
Advisory Alert: PowerSchool Data Breach
Reading Time: 4 minsThe December 2024 breach of a student information software solution for K-12 educational institutions, PowerSchool, leaves us asking: what can we learn from it?

Reading Time: 4 minsThe December 2024 breach of a student information software solution for K-12 educational institutions, PowerSchool, leaves us asking: what can we learn from it?
Reading Time: 5 minsFollowing the release of data from over 15,000 Fortinet devices, what can we do to protect against further compromise?
Reading Time: 4 minsDetecting and stopping attacks using anonymization techniques can give your team the upper hand against cyber criminals — but how do attackers use anonymization and how can we defend against it?
Reading Time: 4 minsLumu has worked hand-in-hand with MSPs throughout a year that consolidated the need for cybersecurity in the role of MSPs.
Get the latest cybersecurity articles and insights straight from the experts.

Reading Time: 3 minsSupply chain risk in cybersecurity keeps increasing with threat actors exploiting third-party vulnerabilities. Here’s how you can stop them.

Reading Time: 2 minsA CISO’s list of responsibilities never gets any shorter, so we asked them about their most urgent projects. Here are their 2021 cybersecurity priorities.

Reading Time: 3 minsThe powerful MITRE ATT&CK Matrix is now integrated into the Lumu Portal, making it possible to see relevant TTPs for all detected compromises.

Reading Time: 3 minsThese holiday cybersecurity reads are sure to captivate and educate as we head into another eventful year for cybersecurity.

Reading Time: 4 minsOn average, a CISO’s tenure is only 26 months. Fabian Zambrano, Director of Cybersecurity at Davivienda, lays out any new CISO’s priorities.

Reading Time: 2 minsOn December 13th, information was released about the SolarWinds hack, one of the most extensive and serious breaches in recent U.S. history.

Reading Time: 3 minsAs security professionals, we hear about mitigation and remediation on a daily basis. However, these are terms that are commonly confused with each other.
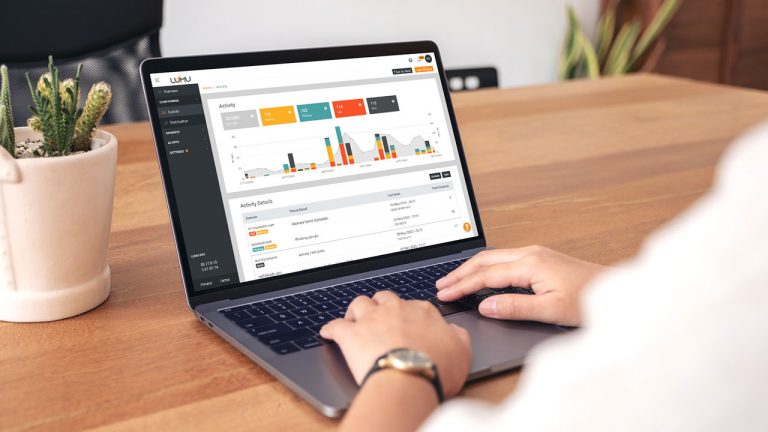
Reading Time: 4 minsSecurity operations teams are increasingly inundated with alerts. Take a look at how Lumu can make your SOC more efficient in 3 easy steps.

Reading Time: 3 minsAfter a tumultuous 2020, what will the future hold for cybersecurity in 2021? We’ve put together the 10 trends that will define the new year.

Reading Time: 3 minsFrom securing a sudden remote workforce to the rise of ransomware, CISOs have had an especially interesting year.

Reading Time: 2 minsAccording to Gartner, 88% of organizations worldwide made it mandatory or encouraged their employees to work from home due to the global pandemic situation.

Reading Time: 3 minsThe concept of Zero Trust has gradually evolved in cybersecurity. NIST’s SP 800-207 legitimizes Zero Trust Architecture (ZTA) and provides roadmaps for its deployment.

Reading Time: 4 minsOver 90% of ransomware attacks are preventable. We have compiled a list of the most common mistakes leading to ransomware regret. Do you recognize any?
Reading Time: 5 minsRansomware attacks have been increasing in frequency; we look at some examples like Sodinokibi, WannaCry, and MAZE, and how Lumu detects them.

Reading Time: 3 minsWe’ve pored through the most recent data breach reports to paint a clear picture of how cyber attacks are affecting enterprises right now.
© Lumu Technologies All rights reserved. | Legal information.