
The Hidden Pitfalls of Deep Packet Inspection
Reading Time: 6 minsExplore DPI’s limitations in network security and discover how Lumu’s cloud-native, metadata-driven approach provides essential visibility and threat detection.
Get the latest cybersecurity articles and insights straight from the experts.

Reading Time: 6 minsExplore DPI’s limitations in network security and discover how Lumu’s cloud-native, metadata-driven approach provides essential visibility and threat detection.

Reading Time: 6 minsDiscover how Lumu’s Playback feature improves visibility and efficiency while addressing the limitations of traditional SIEMs in handling vast amounts of network data.

Reading Time: 4 minsRansomHub is a new ransomware group offering Ransomware as a Service that has already encrypted and exfiltrated data from at least 210 victims. How does RansomHub bypass defenses and how can you defend against it?

Reading Time: 3 minsLearn how Lumu helps MSPs meet CIS compliance with real-time malware detection, network defense, and automated incident response.

Reading Time: 3 minsLearn about the recent CrowdStrike outage affecting Microsoft devices, its impact, recovery steps, and how Lumu can help ensure continued network security.

Reading Time: 4 minsDiscover Lumu’s 2023 MSP breakthroughs: Improved threat detection, incident management, and more.

Reading Time: 4 mins2023 at Lumu: Pioneering advancements in AI-driven cybersecurity solutions and partnerships, enhancing incident management and operational efficiency.

Reading Time: 2 minsDr. Chase Cunningham discusses the critical need for state and local governments to secure against ransomware, ensuring essential services.
Reading Time: 3 minsIntroducing Lumu for MSPs Lite, a free, AI-driven cybersecurity solution for Managed Service Providers, democratizing advanced threat detection.

Reading Time: 3 minsAlert: Severe Cisco IOS XE Web UI vulnerability risks full system control. Immediate action needed for users with HTTP/HTTPS Server enabled.
Reading Time: 5 minsExplore Online vs Transfer Learning in Cybersecurity: Unpacking Lumu’s adaptive AI use for proactive threat defense and staying ahead of risks.

Reading Time: 5 minsLumu’s threat intelligence team has identified a new Advanced Persistent Threat (APT) actor named ‘Copode 1.0’, leveraging the LockBit Black code leaks for cyberattacks. This emerging threat underlines the need for stringent security practices and Lumu’s real-time monitoring offers an efficient response to such evolving challenges.

Reading Time: 4 minsRSAC 2023 brought the cybersecurity world together in San Francisco. While there is a general consensus that a paradigm shift is needed in cybersecurity, it is clear that we would be stronger still if there were consensus around what that paradigm shift needs to look like.
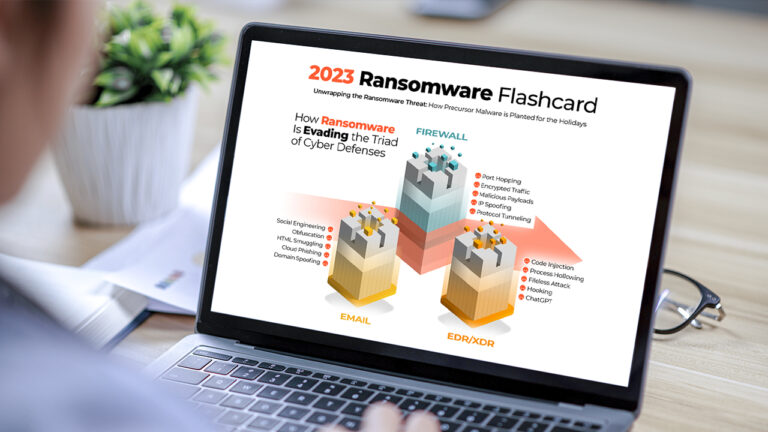
Reading Time: 3 minsExplore the key insights and trends from our 2023 Ransomware Infographic Flashcard. Learn about how hackers are evading defenses, the precursor malware they use, and ransomware’s devastating impact.

Reading Time: 11 minsEDR Evasion includes a suite of techniques that hackers use to elude endpoint defenses. Discover how hackers evade Endpoint Detection and Response (EDR) systems using various techniques. Learn about the common tactics used by cyber attackers to bypass endpoint defenses and how to better protect against these stealthy attacks.
© Lumu Technologies All rights reserved. | Legal information.