Table of Contents
The Snowflake Supply chain attack is a recent example of attacks that are becoming an increasingly common threat to organizations worldwide. These attacks exploit vulnerabilities in third-party services or software to access a range of target organizations.
Recently, several major companies were compromised using the same modus operandi associated with Snowflake account breaches. On June 10, Mandiant published a threat intelligence report linking the threat actor known as UNC5537 to up to 165 possible data breaches affecting large organizations worldwide. All these companies shared the same initial vector: an employees or contractor’s compromised Snowflake system account.
Snowflake Supply Chain Attack Background
Snowflake is a cloud-based data warehousing company that provides a platform for data storage, processing, and analytics, used by prominent organizations across different sectors, from financial institutions like Santander Bank to cybersecurity services & organizations.
Until now, it has been impossible to find evidence linking the Snowflake incidents to any breach or vulnerability exploitation within their system. All indications point to the massive use of stolen Snowflake credentials obtained via Infostealers. Apparently, the threat actor obtained a cumulative list of stolen credentials since 2020 and has been using it to access the platform in cases where MFA is not enabled, allowing them to exfiltrate data. Mandiant estimates that approximately 165 companies may be affected, but records on the deep web show more than 300 companies with SnowFlake credentials being sold online.
Impact of Infostealer Malware
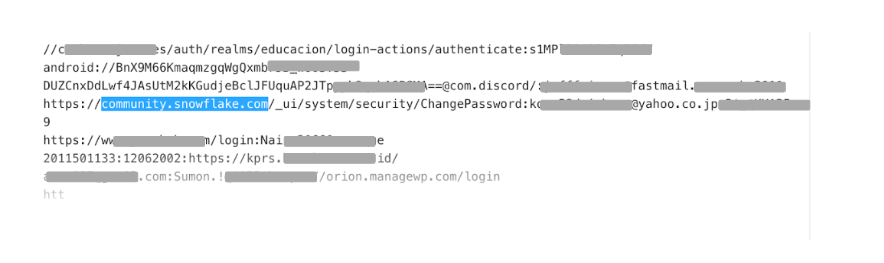
The risk posed by infostealers has been highlighted by Lumu as one of the most dangerous hidden threats. The economy surrounding the infostealer cycle drives the proliferation of threat actors who specialize in targeting different platforms to obtain credentials and exploit access with weak security policies, ultimately obtaining awesome profits. In this case, logs related to Snowflake accounts have been found and provided by the stealers Vidar, Risepro, Redline, Racoon Stealer, Lumma, and Metastealer.
Below is an example of how this information is collected by infostealers and sold on the deep web.
Secondary Breaches
Some of the notable incidents involving compromised Snowflake credentials are listed below in chronological order (approximately according to the first notices), in the DeepWeb these publications are made by two particular actors with aliases Sp1d3r and ShinyHunters:
- 05/14: Banco Santander 30 M users
- 05/15: Ticketmaster 560 M users
- 31/05: Hudson Rock
- 06/01: QuoteWizard / Lending Tree – 190 M users
- 06/05: Advance Auto Parts – 380 M users.
- 06/10: Pure Storage
- 06/07: Cylance Customers & Partners DB – 34 M users
- 06/18: LAUSD.org & Edgenuity. 4 M users
- 06/20: Jollibee Food – 32 M users
Is the CDK Global Ransomware Attack Linked to Snowflake?
The CDK Global Ransomware Attack hamstrung over 15,000 car dealerships across the United States and Canada. CDK Global is still working on restoring its systems and has not confirmed any possible causes. It’s been reported that the attack was carried out by the Black Suit Ransomware Gang.
There’s been speculation surrounding a possible connection between the Snowflake supply chain attack and other recent breaches, such as the CDK Global breach. This speculation is mainly driven by the timing of the attacks and CDK Global’s use of Snowflake services. However, at the time of writing such connections can’t be confirmed. It is possible that Black Suit could have gained initial access through compromised Snowflake credentials. However, there is no clear connection between Black Suit and UNC5537.
To assist with this crisis, Lumu is offering Managed Service Providers with clients affected by the CDK breach free Lumu accounts and instances to assess their clients’ exposure and mitigate effects.
Immediate Action Items
Snowflake has denied any direct compromise of its systems and has provided technical recommendations related to monitoring account activity. Additionally, Mandiant has created a technical guide to identify potential indicators of reconnaissance stages in Snowflake systems.
Beyond these recommendations, it is important to apply robust security policies:
- It is strongly recommended to implement Multi-Factor Authentication (MFA) for all accounts. This significantly reduces the risk of credential theft and unauthorized access.
- Continuously monitor for potentially compromised accounts related to your company as a way to reduce the attack surface.
- It is recommended to implement an Identity and Access Management (IAM) system. IAM systems provide a comprehensive framework for managing user identities and access permissions across the organization this system integrates with alert systems to provide.
- Implement real-time network monitoring to prevent typical initial vectors or infostealers.
- Real-time monitoring and notifications of any suspicious activities or unauthorized access attempt




