One of the biggest challenges in cybersecurity is to execute a strategy and turn it into reality. We live in a world with an abundance of data but the problem lies in operationalizing all this data. Mastering this very fact could be the difference between a successful security operations team or one that is overwhelmed with limited impact on the business.
We are grateful that more than 1000 organizations trust us to help them measure compromise in real-time. The companies that see the most value out of their Lumu account are those who include it in their daily operational tactics. If you are yet to make this move, here is a guide on how to do it.
FIRST
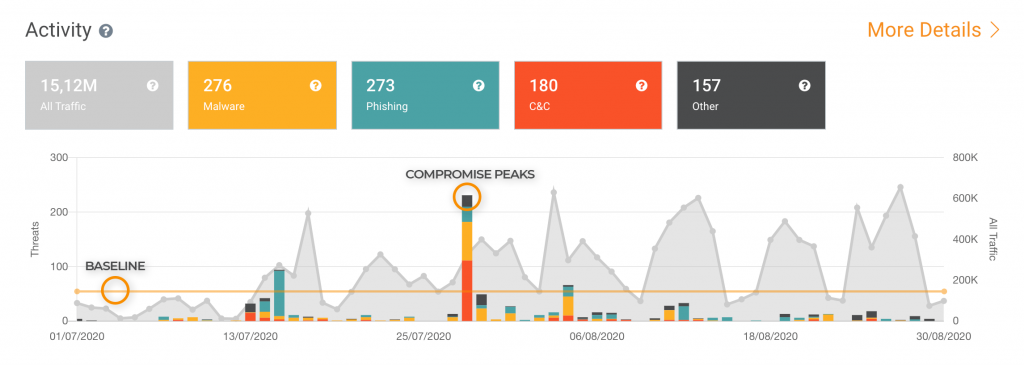
The first step is to allow Lumu to determine the compromise baseline in your organization. As the famous management expert Peter Drucker said, “If you can’t measure it, you can’t manage it”. Before Lumu there was no security operations tool looking intentionally and continuously for the organization’s level of compromise. Now, with Lumu you can know at any given moment your level of compromise and know with hard facts if your strategy and tactics are working as expected. To do this you can go to your Lumu dashboard and know the normal behavior of your company. If you see peaks like the one shown in the graph below something is happening and needs your attention. Also, you will know your compromise baseline, which tools are working, and which tools need adjustment. These adjustments will allow you to attain the ultimate goal of a cybersecurity system: a state of zero compromise.
SECOND
The second step is to take a deep dive into the compromises already inside your organization. A common question here concerns how to prioritize alerts with Lumu. Unfortunately, there is no magic formula that works for everyone but rather we must adapt according to our own business. The good news is that we have developed a series of steps to support this process.
What is a priority for your company?
According to NIST Special Publication 800-61 revision 2, incidents should not be handled on a first-come, first-served basis. Instead, handling should be prioritized based on relevant factors such as functional impact, information impact, and recoverability of the incident. This means that effective incident prioritization requires your knowledge of your business. The following are some general factors that a security operations team can consider when prioritizing incidents while using Lumu:
Affected Label: Companies can define labels in the Lumu Portal to help easily identify the compromise distribution across your infrastructure. Labels will give you the power to sort and view your traffic by geography, network segments, device, domains, critical assets, or as needed. This is a key feature for prioritization because it allows you to define the most critical assets according to your own reality and is very flexible.
Type of attack: All compromises are important but in case of limited resources you may need to decide which event to act on first. The type of attack along with other factors such as the damage an event can cause are good indicators to guide your prioritization. For example, a command and control attack on a critical server should have more priority than a laptop accessing a phishing domain on your guest network. However, some cases could be less obvious. For example, a cryptomining attack, at first sight, is less urgent than a command and control server. But when tied to other information, it could be an indicator of a bigger attack.
Compromise Radar and Attack Distribution: The nature of the contacts (automatic or manual) and the attack distribution is a priority multiplier. A ransomware attack that is propagating through multiple devices and environments must have more priority than a single machine that could be easily isolated and contained. Further, an automatic contact being detected every hour is an indication that the compromise is more dangerous than a detached event.
A broader view: It is important to always keep the big picture in mind. Even though you can focus on single events, sometimes it is useful to look at the event correlation. Constant interaction with C2C servers of a spam botnet could be the cause of continuous interaction with spam domains. So instead of focusing on the spam issue, you should focus to eradicate its source which is the C2C interaction.
THIRD
Reducing Dwell Time
After your security operations team knows what compromises to investigate first, they are ready for the next step: incident response with Lumu. In this respect, you will find useful our playbooks and the video below will guide you through a real use case.
In the end, the goal of this step is to reduce the (shameful) average dwell time of 208 days to minutes and Lumu provides you all the tools to do it. All you need to do is use Lumu to detect the confirmed compromised devices and start the incident response process. If you have any questions you can contact us at [email protected] and we will gladly help you.