With 45% of all emails being spam, a 30% opening rate for messages that contain phishing content, and 12% of those users clicking on the malicious attachment or link, it is clear that continuing to block all that spam is a good idea. But this is not enough. Many organizations continue to act under the assumption that because spam email is quarantined, users are secured. Another common myth is that if an attack reaches a user’s spam folder, the attack has failed. Both of these assumptions are false. There are a few reasons why these are incorrect premises.
First, attackers not only send emails and hope to succeed, but they are also highly motivated and they will persevere until they accomplish the compromise. In addition, sending spam emails is unbelievably cheap, according to Trend Micro bulk email plans in the dark web start at USD$20, thus the ROI of these cybercrime campaigns is significant. More importantly, the attacker gets very close to your users. With a bit of tweaking and perseverance, they will absolutely achieve their goal.
Second, these emails are being segregated and often ignored for good, when the reality is that they hold incredible value and unique intelligence about how an organization is being targeted, including which users in a company are being closely and relentlessly targeted and how this is being attempted.
Lastly, we cannot forget that most of our users are now working from home, thus the security controls designed to protect the perimeter are now void. Remember, email is only one vector for propagating attacks, adversaries have plenty of options in hand.
At Lumu, we are already helping more than 700 organizations unleash the value of their own Spambox. And now, we have new and improved capabilities that allow you to join them.
Unlock the Value of Your Spambox by Analyzing Spam
Implementing a Continuous Compromise Assessment model requires the systematic collection and analysis of a wide range of network metadata. One of the most important, yet frequently ignored data sources is spam. However, your own organization’s spambox is a unique threat intelligence source and it can help you understand the compromises your organization is facing. Different solutions in our space focus on blocking spam, but understanding how attackers are trying to compromise the organization and if they are successful is precious information that most companies ignore.
Here are some of the most relevant items you can access once you start analyzing spam to measure compromise in real time:
- Threat insights: Drill down into detailed, factual data about the attacks targeting your organization, including the kind of attack and the volume with which the attack is occurring. See when the malicious campaigns occur, how successful the attacker is, the most common attack types, and more.
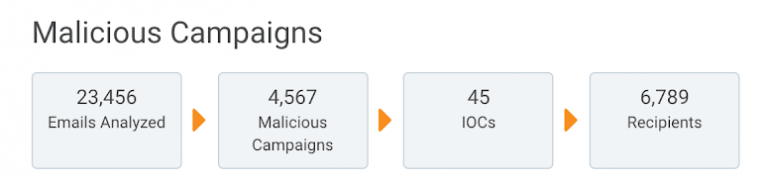
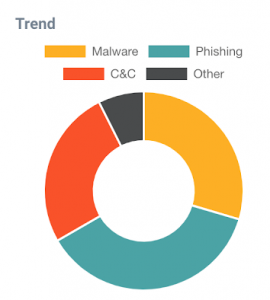
- Spambox attack patterns: Arm your team with a deep understanding of the threats targeting their enterprise and grant them the ability to notice patterns in order to adjust cyberdefense and inform future investments.
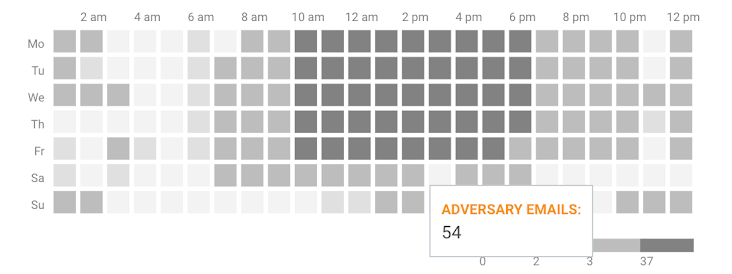
- Understand malicious campaign patterns: Adversaries will relentlessly adjust their email campaigns to improve deliverability. As such, the same campaigns will be launched repeatedly until they become successful.
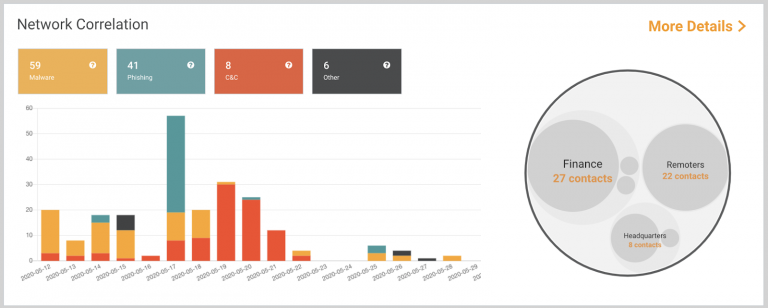
- Discover which assets and environments are being affected: Detect compromised assets and where they are located with advanced network correlation. Visualize compromises according to your unique set of labels (eg. PCI, Swift, Finance, Central Office).
Many organizations start their Continuous Compromise Assessment journey with Spambox, because it is easy to implement and they see its value right away. There are two ways to get started:




