Table of Contents
This article originally appeared exclusively in CPO Magazine on June 2, 2022.
The Conti Ransomware Group’s recent ransomware attacks reported in Costa Rica, Peru, and Chile show that threat actors have transformed from lone wolves into a globe-spanning pack of well-organized criminals disrupting and casting into disarray government entities, private organizations, and small and medium-sized businesses.
During the last couple of years, we have witnessed how a vicious cycle of ransomware has encouraged more and more threat actors to increase and diversify their attacks against all kinds of organizations. Consequently, they have improved access to sensitive information, increased profits, and created alliances that allow them to perform their actions with speed while causing the most damage possible.
Cyberwarfare Without Borders
Today the world is seeing how not only critical infrastructures are being targeted. Healthcare, education, finance, private, and public organizations can be hit as well by a ransomware attack. Tracking the origin of these attacks can lead to an endless maze.
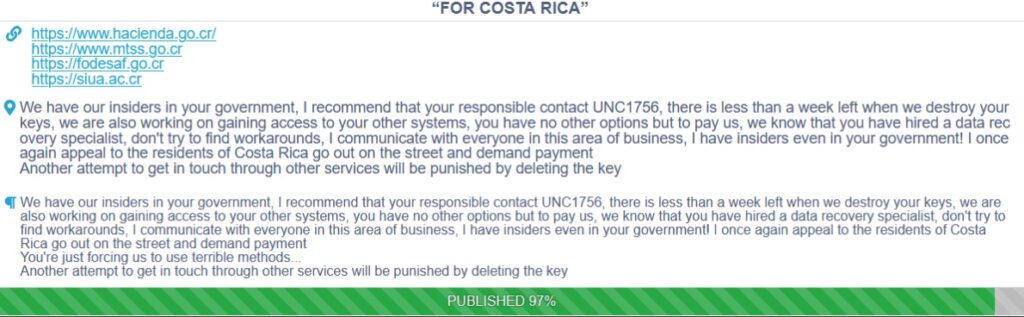
This is the case in Costa Rica, which at the time of writing this blog has been under attack for 4 consecutive weeks, without having a clear picture of who’s responsible for attacks targeting 27 government institutions and ransom demands that double with each passing week. There have even been suspicions that insiders from the same country are collaborating with the Conti Ransomware Group.
Precursors Are Not Randomly Deployed
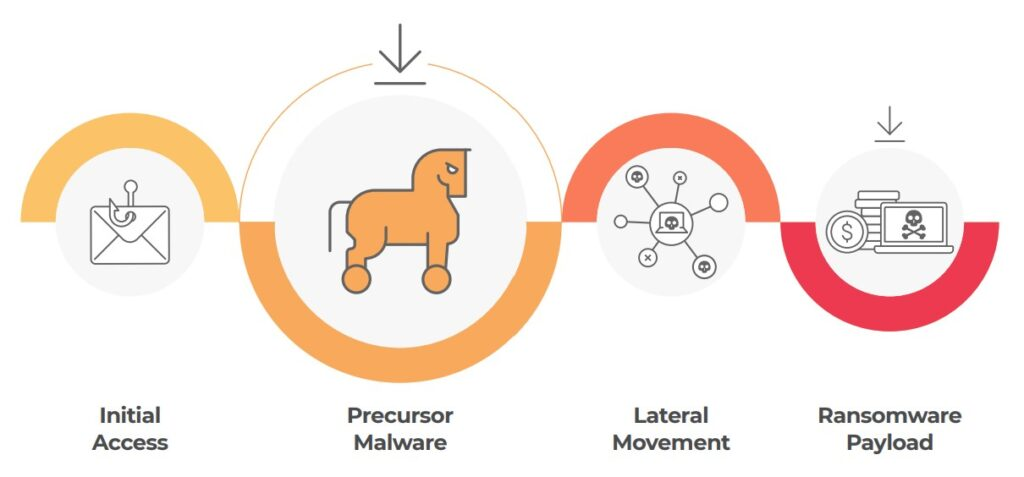
Ransomware does not appear out of thin air, it is instead the result of a chain of ‘minor’ incidents—known as precursors—that were not addressed in time. However, these so-called ‘minor’ incidents are not random. On the contrary, they are tried and tested techniques executed by threat actors that have joined forces to achieve their ultimate goals: creating disruption, increasing profit, and avoiding getting caught.
As is shown in the image above, the ransomware attack starts with the initial access stage. This is performed by groups of cybercriminals and affiliates specializing in reconnaissance, crafting highly targeted phishing attacks, and getting credentials for accessing the network.
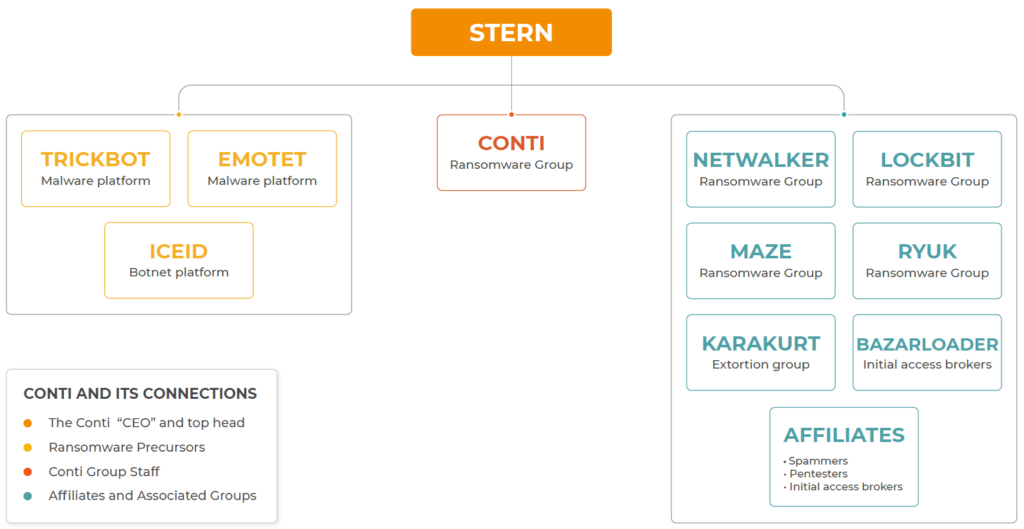
Then it’s the precursors’ turn where the goal is to pave the road with malware. In the case of the Conti Ransomware Group’s attacks, this is done by groups such as Emotet, LockBit, Trickbot, IceID, and BazarLoader.
In the next stage known as lateral movement, a different group of threat actors appears on the scene to start moving through the network to infect as many devices as possible and find information to be exfiltrated or encrypted.
Finally, it’s the moment for dropping the ransomware payload, which is when all hell breaks loose: blue screens, ransom notes everywhere, media coverage, and a scrambled PR response. Typically, this is when the organizations—belatedly— decide to take action against the threat.
The Success of Ransomware as a Service (RaaS)
The distribution of tasks among different threat groups allows the RaaS organizations to lower the risk of being caught and effectively increase their profit in the short term. The success of this cybercrime model has led to the recent spike in ransomware attacks associated with Conti Ransomware Group and its affiliates. This forced the U.S. government to issue a $15M bounty for information about this gang just after a month after having issued a letter that warned about these attacks.
Conti Ransomware Group and Precursor Malware Devs Collaborate
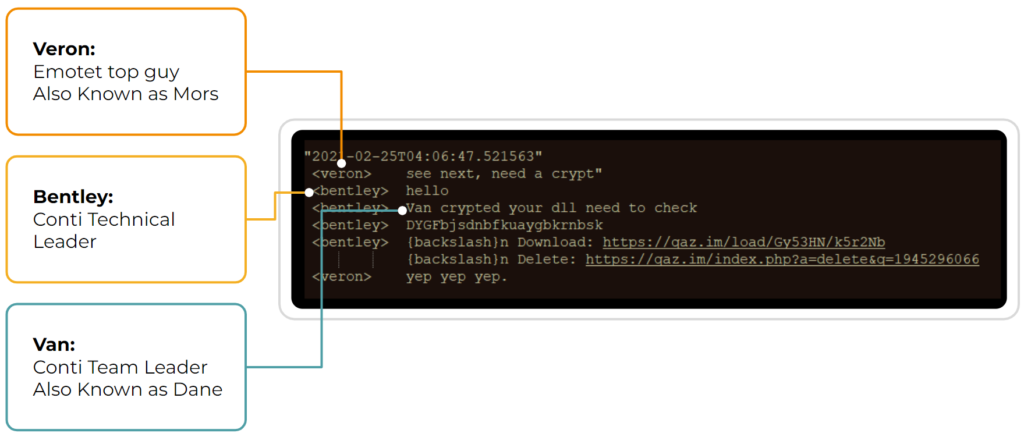
As we’ve mentioned above, ransomware relies on precursor malware to gain network access and escalate privileges. In the following conversations obtained from the Conti Leaks, you can see the close cooperation that exists between all echelons of the Conti Ransomware Group and the developers of precursor malware such as Emotet and Trickbot.
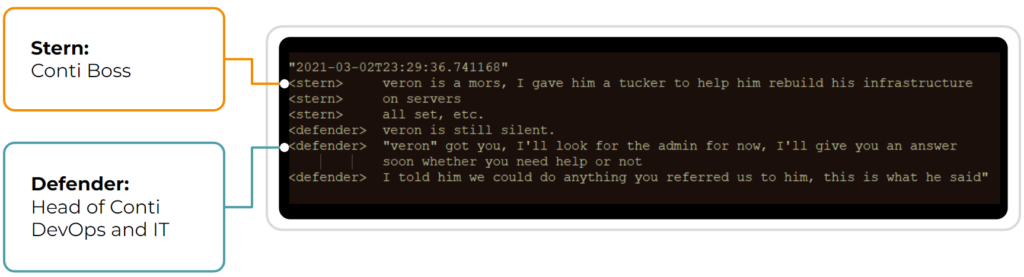
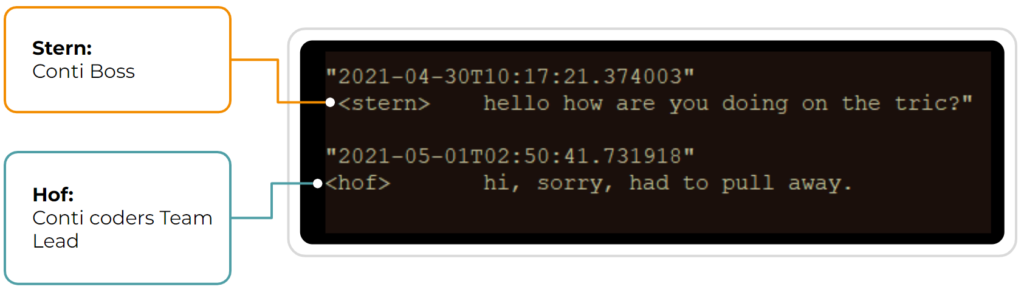
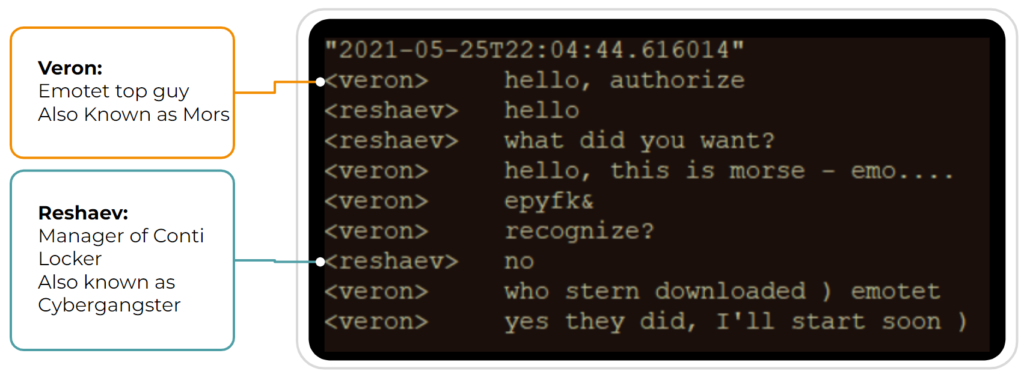
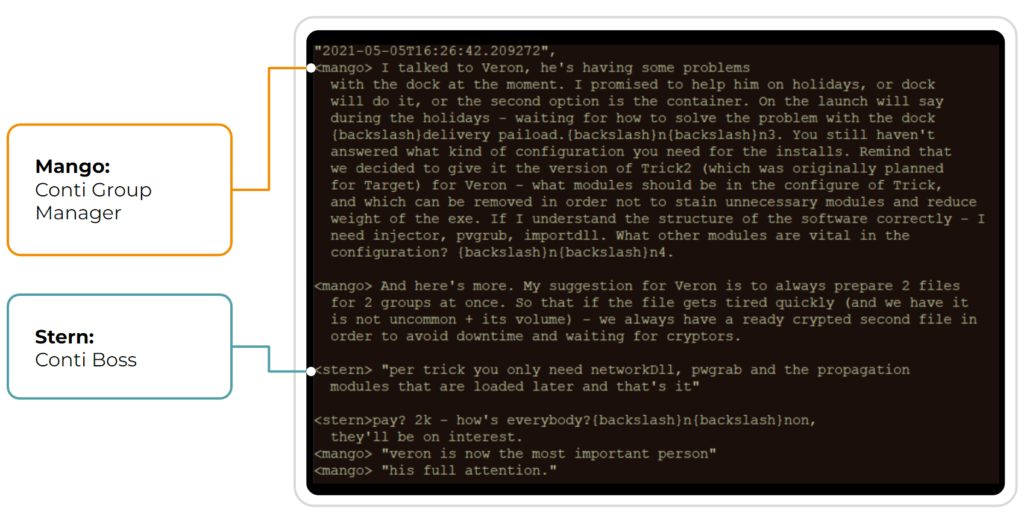
Stopping the Conti Ransomware Group in Time
When a network becomes compromised, it starts to behave differently. Threat actors need to use the network to carry out each phase of their plans, leaving behind evidence of their actions in your network’s metadata. That’s why the Conti Ransomware Group can be stopped if the precursors are intentionally detected and eradicated in time. You decide if you want to deal with a lizard, or a Komodo dragon.
Lumu enables organizations of any size to detect ongoing ransomware attacks by providing full context into each of the stages of ransomware incidents. This allows you to understand the nature of attacks and respond promptly. When was your last compromise assessment? Open your free account now.