Table of Contents
The latest announced VPN vulnerability is typical of the risks associated with VPNs. While VPNs are essential for secure remote access, they often harbor exploitable weaknesses that can undermine perimeter defenses. Such vulnerabilities allow attackers to infiltrate networks, access sensitive data, and compromise overall security. Organizations must remain vigilant, employing comprehensive security measures to detect and address threats affecting networks swiftly.
Vulnerability Background
On May 27th, Check Point Software Technologies (Check Point) published a blog post detailing security best practices in response to observed attempts to exploit vulnerabilities in VPN solutions from various vendors. Notably, they underscored that certain attempts focused on local accounts utilizing password-only authentication. On May 28th, Check Point updated its post, disclosing a new vulnerability (CVE-2024-24919) that affects Security Gateways with IPsec VPN in Remote Access VPN and stressing the critical importance of implementing mitigation measures promptly.
Initially, the vendor did not provide specifics regarding the CVE-2024-24919 vulnerability, and it was not assigned a risk score on CVE. However, researchers from Watchtowr, upon reviewing available information from the “hotfix” managed to discern the alterations and extract some conclusions. Their findings indicated that this vulnerability is critical, enabling relatively straightforward techniques such as path disclosure, and potentially allowing attackers to access sensitive files like the shadow file. Eventually, the vulnerability was assigned a CVSS risk score of 8.6, indicating a very serious vulnerability.
How the Vulnerability Is Exploited
Several PoC codes exploit this vulnerability with a simple POST request, allowing the attacker to gain access to the VPN system’s “passwd”, “shadow” and other important files using a Full Path Disclosure vulnerability, thereby creating persistence on the victim’s network.
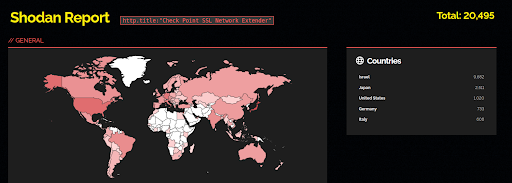
According to Shodan, at least 20,000 indexed devices could be potentially vulnerable to this type of attack.
Immediate Action Items
- Install a mandatory Security Gateway Hotfix to prevent the exploitation of CVE-2024-24919 (https://support.checkpoint.com/results/sk/sk182336).
- Ensure all security solutions are fully deployed and up-to-date across your entire organization and your customers’ networks.
- Proactively hunt for indicators of compromise (IOCs) that attackers might have left behind during the vulnerability window.
- Continuously monitor your network for suspicious activity that might indicate an adversary’s presence within your network or your customers’ networks.
- Configure MFA as a regular policy for all VPN connections.
- As a precaution, change all credentials associated with users present on the device.
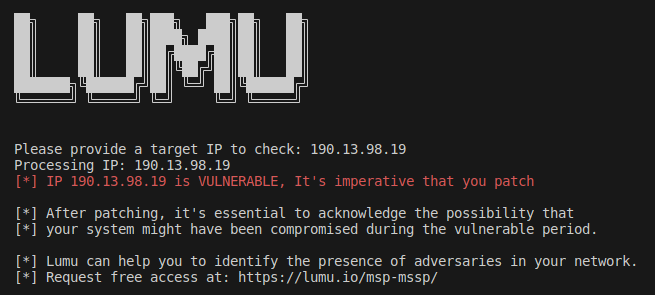
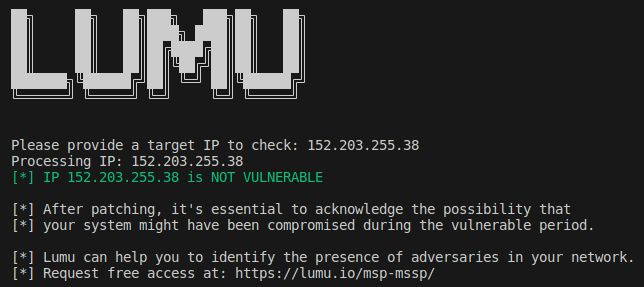
Vulnerability Check Tool
The Lumu Threat Intelligence team has developed a script that can detect vulnerable instances of Checkpoint VPNs. To request access to the tool, simply send a message to [email protected].