Table of Contents
Organizations are under constant pressure to adopt the latest cybersecurity tools, often without full visibility into whether these solutions provide real value. There are many approaches when it comes to detecting and identifying compromise in an organization’s network and not all are created equally.
Deep Packet Inspection (DPI) has long been hailed as a key method for monitoring and analyzing network traffic to detect potential threats. However, as networks have changed and encryption becomes pervasive, the effectiveness of DPI is increasingly challenged. What was once considered an essential practice has now become more of an ideal than a practical reality. The inherent complexity and high costs of DPI have led many traditional vendors to shift their so-called DPI deployments into behind-the-scenes tools, merely listening to a port mirror to synthesize network metadata from packet captures (pcaps), yet they continue to be marketed as the shiny box they once were.
In this blog, we will explore common pitfalls associated with DPI and why Lumu’s approach offers a more modern, accurate, and comprehensive approach to network threat detection.
The Growing Challenge of Encrypted Traffic
As encryption becomes the norm for securing data in transit, the ability of DPI to provide meaningful insights into network traffic is rapidly diminishing. Historically, DPI thrived in environments where most communications were unencrypted, allowing the tool to inspect traffic at key points within the network easily. However, modern encryption protocols, such as TLS 1.3, have made it more challenging for DPI solutions to analyze traffic effectively. Encryption methods have evolved to protect not just sensitive data, but all network communications, making it harder to gain visibility into what’s happening across the network.
DPI tools that try to bypass this challenge often resort to decrypting traffic for inspection, but this approach comes with serious downsides:
- The decryption process itself introduces delays and complexity. It requires significant computational resources, leading to increased costs and performance bottlenecks, especially in environments with high volumes of encrypted traffic.
- Decrypting traffic also means that sensitive data is exposed during the inspection process, creating new points of vulnerability. Even if encryption is reapplied after analysis, this “man-in-the-middle” approach can create security risks and erode the very protection that encryption is supposed to provide.
- DPI can struggle with sophisticated evasion tactics like fragmented packets or traffic tunneling (e.g., over DNS), allowing attackers to bypass detection. This further reduces its effectiveness in modern threat landscapes.
End-to-End Encryption Complicates DPI Further
With the widespread use of end-to-end encryption, decrypting traffic is no longer possible in many cases. Much of the data can remain encrypted due to layered encryption protocols. This means that despite the effort, the decrypted data may still not be readable or useful for threat detection. Given the time and resources involved, decrypting traffic in hopes of gaining insights is often not worth the trouble, especially when there are more efficient ways to monitor network activity.
To avoid the roadblocks and complexities of decryption, the focus should be on the behavior and metadata of network communications, which provides sufficient visibility. When suspicious communication patterns arise, they should be identified and stopped immediately, without needing to decrypt and inspect the contents. The specifics of the communication are less important than recognizing that it shouldn’t be happening in the first place.
Reliance on Physical Devices
One of the major limitations of DPI is its reliance on physical devices to monitor network traffic. In legacy environments where everything was centralized, plugging in a device to inspect network traffic was straightforward.
Limited Traffic Visibility
In today’s distributed networks, capturing all traffic across every endpoint is nearly impossible which results in organizations only focusing on specific high-priority areas of the network. This presents a lot of risk.
For example, if a threat emerges in an area of the network that is not monitored due to its perceived lower importance, it could remain undetected until it reaches more sensitive segments. This delayed detection can significantly impact response times, as the threat has already had the opportunity to spread and potentially cause damage. By the time security teams are alerted, the attacker may have already compromised critical systems, leaving little time to mitigate the threat effectively.
Focusing on specific, high-priority areas of the network creates inherent blind spots, allowing attackers to exploit less monitored sections of the network, move laterally, and escalate their access without being detected until it’s too late.
Inability to Detect Unknown Threats
Another issue with physical devices is their reliance on known signatures to detect threats, which makes identifying zero-day attacks or unknown threat patterns highly unrealistic. In an environment where new and evolving threats emerge constantly, traditional DPI lacks the advanced analytics necessary to catch these attacks.
When a new or previously unseen attack pattern occurs, DPI tools may fail to detect it because they rely heavily on predefined signatures. This means it can only detect already known threats. As a new threat moves through the network, the DPI system may not recognize its malicious intent until it’s too late.
While advanced AI and machine learning could theoretically address these gaps, integrating this technology into DPI solutions requires immense computational resources. Single-box deployments typically used in most NDR solutions simply don’t have the power to support these advanced capabilities, making this ideal difficult to achieve in practice.
Managing a DPI Model — Costly and Complex
Deploying DPI across a modern network can be cost prohibitive. Traffic no longer flows through a few central routers and switches. DPI solutions require specialized hardware, and covering all endpoints often means deploying multiple devices, each adding to the cost.
Another major issue is the impracticality of decrypting traffic at scale. Today’s networks are distributed, often spanning cloud environments, remote users, and third-party services. Trying to decrypt and inspect traffic across this decentralized landscape requires deploying costly hardware solutions in numerous locations, something that is neither cost-effective nor operationally efficient. DPI’s decryption methods can’t keep up with the realities of modern network architectures.
The Network Before, Mostly On-Prem
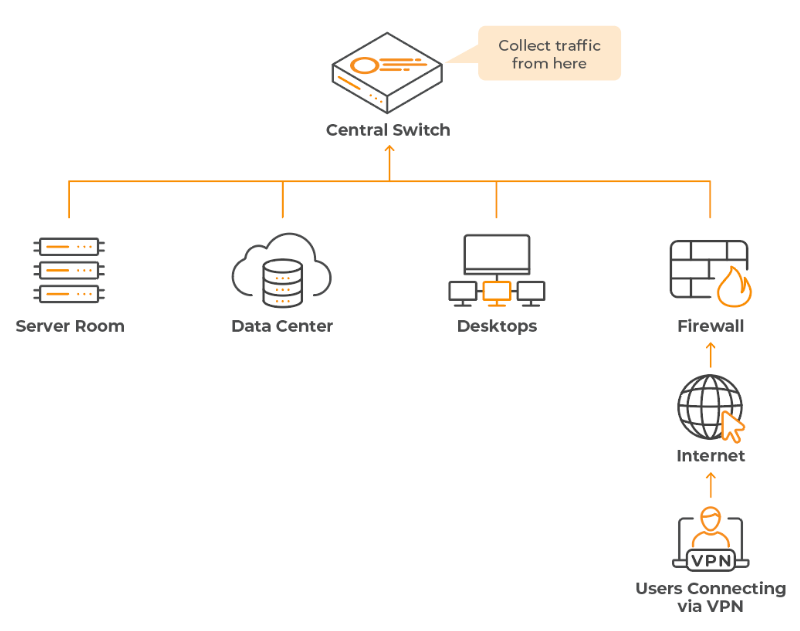
Today’s Highly Distributed Network
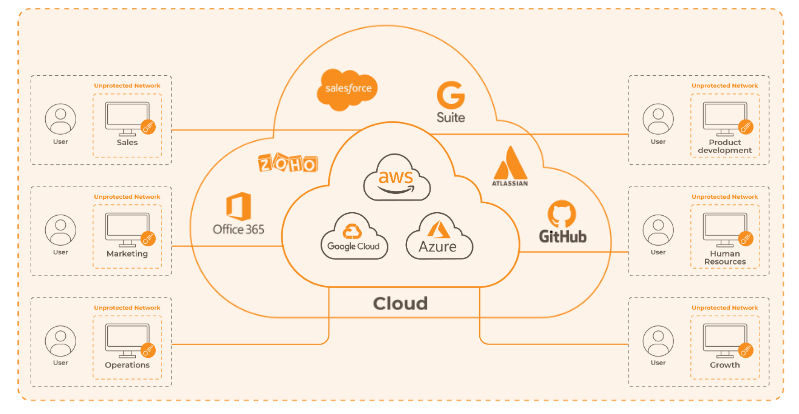
Future Proofing
Data volume is growing exponentially, with internet traffic increasing at an annual rate of about 20%. Considering the high computational cost of cryptographic operations, this means that the new box installed today could struggle to decrypt or analyze the traffic in just a few months. As companies grow, so does the need for more DPI devices, each requiring installation at various network points to maintain the same level of visibility. This hardware-centric model means that as your network grows, the costs of maintaining and scaling DPI solutions can quickly spiral out of control.
Lumu’s Approach: Comprehensive, Cost-Effective, and Cloud-Ready
Cost Efficiency: While DPI may have a role in specific network environments, its limitations make it less suitable for today’s complex networks. Lumu offers a solution that not only addresses the blind spots of DPI but also provides a cost-effective and efficient way to monitor all network traffic.
Complete Visibility: Lumu’s platform offers comprehensive visibility across the entire network by capturing and analyzing metadata from all segments and endpoints. Unlike solutions that rely on physical devices and selective monitoring, Lumu seamlessly integrates with existing infrastructure—firewalls, proxies, and cloud environments—ensuring that no part of the network is overlooked. This ensures early detection of threats, providing real-time insights across distributed environments without any blind spots.
Metadata-Driven Security: Lumu doesn’t rely on decrypting data. Instead, it focuses on behavior and metadata of network communications, which provides the necessary visibility to detect and stop malicious activity. By not needing to decrypt traffic, Lumu eliminates unnecessary complexity, cost, and security risks, ensuring efficient, uninterrupted network monitoring. If your network is contacting malicious infrastructure, regardless of what was exchanged, we know that contact should not have happened in the first place and it needs to be stopped immediately.
Scalability: Through our cloud-native, metadata-driven approach Lumu is more scalable and cost-effective, without the need for specialized hardware deployments. Lumu can be deployed rapidly—often within hours—providing full network visibility with minimal setup and operational overhead. As your network grows, Lumu scales effortlessly, ensuring that you can maintain threat detection without the high costs and long implementation times associated with legacy models.
Big name vendors place unnecessary importance on legacy DPI, but in reality, it’s nothing more than a false sense of security. By focusing on actionable network metadata, Lumu ensures organizations have the visibility they need to stay ahead of potential threats, without the drawbacks of legacy DPI methods. To try Lumu’s approach for yourself, open a Lumu Free account.




