Table of Contents
At Lumu, our product team works round-the-clock to evolve the Lumu experience providing you with the best features when it comes to cybersecurity operations.
Here’s a behind-the-scenes look at what we analyzed over the last 12 months:
- Analyzed 1 trillion+ records of network metadata.
- Detected 192 million+ adversarial contacts.
Next, let’s take a look at how the product evolved over the last year
The New Lumu Free
Lumu Free got a major upgrade at the beginning of the year, allowing you to ingest more data through added sources such as firewall and proxy logs.
This release also expanded the available metadata collection mechanisms, giving you access to:
- API-based custom collector
- Virtual appliance data collectors for on premise infrastructure
- DNS gateways
- Out of the Box Data Collection from Cloud and SaaS Environments
This expansion of the Lumu Free tier was designed to provide even greater value to our Free users while minimizing any friction during deployment.
Enhancements to the Incident View
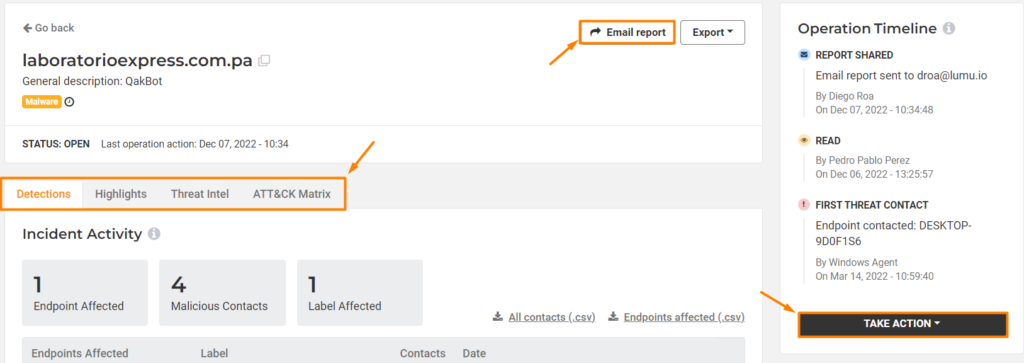
Our incident view was greatly enhanced, offering customers the ability to see malicious activity in an even more efficient and detailed manner.
- The Email Reporting function provides the ability to export all details related to an incident, making it easier to share email reports with others outside of the portal.
- The tabs in the incident view make it easy to browse through and see incident context in an organized manner.
Lastly, the Operation Timeline allows for incident tracking internally with the ability for different members of your organization to close the incident, leave a comment, or mute it.
Enhanced Detection of Lateral Movement
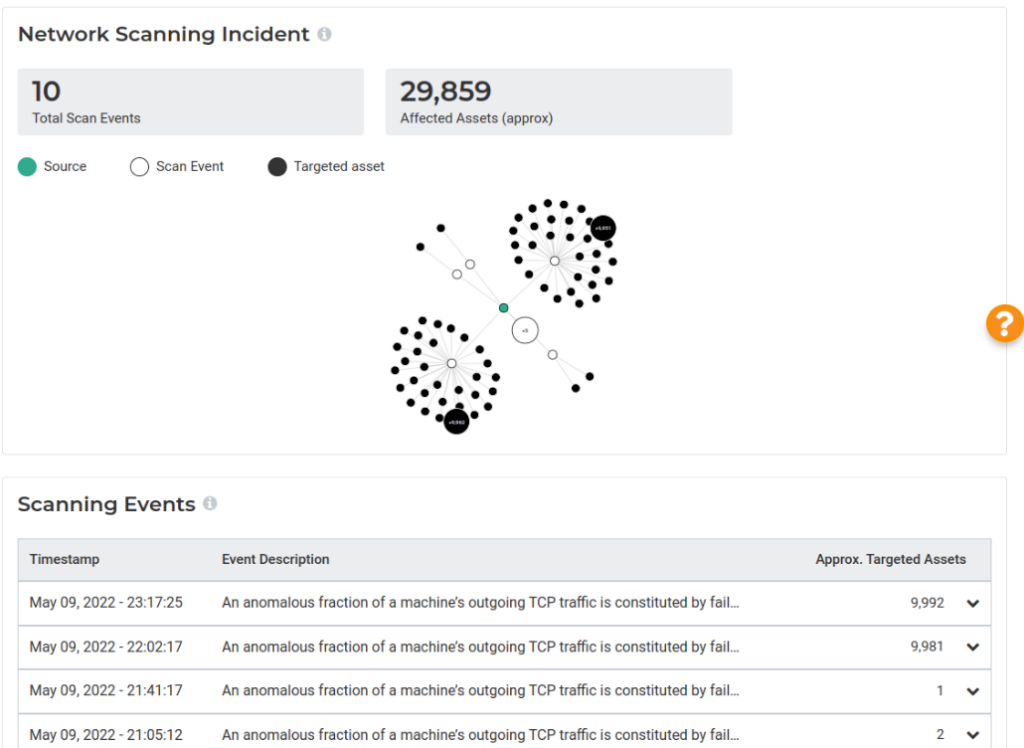
Lumu’s network scanning abilities were enhanced to not only show that a network scanning event was taking place, but also uncover the assets being targeted by adversaries.
This gives you complete visibility into the techniques used by the attackers (the source of the attack, targeted assets, and a detailed timeline) and provides the ability to download the list of affected assets in .csv format so it can be fed to other solutions in your cybersecurity stack.
You can read more about this feature here.
Mac & Windows Server Agents
Adding new agents to meet the technical needs of our customers was another important area of focus as we protect customers wherever they are in the new hybrid reality of the workforce.
We added two new agents for more metadata collection options by adding a Mac Agent and an Agent for Windows Server.
Single Sign-On and Multi-Factor Authentication
Whether you are a large enterprise or a small business, Lumu gives you the options you need to secure access to the portal by adding different authentication options.
You can set up Single Sign-On with any SAML compatible provider including Okta and Ping Identity.
Lumu also added Multi-Factor Authentication for even more enhanced security when accessing your information. You can enable this feature by using the Authenticator apps, such as Google Authenticator and Microsoft Authenticator based on your needs.
To learn more about how to activate this feature click here.
Office 365 Out-of-the-Box Email Integration
This allows you to easily monitor all emails across your Outlook 365 email channel.
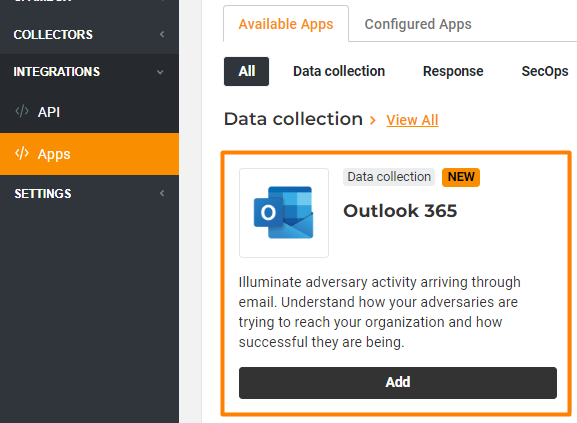
This enhanced email monitoring feature detects malicious activity outside of just the spam box for better visibility into whether there is adversarial communication happening across your email user base.
Simplification of Data Collection and Deployment
Early this year we rolled out 1-click out-of-the-box integrations to collect network metadata from cloud and SaaS providers.
We were also now listed on AWS Marketplace, making it easy to deploy from there.

Getting Your Cybersecurity Stack on the Same Page.
Last, but certainly not least, we had to highlight some of the 40+ integrations that were added to the product over the last 12 months. Product integrations are a big part of our strategy as it enables organizations to operate cybersecurity proficiently while leveraging existing tools and resources.
Here are some of the key product integrations we released:
Incident Response
We added many new integrations to respond to malicious incidents in real time.

Security Operations
We also enhanced the ability to manage incidents using your existing tools by adding new Security Operations integrations for unified incident management.

You can also find us on the marketplaces for Splunk and QRadar.

To learn more about integrations, you can access our integrations page here.
We hope you’ve been enjoying these features and can’t wait to share all of the exciting things we have in store for next year. Stay tuned.