As a security researcher, I have the opportunity (and distinct pleasure) of speaking to hundreds of vendors and customers per year on the trends in cybersecurity. We conduct research, poll end users, and try to make sense of a very complex and evolving market. Through it all, one of the areas that we do not really discuss enough is how many progressive business leaders are shaking up the way that they have operated cybersecurity for decades.
More than ever before, members of the c-suite need to understand the need for security—this certainly is not optional. With continued regulatory pressures and vendor due diligence, prioritizing resources to address those concerns will always be part of the enterprise’s spending calculus. But are they spending resources and dollars on solutions that actually matter?
I recently had the opportunity to speak with Ricardo Villadiego and the team at Lumu again. I was already impressed with their solution, which addresses the specific question about investing in security solutions that will have the greatest impact. Now, Villadiego and the team have added the MITRE ATT&CK® framework to their Continuous Compromise Assessment™, using the metadata already available in the enterprise network to give a constantly changing and thorough evaluation of the security status of the enterprise.
They have shifted the paradigm—they assume that a company has already been compromised. Instead of evaluating security using a scatter approach, casting a wide pattern in hopes of hitting everything, Lumu takes a surgical approach to security investment, identifying specific areas of weakness and providing insights to repair areas in which the company is most likely to experience a breach. As the environment improves/evolves or new technologies (for the good guys and the bad guys) change the threat landscape, the continuous assessment allows businesses to shift and retarget priorities and resources to react to emerging threats.
Incorporating the MITRE ATT&CK® framework through the Lumu Portal, Lumu created an Enterprise ATT&CK Matrix that consists of 12 columns representing Tactics (the adversary’s objective), which are expanded granularly into specific known adversarial methods. Techniques and sub-techniques represent steps an attacker would typically follow when attacking your infrastructure. Depending on the adversary’s objective, multiple techniques can be applied, but not all tactics need to be employed (see picture provided by Lumu).
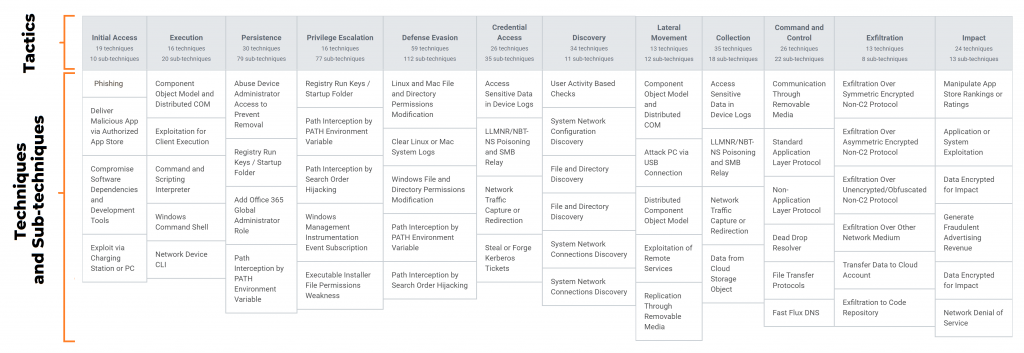
While there are plenty of regulatory frameworks that the enterprise can use to evaluate itself, the MITRE ATT&CK® framework is often considered one of the best and most robust. Lumu is creating actionable areas for improvement by using the MITRE framework for each compromise that it finds. This allows the enterprise and security teams to consider the following:
- Operationalizing the MITRE ATT&CK® framework into your incident response playbooks. This is a fantastic way for security teams to increase their enterprise security maturity almost instantly. The MITRE framework is accepted by many organizations and will likely reduce compliance and vendor due diligence costs. At the very least, it will bring actionable responses to address legitimate security concerns in the environment.
- Understanding how bad actors are operating in your enterprise. Lumu, with the addition of the MITRE ATT&CK® framework, offers insight into the weak points of enterprise security systems and provides a picture of how bad actors are trying to exploit those weak points. A security team can use this intelligence to remediate risks and prioritize improving those systems before an attack occurs, reducing overall security risks.
- Planning and executing red/blue team cyber preparedness activities. Some regulatory compliance and vendor due diligence controls require third-party assessments of the enterprise’s security. Lumu can evaluate where red teams should concentrate their efforts and give direction as to where blue teams need to prepare and repair.
- Creating and evaluating the enterprise security investments. As I mentioned, one of the most brilliant aspects of the Lumu solution is providing real (not sort of real, not contrived, not “this would be nice”) data to security teams and executive decision-makers on where to invest resources and dollars to have the greatest impact. The MITRE ATT&CK® framework adds additional data points to the equation, with specific recommendations for how best to resolve and repair.
There are plenty of security solutions for the enterprise dollar and many that do a great job. In fact, some of them will likely integrate with Lumu to solve some of the issues that they discover—Lumu never claims (nor does it try) to solve all of your security problems. Instead, it does what it does: finds where you have significant security vulnerabilities and makes recommendations on how best to solve them. Very few other tools (if any) work the way that Lumu does, and adding the MITRE framework only increases the value of the Lumu solution to the security teams and decision-makers.
As an industry, security vendors need to continue to improve their efforts to educate their users—how security works, why things are a risk, and how best to solve those problems. Lumu does this, and does it in ways that security practitioners and executives can understand and utilize. Lumu is a company that is enabling organizations to really look at what they were doing, strip off what didn’t work, and effectively utilize tools at their disposal for a proficient security program.




