Table of Contents
With the summer holidays ending, students are set to return to K–12 schools nationwide. While students will just be starting classes, school district IT staff, including technology directors and system admins, have been busy preparing. Devices must be issued to students and staff and set up. New user accounts must be set up and software pre-installed. Unexpected problems must be troubleshot. As old networks strain under the influx of new users and devices, IT staff must now also address the growing threat of cyberattacks. In this blog, we’ll cover some key school cybersecurity tips for IT staff to bear in mind during the back-to-school rush.
Know Your Enemy: Why Threat Actors Target Schools
Students’ data is valuable. Threat actors will look to resell credentials online. For one thing, children haven’t had the opportunity to tarnish their credit ratings. More importantly, a 12-year-old student might not check their credit rating until their 20s. The identity thief therefore has almost 10 years with which to open new accounts and commit fraudulent purchases.
Additionally, the public funding available to schools for IT initiatives has increased in recent years. This funding can increase risks in two ways. First, new vulnerabilities can enter systems through new technologies. Second, threat actors know that more funds can be demanded in the case of a ransomware attack.
Chromebook Cybersecurity: Pros and Cons
Chromebooks are popular in schools for good reason. Their design makes it difficult for them to be used for anything beyond their intended purpose. 3rd party software can’t easily be installed on ChromeOS and neither can malware. They are also easy to restore to their default configurations.
Because of ChromeOS’s limitations antimalware and endpoint detection and response (EDR) can’t be installed either. At first glance, this might not seem like a big deal, since Chromebooks have such limited capabilities that they aren’t valuable targets for threat actors. However, threat actors can use ChromeOS devices for initial access, to move laterally or to escalate privileges on more valuable devices. Especially in cases where students are allowed to take their devices home and leave the school’s defensive perimeter, these devices could be the perfect initial compromise vector and then permitted to return to the network.
Essentially, Chromebooks’ advantages lie in their general safety and limited capabilities, their disadvantages lie in the lack of visibility. It is essential to deploy network monitoring that does not rely on software installed on individual devices. Network Analysis and Visibility (NAV) tools can monitor the traffic originating from those devices to the internet (north-south traffic) and traffic between ChromeOS devices and other information assets in the network (east-west traffic). When threat actors use this traffic for malicious purposes, an NAV tool can detect that behavior in real time.
Timing of Attacks: When You Are Most Vulnerable
Threat actors will look to attack when you are most vulnerable. The back-to-school period is a prime time for cyberattacks because IT staff are preoccupied with many tasks. Attacks take time to evolve, so it’s crucial to close adversaries’ windows of opportunity quickly. Stay vigilant and proactive to mitigate potential threats.
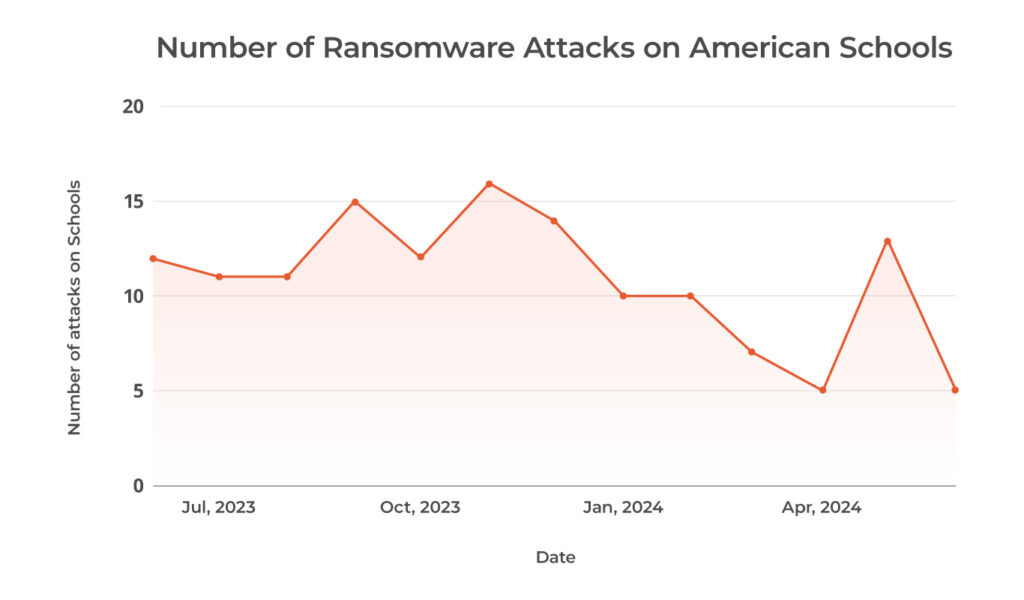
Source: Comparitech
According to the IBM Cost of a Data breach 2023, the mean time to identify and contain a breach was 277 days. However, according to Security intelligence, ransomware only needs as little as 3.85 days. Unfortunately, threat actors too often have the luxury of being able to time attacks when they can cause the most damage.
Invest in Time-Saving Cybersecurity Tools
Your time is valuable. Many schools and school districts oversee networks that are the size of large enterprises while relying on small teams. Investing in tools that make cybersecurity easier, not harder, is essential. Many Cybersecurity tools are designed for large enterprises, expecting that there will be experts available to dedicate to managing and maintaining those tools. Schools usually have limited teams and resources and have to choose how to spend their time wisely.
Look for solutions that offer seamless integrations and can automate routine tasks, allowing you to focus on more critical issues. Effective tools can streamline your workload and enhance your overall cybersecurity posture.
Know that Help Is at Hand
The Department of Education and the Cybersecurity & Infrastructure Security Agency (CISA) recognize the threat faced by K–12 Schools and have released several initiatives to secure these vulnerable networks. Most recently, the launch of the Government Coordinating Council aims to improve the online safety of students, staff, and communities.
Get the Basics Right
As students return to K–12 schools, it’s important to review that these basic cybersecurity controls are in place:
- Regularly update software
- Implement multi-factor authentication (MFA)
- Educate users on cybersecurity best practices
- Segment the network
- Maintain an incident response plan
- Perform regular data backups
- Deploy endpoint protection where possible
- Monitor and log network activity
- Enforce strict access controls
- Secure remote access through VPNs or SDPs
How You Can Protect Your School with Lumu
Many schools across the United States embrace Lumu to operate cybersecurity proficiently. First, Lumu gives them visibility into the network and DNS traffic that allows them to detect threats in real time without having to be installed on individual endpoints. Lumu also doesn’t require additional staff to deploy or maintain, empowering existing team members. Finally, Lumu integrates with existing cybersecurity solutions in the stack like firewalls and EDR solutions to automate response to any threats.
Hear from Sublette County School District Director Chris Rule on why his team loves Lumu.
As the new academic year begins, ensuring the cybersecurity of your K-12 school is more critical than ever. Lumu helps schools across the United States achieve real-time network visibility and threat detection without additional staffing or complex deployments. Open a Lumu Free account and get started today.




