According to Lumu’s 2021 CISO Priorities Flashcard, 81% of CISOs realize the need to prioritize extended detection and response, 73% of responders will prioritize threat hunting in 2021, and 70% are waking up to the importance of measuring compromise in 2021. With a CISO’s list of priorities and responsibilities always increasing, we had a conversation with Manuel Santander—CISO of Puntos Colombia, a loyalty program—for his insights into the MITRE ATT&CK® Matrix framework and how it can help security operations.
What is your opinion about the MITRE ATT&CK Matrix?
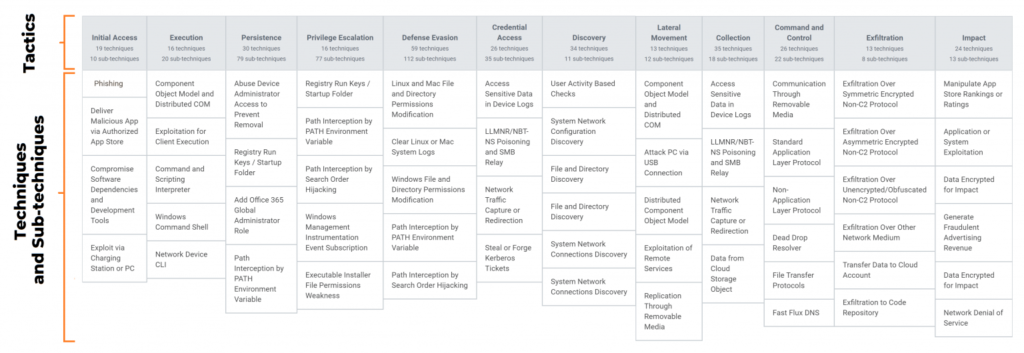
This framework is great because it serves as the foundation of a threat intelligence program. If an organization is just getting started with this initiative and has now used ATT&CK, this is a great starting point. Once you have this intelligence, it can be used to better understand the compromises taking place within the organization, and to go beyond trending treats in the industry. In the end, what truly matters is your own reality.
As a security strategist, you need to prioritize investments. How do the ATT&CK matrix and Lumu help you?
For a CISO to make decisions based on data, having access to a consumable version of the ATT&CK Matrix is a must. Teams can use ATT&CK to inform security strategists about how they are being attacked and map those attacks with their own cyberdefenses. These allow mainly two things:1) to know if your current cybersecurity tools are performing well and 2) to know if (and most importantly what exactly!) you need to strengthen in your defense strategy. Lumu does a really nice job by automating the ATT&CK matrix in a way any organization can leverage to make data-based decisions.
Is the MITRE ATT&CK framework enough to understand the compromises in the organization?
ATT&CK is a great framework but it’s not a silver bullet. You need other sources to give additional power to the ATT&CK matrix to map the progress of the attack with known adversarial TTPs and give additional context. In that way, you can not only manage plain alerts, but deeply understand attacks and respond accordingly.
What advice can you give to CISOs and security managers?
We live in a world of limited resources, which means limited budget to buy defense tools and limited teams qualified to operate them. Unfortunately, there is little we can do to increase the resources available to us. What we can do is make our processes more efficient. This means focusing on what we can do with less human intervention in handling alerts and more automation. You need to have tools that pinpoint confirmed compromises, so you can focus your team on understanding the attacks and responding.
To learn more about the challenges Lumu can solve for you and your team, visit our use cases.
If you are ready to give Lumu a try, you can open a free account here.