The abundance of cybersecurity data makes it difficult to understand what is truly relevant. Much like how the Illumination Process sifts through metadata to provide actionable insights, we’ve pored through the most recent data breach reports to paint a clear picture of how cyber attacks are affecting enterprises in the 2020 Compromise Flashcard.
How did the attacker get in?
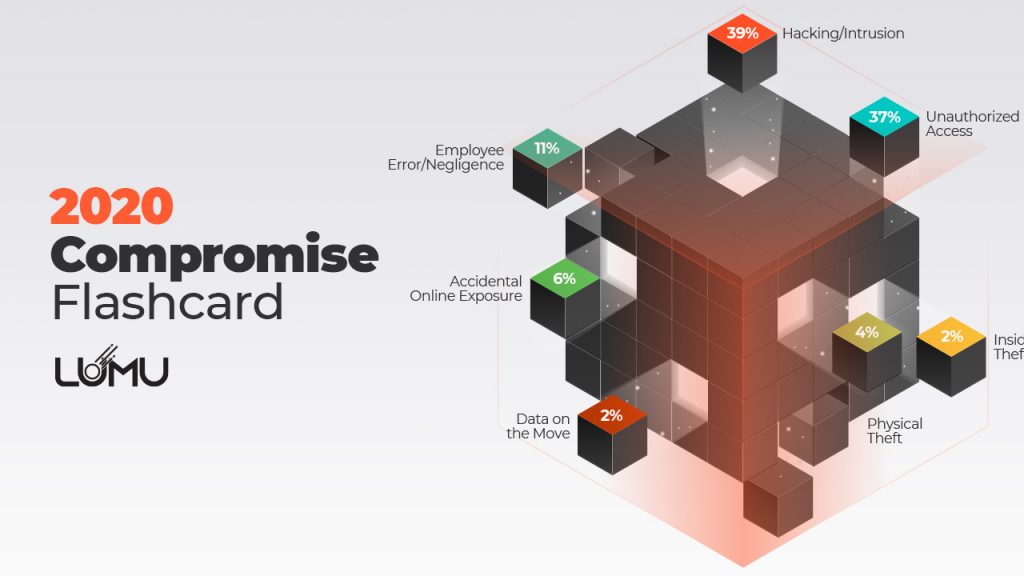
It should be no surprise that as in previous years, the most common method of entry for breaches was hacking/intrusion (ITRC 2019 End-of-Year Data Breach Report). This category, accounting for 39% of all breaches, includes breaches through phishing, ransomware/malware, and skimming. The second-largest category, unauthorized access (37%) continued its growth trend from 2018, largely due to the increased prevalence of credential stuffing. The remaining 24% of compromises resulted from employee negligence, accidental exposure, data on the move, physical theft, and insider theft.
How long did they dwell?
The average time to detect a compromise increased to 206 days in 2019 (IBM Cost of a Data Breach Report 2019). A further 73 days were required to contain these threats. Interestingly, these figures varied greatly depending on their region or industry. For example, German organizations required 170 days to identify and contain compromises, compared to 381 days in the Middle East. Financial and banking organizations performed somewhat better than most, requiring 233 days while healthcare providers performed worst, requiring 329 days.
What did they get out?
The number of breaches increased in 2019 and so did the number of records exposed. In total, 870 million records were exposed, of which 165 million are considered to be ‘sensitive records’. Financial institutions were attackers’ main source of sensitive records, accounting for 101 million exposed records.
The impact and cost
Cybersecurity spending has increased by 44% since 2014, and yet we continue to see an increase in the number of breaches and records exposed. In 2019 the number of breaches increased by 17%. The impact of each breach also increased, especially in the USA, where the average cost of a breach amounted to 8.6 million dollars, double the global average.
Lumu’s Take
From the data, it is clear that no industry is safe from breaches. Even the industries that were fastest to detect and contain compromises were still unacceptably slow. Industries subject to the most stringent regulations are failing to protect sensitive data. Complying with the minimum demands of regulators or comparing yourself with industries that are fairing worse, is far from enough.
Despite the direct correlation between dwell time and ransomware attacks, the time required for compromise detection is only increasing. Threat actors are constantly evolving their tactics, techniques, and procedures to ensure better deliverability. There needs to be a tactical and mindset change if strategists and operators are going to be able to turn around the hard reality our industry is up against.
Your call to action
As Bruce Schneier said in his talk at the Illumination Summit, “We’re spending about as much as we should, we’re just spending it badly.” Years of spending based on trends and buzzwords have not been able to reduce the frequency or severity of compromises. The only way to prevail is to challenge the status quo. Cyber resilience can only be improved if we start measuring compromise intentionally and continuously.
For more facts and figures, be sure to check out the Lumu 2020 Compromise Flashcard infographic.