Table of Contents
In February 2022, CISA, alongside security agencies from the United States, the United Kingdom, and Australia, released a report titled 2021 Trends Show Increased Globalized Threat of Ransomware. Our Ransomware Flashcard 2022 gives you some stats on the trends that inform this expectation, plus observations from our own system.
The Vicious Cycle
According to data from CyberEdge, ransom payers have been increasingly recovering their data (up from 19.4% in 2018 to 71.6% in 2021). This in turn has led businesses to be more willing to pay for the recovery of data (up from 38.7% in 2018 to 57% in 2021). As a consequence, threat actors are more incentivized to launch ransomware attacks and can invest more into their ransomware efforts, leading to increased attacks (up from 55.1% in 2018 to 68.5% in 2021).
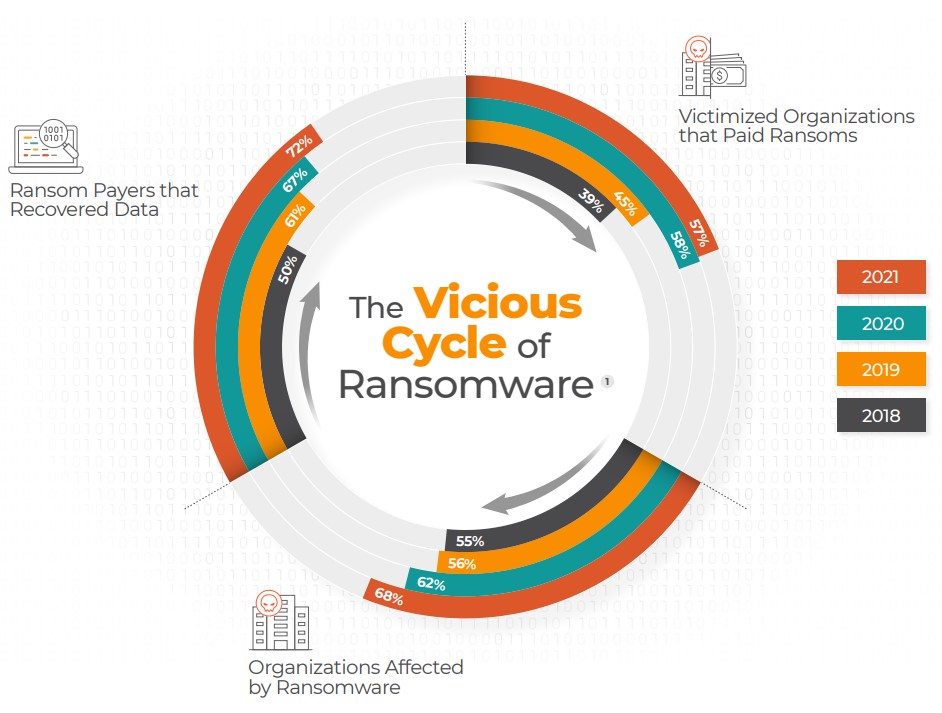
Security agencies have long advocated for businesses to refuse to pay ransoms. Unfortunately, it would appear that organizations haven’t taken—or haven’t been able to take—such a stance. As a result, a market has been established and threat actors encouraged. The losses from such ransomware attacks have been so severe that cyber insurers have had to cut the amounts they cover and in some cases have stopped offering policies that cover ransomware. Increasingly, the best course of action for businesses isn’t to mitigate its cost through insurance, but rather to break the cycle by not getting hit in the first place.
Small and Medium-sized Business (SMB) Perceptions
Managed Security Providers (MSPs) are often on the front lines when it comes to dealing with ransomware. As such, it isn’t too surprising that MPS are overwhelmingly (84%) ‘very concerned about ransomware’. SMBs, however, have a very different outlook with only 30% claiming to be very concerned.
As we mentioned in our cybersecurity prognosis for 2022, large enterprises will continue to be the victims of sophisticated attacks. However, new, less skilled threat actors will enter the market due to the democratization of ransomware through initial access markets, malware-as-a-service, and ransomware chains. These groups will have SMBs squarely in their sights.
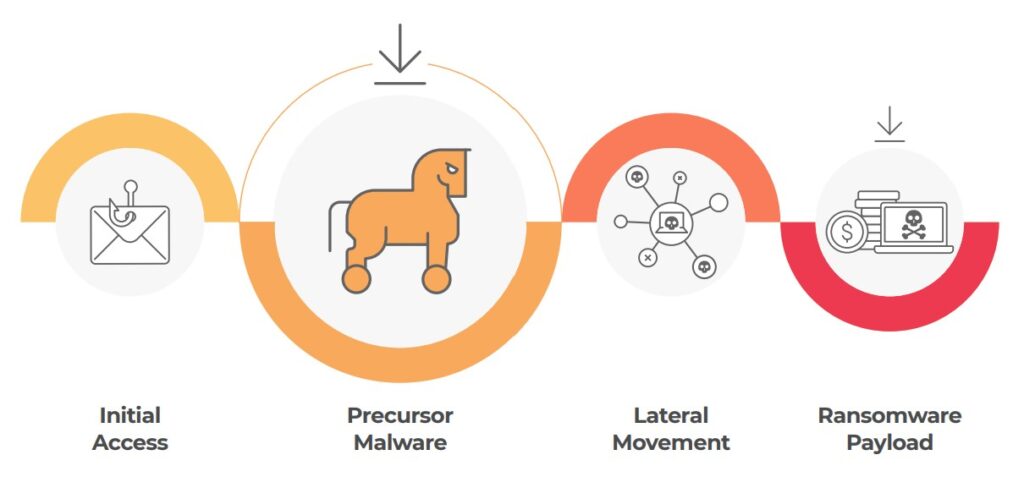
Ransomware Precursor Malware
Ransomware doesn’t appear out of the blue. Precursor malware is used by threat actors to spread laterally and escalate access before a ransomware package is deployed. Some of these malware strains have evolved from their original purpose as banking trojans, others are being created explicitly to deliver ransomware. All need to be taken seriously.
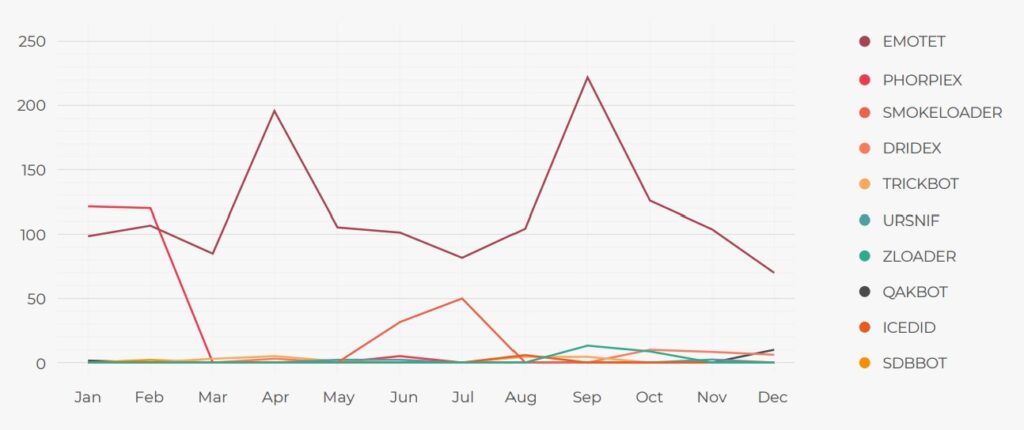
Threat actors are constantly creating new domains—sometimes using algorithms—for the remote command and control of these types of malware in order to avoid detection. In 2021, Lumu collected 21 820 764 new confirmed IoCs that were related to ransomware precursor malware.
The precursor malware whose contacts were most often detected by Lumu was Emotet, which isn’t surprising since it’s one of the world’s biggest and most resilient botnets. Emotet was originally a banking trojan, but has recently adapted to form a ransomware chain with Trickbot that can result in the deployment of Ryuk ransomware.
Conclusion
National security organizations agree that the threat posed by ransomware will only increase in 2022. Unfortunately, the ransomware landscape is due to evolve even more given the precarious geopolitical situation the world finds itself in. We encourage all organizations as well as the public at large to bear in mind that any business can be a target. Cybersecurity operators will still have to efficiently stop incoming attacks, while also being prepared to swiftly detect, mitigate, and remediate the compromises of all types that are getting through.
View the full Ransomware Flashcard 2022 for more insights and statistics into the state of ransomware.




