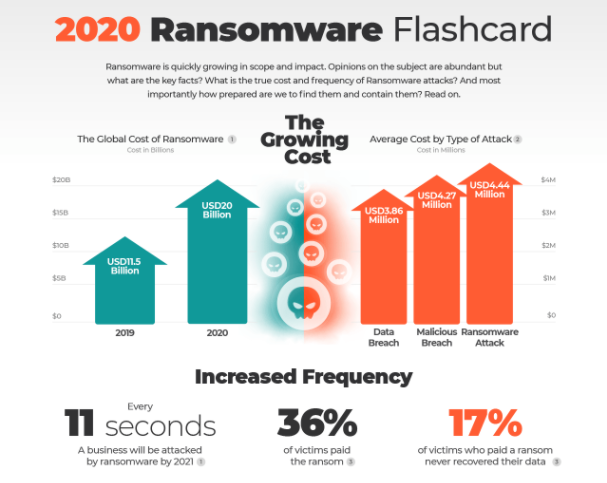
In April 2021, the Associated Press reported that Broward County public school district—the sixth-largest U.S. school district—has been targeted in a devastating ransomware attack with the group behind the attack (the Conti gang) demanding an astronomical sum of $40 million to decrypt their machines and data.
Sadly this is not an elaborate April Fools prank but just the latest in a long line of successful Florida ransomware attacks. As Lumu is headquartered here in the Miami area and given the fact that ransomware represents an existential threat that impacts all of our customers, I wanted to share a few quick reactions to this latest attack, what this might tell us about future ransomware attacks, and what steps organizations should take to better prepare themselves.
Here are four fast observations about this latest attack:
- Ransomware Gangs Are Getting Smarter: The threat actors behind these attacks are growing in sophistication and discipline. In many cases they are adopting many of the practices and methodologies that are common in the corporate world—for instance, some have integrated customer support features including real-time chat and have embraced incentive-based affiliate marketing models such as affordably priced Ransomware-as-a-Service (RaaS) offerings to broaden their reach and reduce their potential risk exposure.
- Ransomware Operator Tactics Have Also Evolved: A few years ago, most ransomware operators would cast a very wide net in which they might use a botnet to distribute millions of phishing emails and hoping to hit pay dirt. Now they are increasingly investing the time upfront to handpick their victims with a special focus on seeking out ‘softer’ targets such as underfunded school districts who don’t have the hardened cybersecurity resources of the private industry at their disposal.
- Reconnaissance is the New Primary Objective: In addition to being more selective about who they are targeting, ransomware gangs are re-thinking what they do once they successfully breach the network perimeter. Unlike a simple ‘smash and grab’ street criminal, this new generation of threat actors will stick around undetected inside the network for months, quietly conducting reconnaissance on the network and data inside so they can extract the greatest amount of value from their victims. One way we are seeing this play out is in the rise of ‘double extortion’ schemes where threat actors will steal data before encrypting it and then threaten to make it public as a way of exerting further pressure on the victim to pay up (and also effectively rendering even the most robust back-up strategy a moot point!).
- The Pandemic is a Ransomware Accelerant: If anyone has benefited from the global pandemic as much as face mask manufacturers, it’s undoubtedly ransomware operators and their growing network of affiliates. The criminal organizations behind these attacks thrive on the chaos and uncertainty in general and the current pandemic has produced a perfect breeding ground for exploiting remote workers who do not have access to the same security controls that can be found within their corporate networks.
The points above address aspects of ‘the who, why, and how’ behind these attacks. But what steps should organizations take to protect themselves? Here are a few best practices that we recommend to our customers:
- Evolve Traditional Security Testing: If you are currently employing regular penetration tests and vulnerability assessments, know that these are useful but not enough. These kinds of tests focus on checking the permeability of a system’s outer defense but not what is happening right now, as you read this blog post. These procedures remain necessary, yes. Do they provide a comprehensive and actionable view? Unfortunately, no. Be sure to evolve these practices, we wrote more on the topic on the following whitepaper: It Is Time to Evolve Security Testing.
- Prioritize Zero Trust & Network Microsegmentation: There’s a reason why Zero Trust is one of the hottest topics in network security today. Not only does a Zero Trust provide a framework for providing ‘least-privilege’ access that continuously validates a user’s devices and entitlements, but it also helps cloak the network edge itself which can go a long way towards limiting the scale and scope of an attack. Keep in mind the ultimate goal of a Zero Trust strategy is to achieve a state of zero compromise. In addition to employing this strategy, be sure to measure its degree of success continuously and intentionally so you can use that intelligence to build an increasingly resilient organization.
- Listen to All Your Threat Signals: Ransomware is a dynamic threat that requires a modern and proactive approach. Consider embracing the principles of Continuous Compromise Assessment which turns the conventional security paradigm of keeping attackers out of the network on its head and instead assumes that the network is already compromised until proven otherwise.
Want to learn more? Visit our Ransomware Resource Center.