Watch the news these days and you will find a particular word show up recurrently, one that creates anxiety among business leaders and cybersecurity practitioners alike: ransomware. Regardless of your organization’s vertical or its size, everybody who uses a computer for business or leisure should be aware of it. There is an evil out there trying to get into your infrastructure just to encrypt your most important asset: your information.
We don’t mean to bore you with stats but if you thought the problem was not bad enough, take a look at these stats which speak for themselves. If you already know how bad (and we mean pretty bad) it is, you may skip this paragraph. According to Kaspersky there were 174 ransomware attacks against cities and towns in 2019. Cybersecurity Ventures estimates that the global cost of ransomware will reach $20 billion by next year and Malwarebytes reports that Ryuk detections increased by 543% over Q4 2018 and Sodinokibi increased by 820% since its introduction in May 2019. That means that the problem is not going away but is increasing dramatically.
The situation is so out of control that a new job title is emerging: “Ransomware Negotiators”. This new role is helping organizations to scale down financial demands, arrange payments, and try to restore encrypted data. This certainly shows that we are tackling the problem in the wrong way and that we need to change our mindset and strategy.
First: The Basics
By definition, ransomware is a type of malware that encrypts victims’ information and demands a ransom to return the information to its original unencrypted state. Even though this definition differentiates this type of malware from the huge amount of samples out there, there are still several behaviors that belong to particular ransomware malware families. Understanding these behaviors is the first step to successfully mitigate the attack, so let’s dig into the details.
Let’s review three real-life examples and how Lumu has helped organizations prevent ransomware attacks from materializing, and keep you out of the news cycles.
Case Study 1 – WannaCry Ransomware Attacks
In May of 2017, a massive cyberattack was spotted affecting thousands of Windows machines worldwide. The impact of this attack was not only its ransomware nature but also its ability to spread quickly across networks thanks to the ‘eternalblue’ exploit discovered several months before the outbreak.
This looks like a forgotten story but it is far from over. At the time this attack took place, it was only a matter of time for security experts to identify a killswitch to stop the havoc. Thanks to experts’ efforts, WannaCry is out of the front pages, for now. However, it is still worrisome to find that even today this threat remains at the top of detections by AV vendors. So are we really safe?
Well, let’s see. Taking into account its MITRE ATT&CK matrix, the “Exploitation of Remote Services” (T1210) is a behavior used by several different attacks including Emotet, NotPetya, and PoshC2, among others. So even if your files are no longer encrypted by WannaCry, if your infrastructure has been infected by this worm it is a clear sign of how vulnerable you are against even more nefarious trojans that can also lead to ransomware attacks, such as the triad Emotet, Trickbot, and Ryuk.
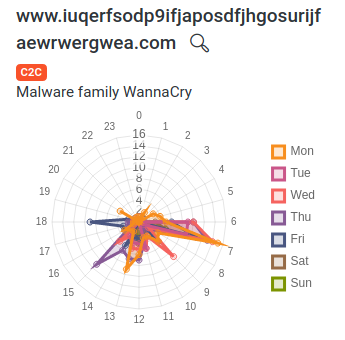
So, if you log into your Lumu account and see that WannaCry is active on your network infrastructure, you MUST patch your systems. Otherwise, you are completely exposed to really dangerous attacks.
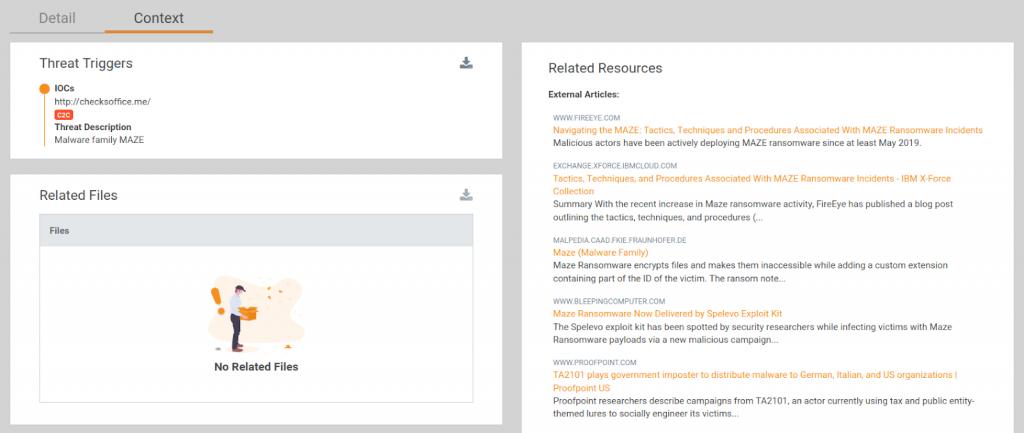
Case Study 2 – MAZE Ransomware Attacks
When we are talking about MAZE ransomware, we are not talking only about a malware family, we are talking about a complete business operation that integrates multiple parties with different levels of specialization to increase efficiency and its RoI. This creates a highly complex environment, which is even more challenging to follow without the right context.
Based on FireEye’s report, MAZE ransomware attacks are the result of any of the following initial compromises:
- A user downloaded a malicious resume-themed Microsoft Word document that contained macros which launched an IcedID payload, which was ultimately used to execute an instance of BEACON.
- An actor logged into an internet-facing system via RDP. The account used to grant initial access was a generic support account. It is unclear how the actor obtained the account’s password.
- An actor exploited a misconfiguration on an Internet-facing system. This access enabled the actor to deploy tools to pivot into the internal network.
- An actor logged into a Citrix web portal account with a weak password. This authenticated access enabled the actor to launch a Meterpreter payload on an internal system.
After access has been granted, the attackers start to silently move across the network, gaining a foothold in as many machines as possible. Keep in mind that even if their ultimate goal is to unleash ransomware attacks on those machines, having access to the victims’ entire infrastructure also provides them the advantage of exfiltrating huge amounts of sensitive data that will be used as another extortion alternative.
Summarizing all of this, if you log into your Lumu account and see that there is MAZE activity on your network infrastructure, you MUST identify the affected endpoints, clean and quarantine them with your endpoint protection technology program. Note that you might find more than one malware distribution in those machines. Once this is done, be sure to verify your internet-facing systems, and don’t forget to include RDP and Citrix technologies. At this point, the enemy is already inside your network you don’t have time to waste.
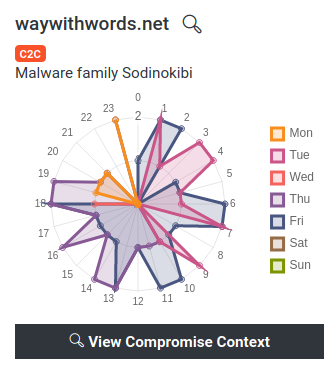
Case Study 3 – Sodinokibi aka REvil Ransomware Attacks
When we refer to Sodinokibi, we are talking about one of the most evasive ransomware attacks, which has caused huge damage to organizations since its public release in April of 2019.
Based on previous reports, we now know that this ransomware has been spread via exploits targeting vulnerabilities in servers and other critical assets, phishing, and exploit kits.
Now if we focus directly on its network traffic, it can be classified as “post-mortem.” This means that the interaction between the victim and the malicious servers occurs after the files have been encrypted and it is used to share system information and encryption keys. The type of request generated by this attack uses the following structure, where path_1 and path_2 are random entries chosen from each of the columns in the list below.
POST hxxps://[MALICIOUS_DOMAIN]///.<jpg|png|gif>
Cache-Control: no-cache
Connection: close
Pragma: no-cache
Content-Type: application/octet-stream
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.3112.90 Safari/537.36
Content-Length: 1000
Path 1 | Path 2 |
wp-content | images |
static | pictures |
content | image |
include | temp |
uploads | tmp |
news | graphic |
data | assets |
admin | pics |
game |
So if you log into your Lumu account and you find some Sodinokibi activity, you MUST identify the affected endpoints and verify the requests associated with the malicious domains. If they share the structure previously shown, your endpoint was infected so you need to quarantine it and start your endpoint protection technology program.
Conclusion
Sun Tzu once said, “If you know the enemy and know yourself, you need not fear the result of a hundred battles”. This wisdom is still applicable to the cybersecurity reality we are living in. Now that you understand the enemy and its ransomware attacks, Lumu can grant the visibility into your own network infrastructure that lets you “know yourself.” With these two pieces of knowledge locked down, you won’t need to fear being mentioned in the next news report on the latest ransomware attack.
If you haven’t already, sign up for a Lumu Free account and start measuring your real-time level of compromise today. For more on the topic of ransomware, be sure to visit our Resource Center.