Table of Contents
According to NIST, anonymization is the “process that removes the association between the identifying dataset and the data subject”, or in other words, hiding the identity of the information owner or source. This carries different connotations depending on the context. For users, anonymization is fundamental to protecting their sensitive data and actions on the web, ensuring their right to confidentiality. On the other hand, attackers can exploit this technique for very different purposes. If a victim cannot identify the source of an attack on their infrastructure, incident response becomes significantly more challenging.
Anonymization Techniques in Cyberattacks
Recently, several threat actors, including ransomware gangs, have increasingly employed anonymization techniques in their attack chains. Techniques such as T1090.002 – External Proxy and T1090.003 – Multihop Proxy are used to evade critical alerts linked to malicious infrastructure. This not only complicates the identification and attribution of specific threat actors, but also helps them avoid legal repercussions. Furthermore, these techniques make it difficult for victims to implement effective defense measures, making the overall response process more complicated.
A proxy acts as an intermediary for network communications with a command-and-control (C2) server, preventing direct connections to the attackers’ infrastructure. In 2024, gangs such as LockBit 3.0, BianLian, and different APTs such as APT28 and APT29 have used multiple compromised infrastructures with proxy tools like Rsocks, Socks5, Htran, and ProxyChains in prominent attacks. These tools allow them to pivot their attack chains, concealing their servers and real infrastructure behind public networks. Although this approach generally contains only one step or just one infrastructure between the victim and the attacker, it significantly delays the hunting and attribution process.
Commercial VPNs Used for Anonymization
Similarly, malicious actors have used commercial VPNs to carry out their attacks and mask their malicious activities. Recently, Lumu’s CTI team identified the gang Copode 1.0, active in Latin America, using a combination of commercial VPNs and compromised proxy infrastructure to obscure their movements and evade detection. Corvus Insurance detected in Q3 2024 that at least 28% of all ransomware attacks included compromised access to proprietary or commercial VPNs.
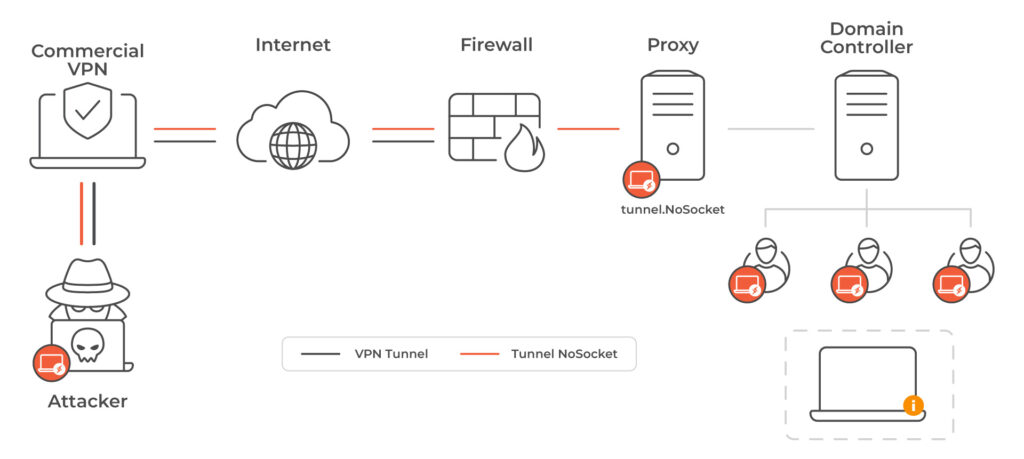
Copode 1.0 Attack topology
Multihop Proxy Anonymization
T1090.003 – Multihop Proxy represents a kind of evolution of the T1090.002 – External Proxy technique by chaining multiple proxies to hide the source of malicious traffic.
The Tor network serves as an exemplary implementation of this technique. The Onion Router (Tor) project provides an alternative method for anonymizing traffic by routing it through a chain of nodes or “relays”, each adding a layer of encryption (hence the name “onion routing”) building an encrypted tunnel using TLS. In this system, the entry and exit nodes act as proxies, as they are the only points with direct communication with the user and the destination service.
Today, Tor is the cornerstone of the Dark Web, with countless users relying on Tor to protect their browsing. Still, many malware and cybercriminal groups exploit Tor’s robust anonymization infrastructure to hide their operations, further complicating detection and attribution efforts.
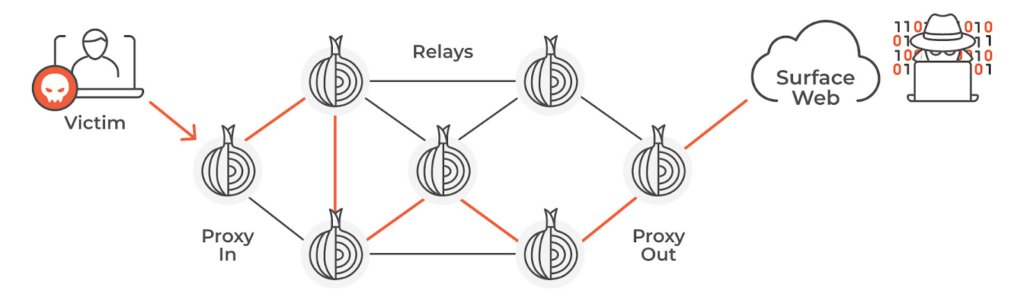
TOR – Proxy out scheme
Over the past year, the malware SystemBC has evolved significantly. Initially designed as a VPN tool using a SOCKS5 proxy, it has transformed into a sophisticated backdoor. SystemBC now leverages the Tor network to maintain persistence and complicate the monitoring of its connections to command-and-control (C2) servers. Equipped with capabilities to execute Windows commands, distribute scripts, deploy malicious DLLs, enable remote management and monitoring, and create backdoors, it provides attackers with versatile functionality. This malware has been observed in multiple attacks orchestrated by prominent ransomware gangs such as Ryuk and Egregor.
How Lumu Adresses Attacker Anonymization
Lumu provides real-time up-to-date information about active Tor nodes, proxy, and VPN infrastructure — providing network administrators complete visibility about which network contacts are anonymized. Anonymizer-linked threats are clearly identified within the Lumu portal, allowing for efficient filtering and focused threat management.
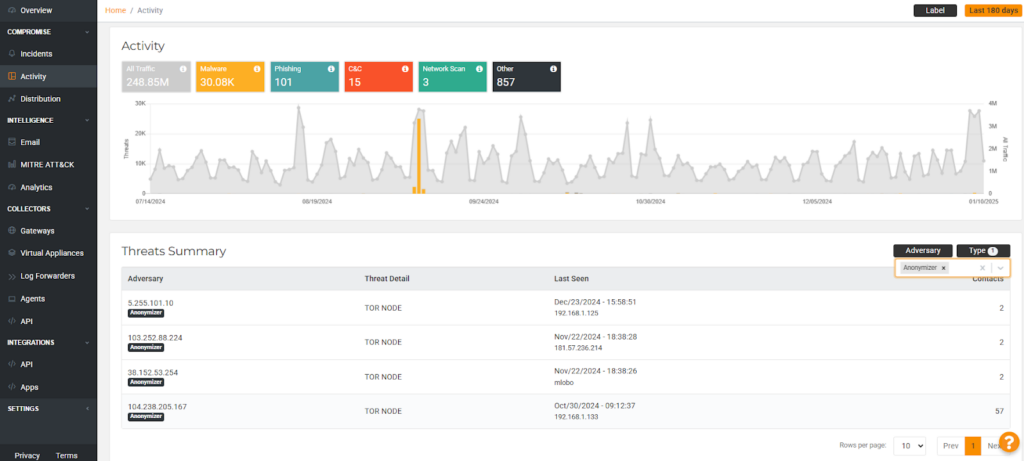
Lumu Defender offers the capability to integrate with your security stack to block and contain connections to Tor, proxy, or non-approved VPN infrastructure. This provides valuable time to investigate the source and purpose of these connections within your network, enabling you to mitigate risks promptly and effectively.
For several security reasons, allowing connections to infrastructure associated with commercial VPNs (except for approved, secured, and monitored corporate VPNs), proxies, and Tor nodes is generally undesirable in a secure corporate network. Such connections can enable attackers to conceal their activities, allow users to bypass security measures and network controls, and, more broadly, reduce the network’s overall visibility and control. Lumu gives your security team control to block these connections automatically.
Concerned about the risks of anonymized attacks on your organization? Claim your Lumu Free account and get started on your journey to comprehensive network visibility.