
Mitigate & Remediate – Don’t Skip Either in Incident Response
Reading Time: 3 minsAs security professionals, we hear about mitigation and remediation on a daily basis. However, these are terms that are commonly confused with each other.
Get the latest cybersecurity articles and insights straight from the experts.

Reading Time: 3 minsAs security professionals, we hear about mitigation and remediation on a daily basis. However, these are terms that are commonly confused with each other.
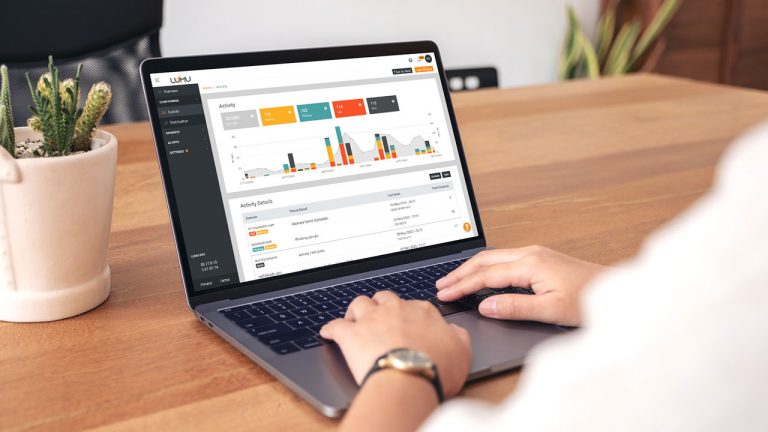
Reading Time: 4 minsSecurity operations teams are increasingly inundated with alerts. Take a look at how Lumu can make your SOC more efficient in 3 easy steps.

Reading Time: 2 minsAccording to Gartner, 88% of organizations worldwide made it mandatory or encouraged their employees to work from home due to the global pandemic situation.
Reading Time: 5 minsRansomware attacks have been increasing in frequency; we look at some examples like Sodinokibi, WannaCry, and MAZE, and how Lumu detects them.

Reading Time: 3 minsAnalyzing spam metadata lets Lumu’s portal present insights on which users are being targeted and how your company is being compromised.

Reading Time: 3 minsUn equipo de seguridad promedio recibe diariamente 3.000 notificaciones y esta cifra aumentó en casi 20% el año pasado. La revisión de alertas les está

Reading Time: 3 minsLumu now provides compromise context in one place, providing more insight into the nature of attacks and improving incident response

Reading Time: 2 minsNetwork metadata has the power to efficiently answer the most important question in cybersecurity: Is my network compromised?

Reading Time: 2 minsContinuous Compromise Assessment identifies cybercriminals in real time by using several cutting-edge technologies.
© Lumu Technologies All rights reserved. | Legal information.