Table of Contents
Threat-informed defense is a strategic approach to cybersecurity that combines threat intelligence with traditional security measures and threat analysis. It helps organizations protect their networks, systems, and data by proactively identifying potential threats before they can cause damage or disruption. By utilizing threat intelligence and threat analysis, threat-informed defense allows organizations to anticipate malicious attacks and take proactive steps to mitigate risk. This approach provides better visibility of the attack surface, enabling more effective response strategies should an attack occur. With threat-informed defense in place, organizations are better prepared to address cybersecurity challenges and better able to allocate their resources.
What Is Threat-Informed Defense?
According to Jon Baker, Co-Founder and Director of the Center, Threat-Informed Defense (TID) is the systematic application of deep understanding of adversary tradecraft and technology to improve defenses.
Baker elaborates that “Threat-Informed Defense is both a set of practices as well as a way of thinking. In cybersecurity, it builds on a foundation of sound IT security building blocks including IT asset management, configuration, and vulnerability management as well as the deployment of essential controls.”
The Center for Threat-Informed Defense
The Center for Threat-Informed Defense (The Center) plays a key role in advancing the art and practice of threat-informed defense, globally. The Center is a research and development organization focused on improving the effectiveness of cybersecurity defenses through the use of threat intelligence and other forms of context-specific information. As a non-profit organization operated by MITRE Engenuity, the Center provides public resources on the practical application of threat-informed defense.
The Center is responsible for
- Developing new methods and tools for collecting, analyzing, and disseminating threat intelligence.
- Evaluating the effectiveness of different threat-informed defense approaches and techniques.
- Identifying best practices for integrating threat intelligence into existing security processes and systems.
- Collaborating with industry, academia, and other stakeholders to advance the state of the art in threat-informed defense.
The Advantages of Threat-Informed Defense
Freely-Available Resources
Through the MITRE Corporation and the Center, businesses of all sizes have access to the tools needed to operate a threat-informed defense strategy. For example, organizations might already be aware of the MITRE ATT&CK Matrix, which is a threat-oriented model and framework for understanding, preparing for, and responding to cyber threats. The Center releases public research, guides, and case studies on practical applications of MITRE ATT&CK® that organizations can follow.
Improve Efficiency and Effectiveness
By focusing on the threats that are most likely to be encountered, threat-informed defense can help organizations prioritize their resources and implement more effective defenses. In addition, organizations can avoid wasting resources on ineffective or unnecessary measures by basing their defenses on a detailed understanding of the threats they face.
Starting point for Risk-based cybersecurity
A Risk-based cybersecurity strategy is a broad term that refers to any approach that involves evaluating and prioritizing risks in order to make informed decisions about how to allocate resources and manage risk. A threat-informed defense strategy focuses on the specifics, using information about the tactics, techniques, and procedures (TTPs) of adversaries to inform the design and implementation of defensive measures.
Improved Decision-making at a strategic and daily level
By understanding how threat actors are most likely to operate, organizations can develop more effective response strategies to specific threats. In addition, threat intelligence can provide a better picture of the threat landscape, which can help organizations optimize their security posture and identify areas where they are most vulnerable.
Improved Resilience
By using threat-informed defense to anticipate and prepare for potential threats, organizations can become more resilient to attacks and other security incidents.
How Organizations can Get Started with Threat-Informed Defense
“Implementing a threat-informed defense starts with understanding the threats that are relevant to your organization and then aligning your defenses to those threats. Don’t get overly concerned with developing the perfect threat model. Teams can start with a single ATT&CK technique and incrementally expand from there.“ – Jon Baker.
Step 1: Identify Relevant Threat Types
Determine the types of threats that could potentially affect your organization, including both internal and external threats. Try to stay up to date with the latest attacks that are targeting similar organizations in your industry, and geography. This may include threats such as ransomware, phishing, data breaches, insider threats, and more. The MITRE ATT&CK® matrix can be used to help identify and categorize these types of threats.
Step 2: Monitor Your Network
Actively monitor your network to identify malicious activity and then identify the TTPs associated with that activity. First, mitigate and remediate any active compromises. Prioritize addressing the techniques that adversaries are or have successfully used to compromise your organization.
Step 3: Map Your Security Stack to Adversarial TTPs
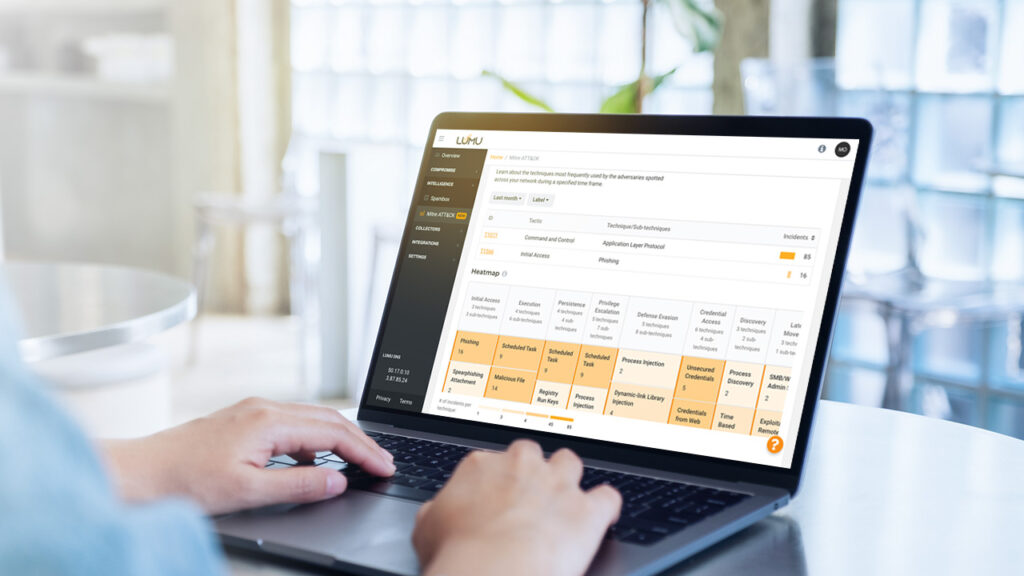
Identify which tools in your stack address the adversarial techniques in steps 1 and 2 above. Consult resources provided by the ATT&CK® Matrix and the Center to get up to date on best practices in addressing these threats. Identify any gaps in your defenses or areas where more defense-in-depth is necessary. You can find examples of how the Center mapped cloud-native security controls to MITRE ATT&CK on their GitHub.
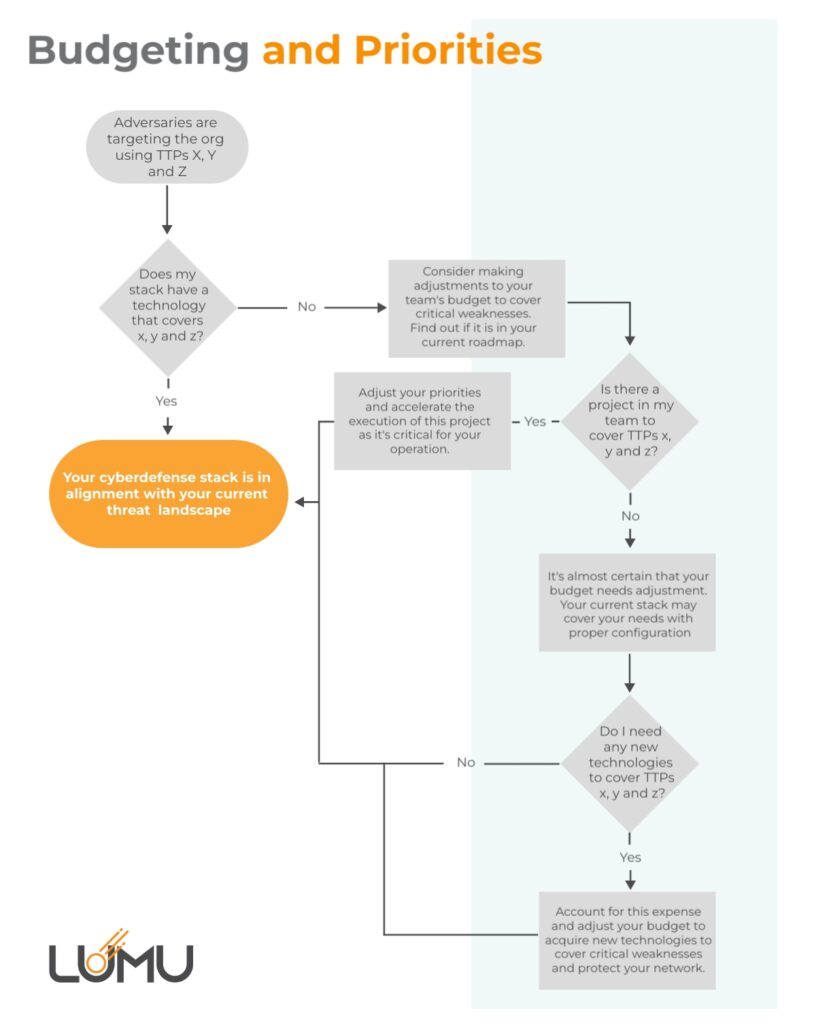
Step 4: Make Appropriate Adjustments to Your Cybersecurity stack
Invest in those areas of your security operation where you are most vulnerable. Make improvements where necessary and verify that existing cybersecurity tools are delivering on their promises. Make adjustments to your budget if critical vulnerabilities cannot be covered under your existing strategy.
Step 5: Continuous Improvement
Continue to monitor and assess your network infrastructure for internal threats and vulnerabilities as well as external developments in the threat landscape.
How Threat-Informed Defense Can Be Complemented and Empowered
“Test and evaluation is a critical component to a threat-informed defense. Leverage automated testing to emulate adversary behaviors and validate that your defenses are properly configured.“ – Jon Baker.
Test and Validate the effectiveness of the strategy
Regularly testing and validating the effectiveness of the threat-informed defense strategy can help organizations to identify weaknesses and areas for improvement. This may involve conducting simulated attacks or penetration tests to identify vulnerabilities, or conducting regular reviews of the organization’s security posture.
Review and Update the strategy
As the threat landscape evolves, it is important to periodically review and update the threat-informed defense strategy to ensure that it remains effective and relevant. This may involve adjusting the focus of the strategy based on new or emerging threats, or making changes to the defensive measures that are in place.
Integrate Threat Intelligence
Incorporating high-quality, timely, and relevant threat intelligence into the threat-informed defense strategy can help organizations to better anticipate and prepare for potential threats. This may involve subscribing to threat intelligence feeds, participating in information-sharing initiatives, or establishing relationships with trusted sources of intelligence.
Implement strong security controls
A strong security posture is essential to effectively defending against cyber threats. This may involve implementing controls such as firewalls, intrusion detection and prevention systems, and access controls to protect against external threats, as well as implementing measures such as employee awareness training and data loss prevention controls to mitigate the risk of internal threats.
A threat-informed defense strategy is a proactive and comprehensive approach to cybersecurity that can help organizations protect their networks, systems, and data. By utilizing threat intelligence and threat analysis, TID allows organizations to anticipate malicious attacks and take steps to mitigate risk. This approach provides better visibility of the attack surface, enables more effective response strategies should an attack occur, and helps prepare organizations for future cybersecurity challenges. Lumu’s MITRE ATT&CK Global Matrix is a tool that can help you operationalize TID within your organization. Our partners over at Fluid Attacks have also provided their insights into the role played by threat-informed defense when performing security testing and assessments. Visit the Center for Threat-Informed Defense for more resources on Threat-informed Defense including mapping security tools to threats.