An average security team receives 3,000 notifications on a daily basis and this number increased by almost 20% last year. Combing through alerts is costing businesses an average of $1.5 million in overhead expenses on a yearly basis, and most CISOs have admitted to struggling to manage the rising number of notifications.
From its outset, Lumu has offered an easy-to-use solution that drastically eases alert fatigue by going beyond Indicators of Compromise and alerting your teams only when a particular device is being contacted by infrastructure that belongs to the adversary. Now, we are strengthening this capability by including robust context around confirmed compromise incidents that enable teams to implement the right response in a timely manner.
The context will help to answer questions like:
- How is the compromise spreading?
- What is the attacker’s objective?
- Is this happening anywhere else?
- How long has this been going on for?
Today, most security monitoring technologies don’t provide this kind of context out of the box. You need—in the best scenario—to invest a lot of time and effort creating rules, applying conditions, and more. But not with Lumu.
Why this is important for security teams
As a part of a security team you have two big priorities: mitigate the threat as quickly as possible and take strategic decisions to avoid this threat in the future.
Typically, to mitigate threats security teams can take a combination of actions, such as attempting to block adversarial infrastructure, learning more about the type of threat, evaluating the scope of the problem in the organization, and identifying which devices are affected. All these things take time, and Lumu now has a single place to understand the compromise, which is key to security teams when responding to incidents.
After mitigation, the next important thing is to make strategic decisions that should include documentation about the attack and techniques, reveal the history behind the compromise, adjust the incident response playbooks, and identify if long term prevention strategies are required. With the context provided by Lumu making factual decisions is finally achievable in cybersecurity.
How Lumu provides enhanced compromise context
To address this ongoing problem, Lumu is introducing Compromise Context to help you be more efficient and effective in your daily operations.
Compromise Context allows organizations to enrich confirmed compromise information and understand how the attack is moving, what the compromise distribution is, what the compromise behavior is, and more.
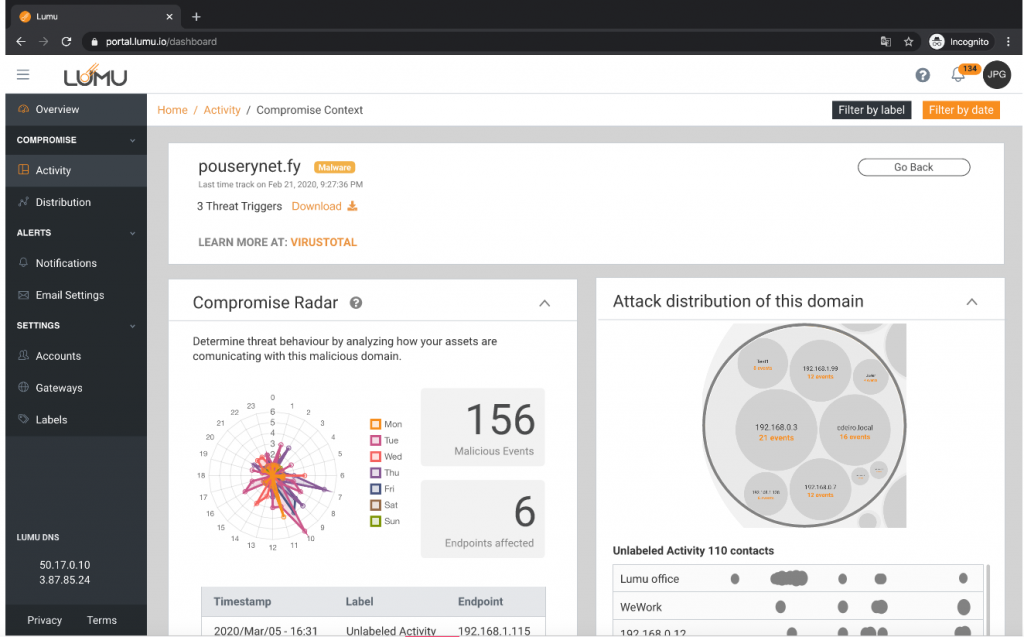
Now including internal and third-party intelligence, your team doesn’t need to start searching for information, you have it all in a single pane.
How to apply this context in your organization today with Lumu
Let’s say that you receive an alert with a compromise inside your organization. How do you decide if something is critical for the organization?
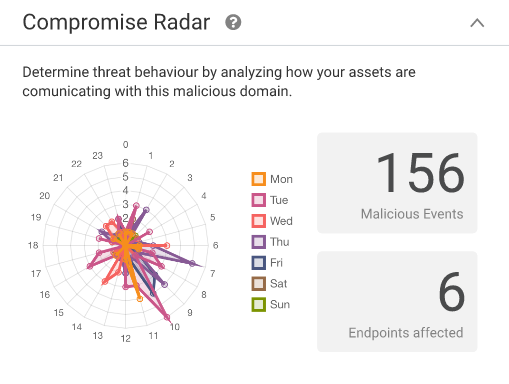
- Check the Compromise Radar™ to see how many malicious events and endpoints are affected. See the radar to identify the behavior. The Compromise Radar™ allows security analysts to quickly separate occasional contact from persistent and automated compromises that have the power to cause harm to the organization.
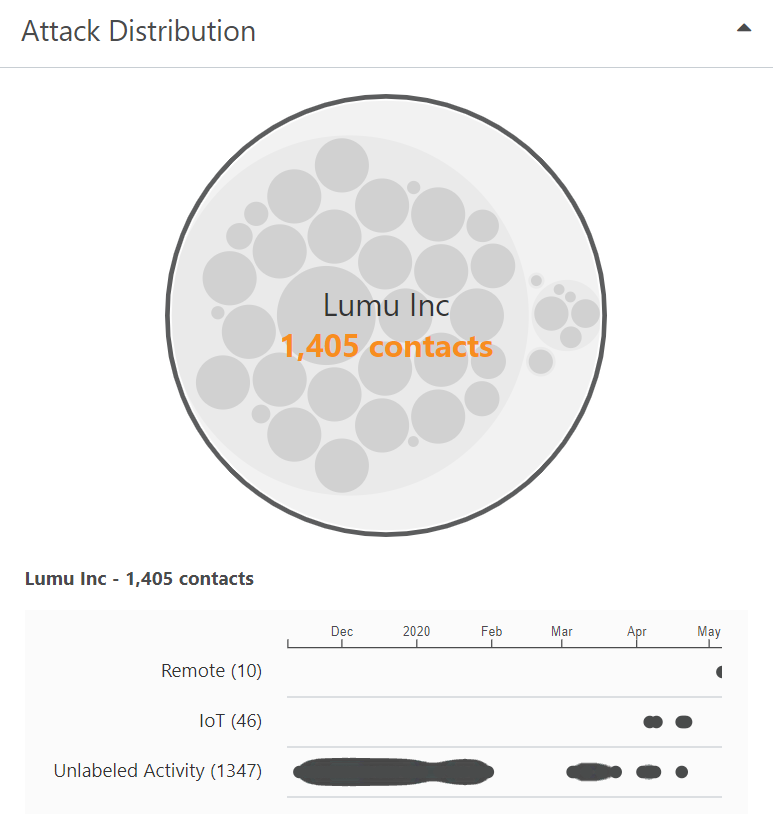
- Check the attack distribution. If you see that your critical environments like SWIFT, PCI-DSS, IOTs, OT networks, or others are affected, take immediate action. Also, see how it is spreading inside your organization; did it start in the finance area and move laterally to your critical environment?
- Gather more information about the compromise with related articles for security researchers around the world covering this threat and incident response playbooks. Our playbooks are based on the NIST Framework and suggest the steps to respond to attacks.
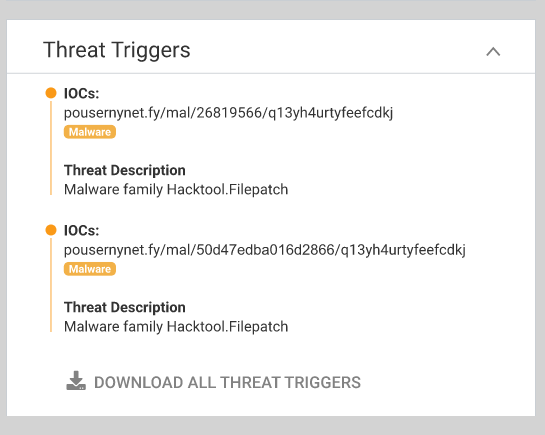
- Learn more about why Lumu classified the event as a compromise in Threat Triggers and download resources to facilitate the configuration of policies that contain these compromises using your current cybersecurity strategy.
- Take some time to understand the compromise in order to make strategic decisions to minimize the risk of these threats in the future.
Knowledge is power and Lumu’s compromise context places that power right at your fingertips. Supercharge your incident response by diving into unprecedented insights, right in the Lumu Portal.