
Advisory Alert: PowerSchool Data Breach
Reading Time: 4 minsThe December 2024 breach of a student information software solution for K-12 educational institutions, PowerSchool, leaves us asking: what can we learn from it?

Reading Time: 4 minsThe December 2024 breach of a student information software solution for K-12 educational institutions, PowerSchool, leaves us asking: what can we learn from it?
Reading Time: 4 minsDetecting and stopping attacks using anonymization techniques can give your team the upper hand against cyber criminals — but how do attackers use anonymization and how can we defend against it?
Reading Time: 4 minsLumu has worked hand-in-hand with MSPs throughout a year that consolidated the need for cybersecurity in the role of MSPs.
Reading Time: 5 minsLumu’s 2024 SecOps advancements focus on automation and smarter threat detection, with new features that set the stage for a more proactive cybersecurity approach.
Get the latest cybersecurity articles and insights straight from the experts.

Reading Time: 4 minsDetecting and stopping attacks using anonymization techniques can give your team the upper hand against cyber criminals — but how do attackers use anonymization and how can we defend against it?

Reading Time: 4 minsThe December 2024 breach of a student information software solution for K-12 educational institutions, PowerSchool, leaves us asking: what can we learn from it?

Reading Time: 4 minsLumu has worked hand-in-hand with MSPs throughout a year that consolidated the need for cybersecurity in the role of MSPs.

Reading Time: 5 minsLumu’s 2024 SecOps advancements focus on automation and smarter threat detection, with new features that set the stage for a more proactive cybersecurity approach.
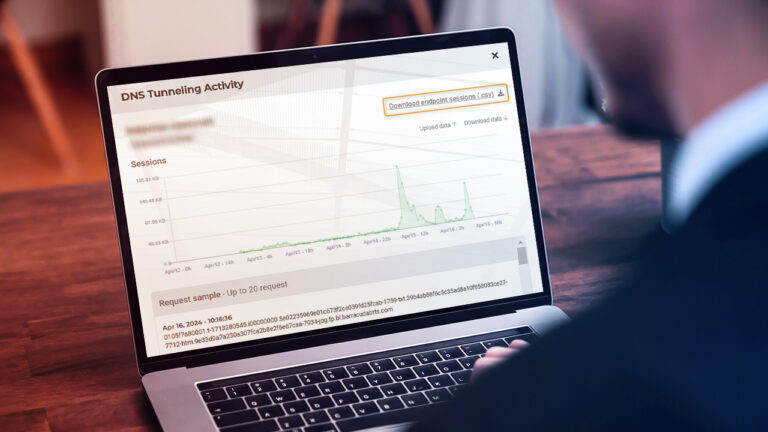
Reading Time: 7 minsThis is the story of a serious DNS tunneling attack on a multinational insurance provider — discover the importance of DNS tunneling detection, what we found when we investigated the attack, and how we contained it.

Reading Time: 4 minsDiscover the top insights from Lumu’s pre-conference workshop at IT Nation Connect, where MSP leaders shared actionable advice on building effective cybersecurity stacks, pricing services, and managing client success

Reading Time: 2 minsAs we move into 2025, AI-driven evasion and autonomous threats will redefine cybersecurity, pushing organizations to adapt to new risks and defense tactics.

Reading Time: 7 minsEndpoint Detection and Response (EDR) has a critical role in most companies’ security setup, but cybercriminals are mastering EDR bypass tactics. How can we defend against them?

Reading Time: 5 minsLumu’s Compromise Report for 2024 uncovers surprising information about how infostealer malware has increasingly targeted US organizations, local government, and education establishments.

Reading Time: 4 minsFor MSPs to proactively protect their clients they need good intelligence, such as the trends and tendencies in cyber threats revealed in the Lumu Compromise Report 2024.

Reading Time: 6 minsExplore DPI’s limitations in network security and discover how Lumu’s cloud-native, metadata-driven approach provides essential visibility and threat detection.

Reading Time: 3 minsLumu’s new Compromise Report 2024 reveals the greatest current cybersecurity trends and how to defend against them. We look at the top three takeaways to watch out for in the report.

Reading Time: 6 minsDiscover how Lumu’s Playback feature improves visibility and efficiency while addressing the limitations of traditional SIEMs in handling vast amounts of network data.

Reading Time: 4 minsRansomHub is a new ransomware group offering Ransomware as a Service that has already encrypted and exfiltrated data from at least 210 victims. How does RansomHub bypass defenses and how can you defend against it?

Reading Time: 7 minsMario Lobo, Cybersecurity Specialist at Lumu Technologies, recently attended DEFCON – a hacker convention held annually in Las Vegas, Nevada – and he highlights his big takeaways.
© Lumu Technologies All rights reserved. | Legal information.