Already have an account? Sign in
Sign in
Phishing is categorized as a form of online fraud where criminals rely on posing as reputable sources in order to lure victims into giving them confidential data or tricking them into downloading malicious software. These communication tactics involve the use of email, social media, text messages, phone calls, and websites.
A severe attack on MGM resorts was perpetrated by a European cybergang called Scattered Spider that took just 10 minutes of phishing. The gang went on LinkedIn to find MGM employees, made a few fraudulent phone calls, and got login credentials. Scattered Spider has been known for leveraging social media and their success at hacking is often due to their research skills and ability to emulate people.
Phishing is the most common type of cyberattack that people face globally. It’s so prevalent that the spam box in most email accounts is often filled with a wide variety of phishing scams, from claiming to be a bank account you just opened, to outrageous declarations that you inherited a fortune from a long lost uncle in Portugal. According to the 2023 Phishing Statistics report, nearly 3.4 billion spam emails are sent daily and Google blocks about 100 million phishing emails a day.
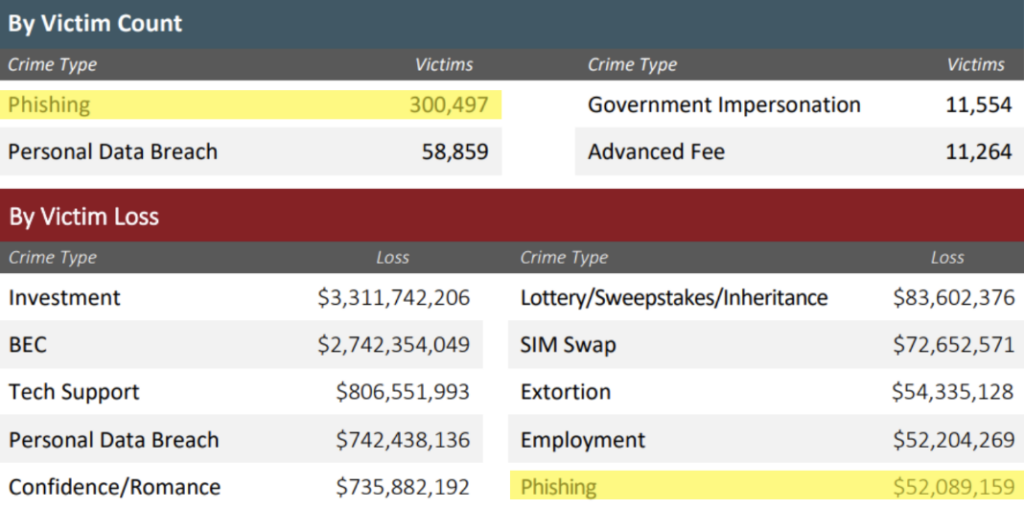
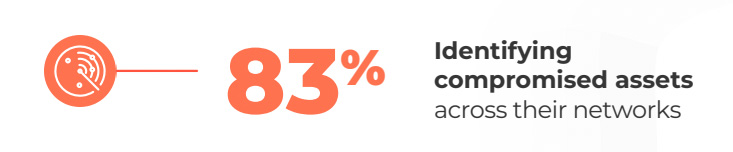
In 2022 the top internet crime experienced by the FBI was phishing, with a total count of 300,497 victims in the US resulting in a financial loss of over $52 million dollars. In the 2023 Cost of Data Breach Report, the reason why phishing has such a costly impact is due to the fact that it takes an average 298 days for phishing attacks to be identified and contained. In the United States 83% of Chief Information Security Officers (CISOs) expressed that identifying compromised assets across their network is a high-priority project.
Phishing has always been one of the top threats in cybersecurity because it’s often the very first step in a larger scale attack. According to IBM, 41% of breaches have phishing as the initial attack vector. In the MGM resort incident, phishing was used to gain access to then deploy a huge ransomware attack. MGM is said to have lost nearly $8.4 million, or about 10% to 20% of their daily revenue for each of the 9 days of system disruptions.
Precursor malware is also a common result of phishing from victims who click on supposedly legitimate links and attachments in emails. In the case of Universal Health Services (UHS), convincing emails were sent to staff impersonating trusted sources or colleagues and were filled with malicious attachments and links. UHS suffered a total loss of $67 million dollars from the attack.

Learn more about the different types of precursor malware and how it leads to ransomware.
New types of phishing tactics are developed often. Here are examples of phishing that use the most common and current trending scams out there:
Type of Attack | Description |
Spear Phishing | Attacks directed at specific companies or individuals. Lots of information is gathered to make the imposter seem like a trustworthy contact. |
Whaling | Targets strictly senior level executives with the goal of stealing large volumes of sensitive data. Most of these targets have the ability to authorize payments. |
Pharming | Tricks users into logging into very convincing fake websites to obtain their login credentials. |
Quishing | QR codes that direct victims to fake websites that may seem like restaurant menus, adverts, commercial tracking, etc. |
Voice Phishing | Phone calls targeting victims to vocally confirm their sensitive data. The victim’s voice is then recorded stating their personal data or simply getting them to say “yes” for approved transactions. |
Smishing | Attackers use convincing text messages to get victims to disclose account credentials or install malware. Also known as SMS phishing. |
Social Media Phishing | The goal is to impersonate victims by obtaining their social media logins in order to reach out and scam the victim’s friends and family via Instagram, TikTok, LinkedIn, Facebook, etc. |
Don’t be fooled! Phishing has become increasingly more sophisticated and can involve clever deception and psychological manipulation. Successful phishing attacks rely on human error and naiveté. Below are some Phishing Prevention strategies that can help your organization be better prepared:
These cybersecurity precautions will help your organization stay on top of your defenses.
There are several stages to a phishing attack and at each stage you can take action, especially when there is any uncertainty on whether data has been leaked or a backdoor has been created. Here’s what you can do if you think you are being attacked:
There are numerous options when it comes to phishing protection. Many of these tools are available at no cost, or are budget friendly. The following is a list of the basic recommended tools for phishing protection:
The Response Playbook is a quick set of guidelines that organizations can easily adapt to their needs. Paired with a Free Lumu Account, the playbook provides recommended actions for preparation, detection and analysis, containment/eradication & recovery, and post-incident activity.
© Lumu Technologies All rights reserved. | Legal information.