Table of Contents
Lumu Autopilot represents a digital twin of your SecOps team that keeps your cybersecurity operations running 24/7, regardless of where you are. It fosters orchestrated, collaborative intelligence between human and machine analysts, empowering teams to stay ahead—around the clock. In short, Lumu Autopilot offers autonomous cybersecurity for smarter, faster, and more effective security operations.
Why Autonomous Cybersecurity Is Needed
More Devices, More Data
By 2025, the number of connected, digital devices will exceed 75 billion. Many of these devices are connecting to corporate networks via ever-faster connections. Additionally, they include a wide range of device types including IoT devices and OT (Operational Technology) that aren’t covered by traditional cybersecurity measures like EDRs.
The result of this proliferation of devices is that cybercriminals’ attack surface is larger than ever. It also means that the amount of data produced is much larger. So, while there are more needles, the haystack they hide in keeps growing exponentially larger—and human hands are simply not enough to look through it all.
Demand for Cybersecurity Analysts
Currently, there are over 3.5 million unfilled job openings in cybersecurity. Finding, training, and keeping cybersecurity talent is an increasingly difficult task. What’s more, those currently working in cybersecurity frequently cite high rates of burnout due to the challenges they face in combating cybercrime.
Lumu Autopilot emerges as an autonomous cybersecurity solution that not only helps Secops teams more efficiently manage their current workloads, but also future-proofs cybersecurity operations for the increasing demands of the future.
The Challenge of 24/7 Monitoring Mandates
Frameworks such as GDPR, HIPAA, and CMMC pose significant challenges for organizations, demanding continuous monitoring of their digital environments. Compliance requires not only the ability to protect data around the clock but also to swiftly respond to security incidents. This level of vigilance stretches resources and places immense pressure on cybersecurity teams, often leading to burnout.
How Lumu Autopilot Works
Lumu Autopilot is like a virtual version of your SecOps team that works within the Lumu portal to manage incidents for you. This cybersecurity ‘digital twin’ relies on 3 ingredients:
- Lumu’s Network Analysis: Lumu already collects a range of network metadata and analyzes it in real time. This system, called the Illumination Process, detects confirmed compromise incidents that have bypassed traditional cybersecurity defenses.
- AI-Powered Playbooks: Because of our 5 years’ experience in collecting metadata related to cyberthreats, Lumu has crafted AI-powered playbooks that combine the best practices of human cybersecurity analysts with machine speeds
- Integrations for Automated Response: Lumu offers over 125 integrations with 3rd party cybersecurity tools. Data collection integrations let the Illumination Process ingest network metadata collected by those tools. Response integrations let Lumu Autopilot coordinate responses to detected incidents and know which actions have been taken by the entire cybersecurity stack.
Taking these ‘ingredients’ into account, Lumu Autopilot decides whether the incident needs to be monitored, muted, closed, or escalated. What’s more, this process can manage multiple incidents at the same time, while learning from similar incidents all across the globe.
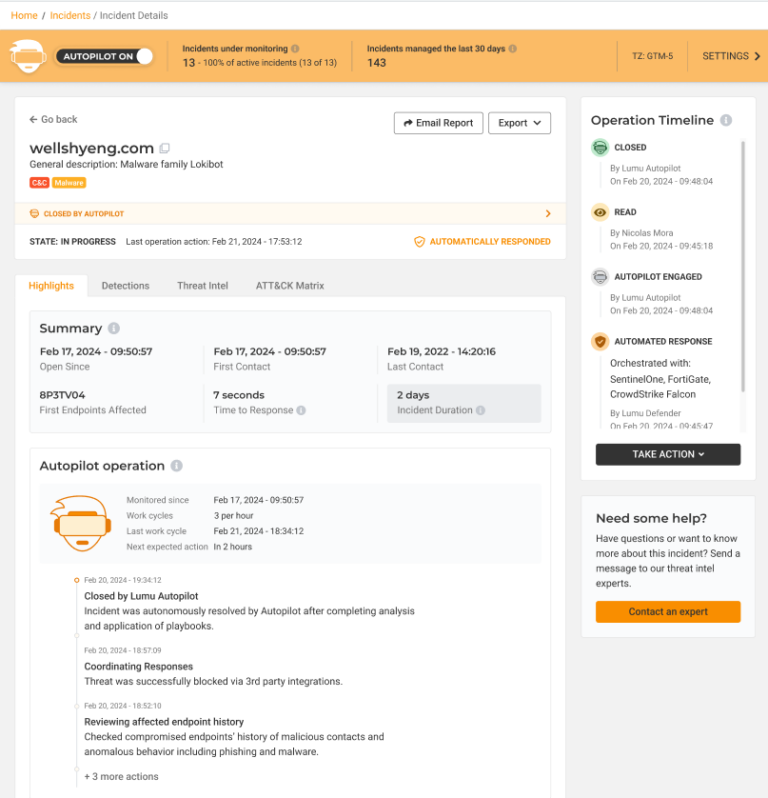
Key Benefits of Lumu Autopilot
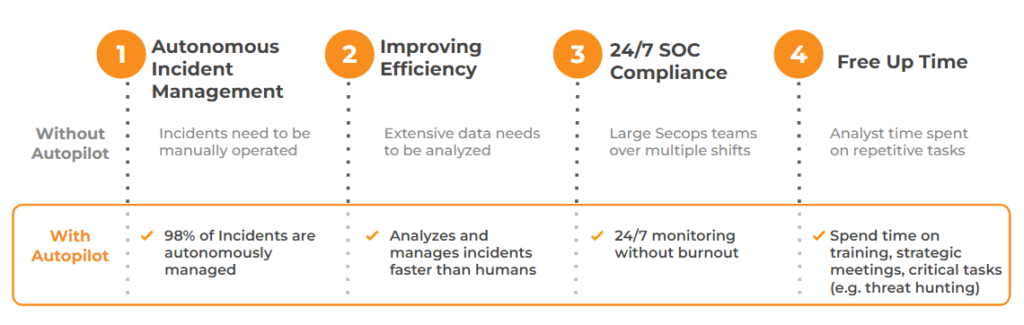
Automated Cybersecurity Incident Management
Lumu Autopilot excels in managing incidents, ensuring that cybersecurity threats are addressed promptly and efficiently. By automating the detection, analysis, and response to incidents, it draws from incident best practices and closes the window of opportunity for attackers.
Improving Efficiency
By leveraging AI-powered playbooks and extensive integrations, Lumu Autopilot significantly streamlines cybersecurity operations. Autopilot ingests and correlates vast amounts of data faster than is humanly possible while reducing the scope for human error.
24/7 SOC Compliance
Autopilot is your always-on SecOps team, simplifying compliance with round-the-clock monitoring mandates without overburdening your staff. This perpetual vigilance ensures that threats are identified and mitigated at all hours, providing a level of security that is challenging to maintain manually.
Free Up Analyst Time
Perhaps one of the most crucial benefits, Lumu Autopilot frees cybersecurity analysts from the demands of incident monitoring and clamoring alerts. By automating routine tasks, analysts can dedicate their time and expertise to more strategic endeavors, improving security protocols, and engaging in proactive threat hunting.
Where Human Insight Meets Autonomous Cybersecurity
Automation and Artificial Intelligence offer undeniable benefits in efficiency and scalability, but there are realms within cybersecurity where human intuition, creativity, and ethical judgment remain irreplaceable. The development of security strategies and ethical decision-making in ambiguous situations are areas where the nuanced understanding and adaptability of human experts are crucial.
While Lumu Autopilot significantly enhances cybersecurity operations, it acts as a complement to, rather than a replacement for, the invaluable insights provided by cybersecurity analysts. Our aim is that this “collaborative intelligence” will lead to more fulfilling work for cybersecurity professionals, as well as better cybersecurity operations as a whole.
While Autopilot takes over, human analysts focus on tasks such as
- Proactive Threat Hunting: Actively search for potential security threats and vulnerabilities within the network environment.
- Threat-Informed Defense & Strategic Planning: Collaborate with stakeholders to develop and refine overarching security strategies aligned with organizational goals and risk tolerance.
- Deep Dive Investigations: Conduct in-depth investigations into complex security incidents to uncover root causes and develop mitigation strategies.
- Incident Response Planning: Lead the development and documentation of incident response plans for rapid and effective response to security incidents.
- Continuous Learning and Skills Development: Invest time in ongoing learning to stay abreast of evolving cyber threats and industry best practices.
Let Autopilot Take Over
Transforming Cybersecurity Operations
SecOps teams already face significant challenges in processing and analyzing increasing amounts of data as well as keeping their teams staffed with qualified cybersecurity talent. These challenges are only set to increase in the immediate future. With Lumu Autopilot, SecOps teams will be equipped with the technology to meet these challenges and then some. Autopilot will also help them to do so around the clock and comply with 24/7 monitoring requirements.
To sum up, Lumu Autopilot represents a leap forward in autonomous cybersecurity incident management. By automating routine tasks and freeing up cybersecurity professionals to focus on strategic initiatives, it offers a robust solution to the growing demands and volumes of cyber threats.




