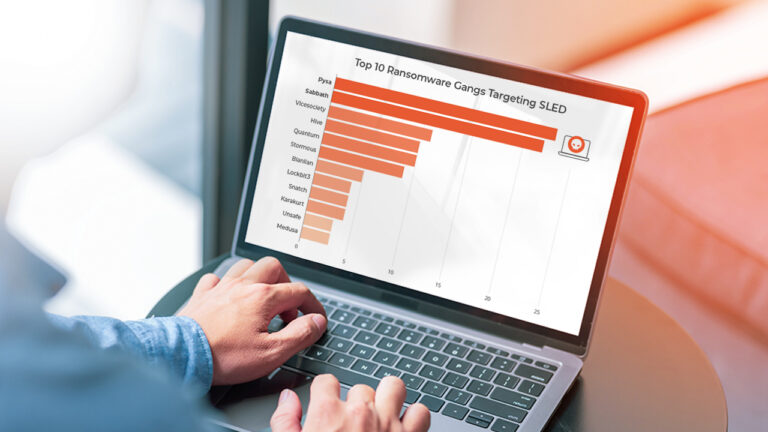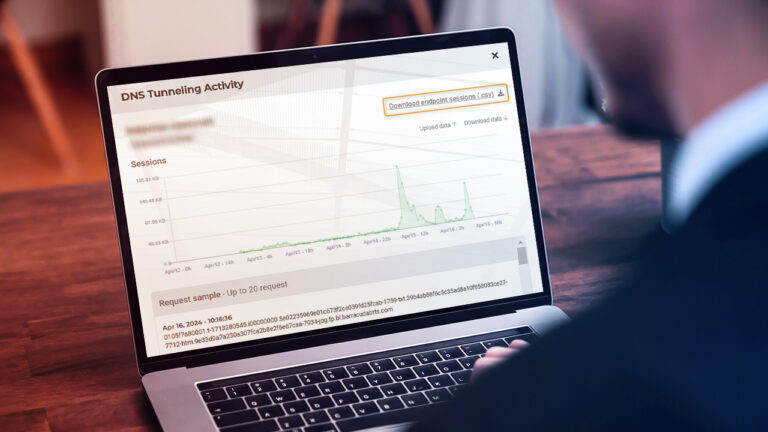
Lumu’s Detection & Response to a Real-World DNS Tunneling Attack
Reading Time: 7 minsThis is the story of a serious DNS tunneling attack on a multinational insurance provider — discover the importance of DNS tunneling detection, what we found when we investigated the attack, and how we contained it.