Table of Contents
SLED (which stands for State, Local, and Education) organizations face unique cybersecurity needs and challenges. This sector includes a wide range of entities, with State government agencies, city or municipal governments, county governments, public school districts, universities, community colleges, and various educational institutions all falling under the SLED umbrella.
While this category includes a diverse range of entities, what sets SLED cybersecurity needs apart is the unique combination of regulatory challenges, resource limitations, and diverse networks that these entities face. State agencies, local governments, and schools grapple with tight budgets, making it challenging to invest in robust cybersecurity measures and cybersecurity talent. Furthermore, the broad range of services provided by SLED organizations results in complex network environments that require tailored solutions to protect sensitive data and ensure the continuity of essential services. Understanding and addressing these intricacies is crucial for effectively safeguarding SLED entities against cyber threats.
What Does a Typical SLED Cybersecurity Stack Look Like?
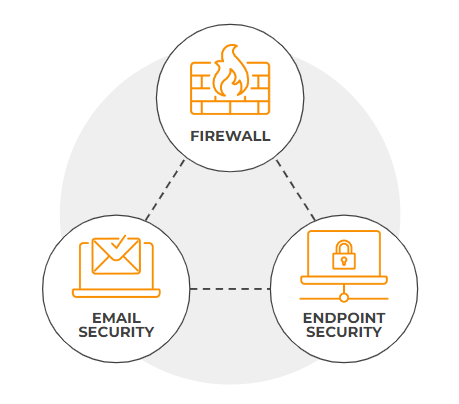
Every SLED Organization already has some cybersecurity protections in place. The key elements of this stack are a Firewall Solution, Email Security, and an Endpoint Security Solution. While these tools are essential components of a cybersecurity stack, achieving comprehensive protection requires the integration of network visibility and automation to proactively identify evolving threats, they have their shortcomings and are known to be easy targets for cyber criminals.
Attackers have been evading these tools’ protections for years, and they are not enough on their own.
- 94% of the most common EDR platforms were found to be vulnerable to at least one common evasion technique. That means most EDRs are easily bypassed.
- A growing number of firewall vulnerabilities are used by threat actors to bypass defenses. There are many examples of Firewall evasion and escalation of privileges which ultimately results in compromise.
- While almost every organization has some form of email security and training in place, Email is still the most common point of initial access for cyber adversaries, with email being implicated in 90% of attacks.
- Many SLED organizations employ a “set and forget” policy approach in their cybersecurity measures. This static strategy fails to evolve at the speed of attackers’ capabilities, creating vulnerabilities. For instance, the SLA (Service Level Agreement) for policy adjustments often exceeds 36 hours, providing ample time for adversaries to exploit these gaps and cause significant harm.
How Are Adversaries Able to Evade Traditional SLED Defenses?
- Risky IoT devices: IoT devices (internet-connected devices such as security cameras, smart home devices, and even traffic control systems) are a common point of entry for attackers to gain access to the network—and there is no EDR technology that can be deployed on endpoints.
- Various Malware Strains: Many malware strains are designed to evade EDRs and Firewalls, like polymorphic malware, file-less malware, APT threats, and encrypted malware.
- Phishing: EDR solutions and firewalls may have difficulty distinguishing between legitimate and malicious activity if the user willingly provides sensitive information obtained through phishing attacks, especially those developed through social engineering attacks.
- Social Engineering Attacks: A well developed social engineering attack can easily target employees to make it past your email security tools. Without the ability to observe behavioral patterns in the network, social engineering attacks can be successfully carried out.
- Lateral Movement: without visibility into the communication patterns and behaviors between different endpoints and systems (iot, roaming devices, servers) you are unable to see attackers moving across the network. Lateral movement is a technique used by attackers to navigate through a network after gaining initial access, with the goal of escalating privileges and reaching sensitive assets.
The Importance of Your Network
Any attack needs to use an organization’s network in order to carry out its objectives. According to a report by leading analyst firm Forrester, “NAV technology provides intelligence on, correlation with, and visibility into all aspects of the network, from endpoints to the cloud.” Without network visibility and analysis, it’s very difficult to make decisions about an organization’s state of compromise.
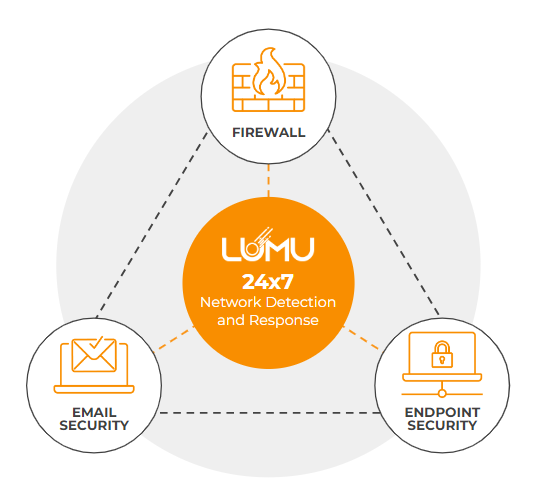
So, how do you leverage the critical threat intelligence in your network? Lumu monitors the signals already being produced by your network in real time, 24-7. We compare this data with the most up-to-date database of compromise indicators to determine if adversaries have already made their way into your network.
Lumu goes beyond detection by integrating the various elements of the cybersecurity stack. This means that Lumu can collect signals from other elements of the cybersecurity stack, for example an email security solution. By analyzing these signals alongside other network signals, we can determine in real time if a threat is present. Secondly, these integrations allow us to automate response against the threat, for example by instructing the existing firewall solution to block the threat.
Employ a 24/7 Cyber Analyst
Many SLED Organizations struggle to recruit, train, and retain cybersecurity talent necessary to employ the modern cybersecurity practice required by regulations and governmental standards. However, Lumu acts as an extra team member: an analyst that never takes a sick day, goes on holiday, or accepts a higher-paying job offer.
Challenges in Cybersecurity for SLED Organizations | Your 24-7 Cyber Analyst |
Vulnerable to Evasion Techniques: Common cybersecurity tools like EDRs and firewalls are susceptible to evasion, leaving organizations exposed. | Continuous Threat Detection: Lumu leverages AI and advanced analytics to detect threats that traditional tools miss, ensuring comprehensive protection. |
Limited Visibility of Network Threats: Standard tools may not detect activities like phishing, malware, and lateral movements. | Continuous Network Monitoring: Lumu provides continuous monitoring of the network, identifying and classifying malicious activities in real-time. |
Integration and Management of Multiple Tools: SLED organizations often deal with the complexity of managing and integrating multiple cybersecurity tools. | Seamless Integration with Existing Tools: Lumu’s platform integrates with existing cybersecurity tools, enhancing their capabilities and simplifying management. |
High Alert Volumes and False Positives: Organizations struggle with the sheer volume of alerts, many of which are false positives, creating a large workload for staff to deal with. | Accurate and Efficient Incident Response: Lumu’s platform minimizes false positives and automates responses, allowing for more accurate and efficient threat management. |
Need for Manual Processes: Existing cybersecurity practices often require extensive manual intervention, draining resources. | Automated Incident Creation and Response: Lumu automates the detection, analysis, and response to cyber threats, reducing the need for manual processes. |
SLED Cybersecurity Success Stories
Don’t take our word for it. Hear from these SLED organizations that solved their most critical cybersecurity challenges with Lumu’s 24-7 Cybersecurity Analyst:
For more information or a demo on how Lumu can help you, be sure to contact us.