According to Gartner, 88% of organizations worldwide made it mandatory or encouraged their employees to work from home due to the global pandemic situation. In the State of Remote Work by Buffer, 99% of remote workers said they would like to continue working from home to some extent. This means that working from home is here to stay. While this has several cost and time benefits, for it to be effective and sustainable in the long term, it has to be accompanied by a strong cybersecurity model. A recent survey conducted by Lumu supports this statement: 1 in 3 companies reported reduced compromise visibility, 70% saw more attacks and incidents, and 35% cut cybersecurity budgets due to the pandemic.
A lot of current cybersecurity strategies were designed to protect on-premise assets. Needless to say, most of this defense is now sitting in empty offices. For this reason, it has never been more critical to protect our remote workforce. Regardless of the work model adopted, most teams will eventually return to the office even a couple of days a week. Their assets will have spent time in home networks and environments with lax security. Any returning compromised devices will have access to the corporate network having passed all the previously established controls, so measuring compromise on those devices is a must.
Introducing the Lumu Agent for Windows
We have always offered our clients the option to protect their remote users by integrating their VPN or SDP with Lumu. And now, Lumu is going a step further and introducing the Lumu Agent for Windows. This software is installed on your employees’ machines, running silently and collecting network metadata. The Lumu Agent for Windows works alongside other network metadata collectors such as virtual appliances and cloud collectors. This varied metadata is then correlated and analyzed by Lumu to measure compromise in real time.
The installation of the Lumu Agent for Windows is simple and straightforward. Multiple agents could be deployed easily to your entire user population through a distribution point, thus facilitating the installation and administration. Likewise, the portal allows controlling the installations with the creation of specific groups and you can check the status of each installation at a glance.
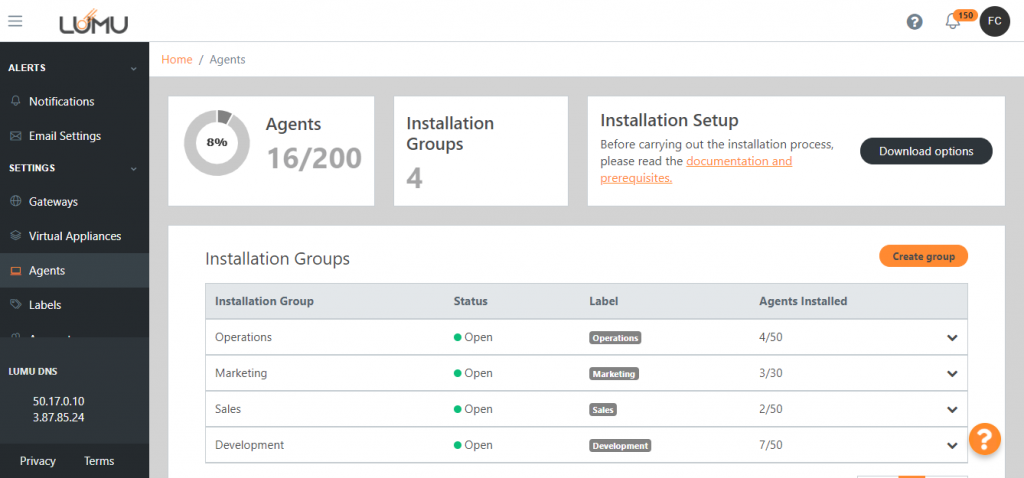
Start today
Many organizations start their Continuous Compromise Assessment journey with the Lumu Agent because you can start protecting your most critical assets and see its value right away. There are two ways to get started:




