Table of Contents
Security logs provide a detailed record of activities within an organization’s IT environment, including user access, network activity, security events, and more. By retaining logs, organizations can demonstrate that they maintain a comprehensive audit trail, which is essential for compliance audits and forensic investigations.
Log storage plays a crucial role in ensuring compliance with various regulatory requirements across industries. Regulations and security frameworks such as PCI, HIPAA, SOC2, NIST and CIS have specific mandates regarding the collection, retention, and protection of log data. Most Cyber Insurers also require that organizations have a way to save and access essential logs. Failure to comply with regulatory requirements can have serious consequences, including possible legal repercussions. Because of this, storing logs has become fundamental for many organizations.
Traditionally, organizations face the challenge of trying to send everything that their security compliance demands to their SIEMs. Security logs are highly diverse, with network data making up a significant portion of them. Attempting to push all that into the SIEM leads to inefficiencies in cost and performance that will quickly put the SecOps team in pursuit of efficiencies to reduce cost and optimize performance; in doing so, they will inevitably create gaps in visibility by sacrificing the network data.
SIEMs – Slow Performance and High Cost
A SIEM’s performance, cost of acquisition, and operation are challenged when they’re forced to store large volumes of data provided by the network over long periods, making them a costly and impractical solution for log retention. This not only hinders an organization’s ability to meet compliance requirements but also leads to unnecessary expenses due to the high costs associated with storing large amounts of data. Additionally, SIEMs may not provide sufficient data retention periods to meet all compliance mandates, further highlighting their limitations as a long-term storage solution. Organizations relying on SIEMs for log storage risk facing high costs and compliance challenges without realizing the full benefits of their investment.
Lumu customers gain network visibility that no SIEM can provide while optimizing their SIEM focus on what it truly excels at.
An Optimized Approach to Security Log Retention:
Lumu understands the need to store and access essential logs and we’ve evolved our Playback feature to allow organizations to store their essential network logs with the ability to run data queries and exports for stored data from the last two years.
Lumu’s security log storage capabilities are specifically designed to handle the most demanding network data efficiently. Unlike traditional SIEMs, which struggle with large volumes of network traffic logs and require costly storage and resources, we are focused on storing and processing the most relevant network metadata.
This optimization allows for quick retrieval of the most critical data points, such as:
- Traffic to Specific Endpoints: Identifying and analyzing network activity related to specific devices or servers over a defined period.
- Communications with Known Malicious Destinations: Tracking which users or devices in the network have communicated with potentially harmful IPs or domains.
- DNS Queries: Storing logs of DNS queries to identify patterns and detect any abnormal or unauthorized domain lookups.
- Anomaly Detection and Pattern Recognition: Automatically identify unusual patterns or behaviors in network traffic that may indicate a security threat.
- Network Traffic Logs: Storing logs related to general network activity, such as firewall traffic, to analyze communications between internal and external entities.
- Endpoint-Specific Traffic Analysis: Providing detailed insights into all connections and communications associated with a specific endpoint during a given timeframe.
The data points above provide organizations with easy access to their most critical data and information for compliance, forensic analysis, and security monitoring, all while reducing costs and maintaining network performance.
A More Effective Threat Detection and Log Archive Architecture
Companies and MSSPs using Lumu have found this architecture to be more effective for meeting compliance requirements and improving threat visibility, detection, and response. By eliminating the need to ingest network traffic into a SIEM, they regain network visibility without increasing costs. Additionally, they benefit from extended retention of network data along with the robust threat detection and response capabilities provided by Lumu.
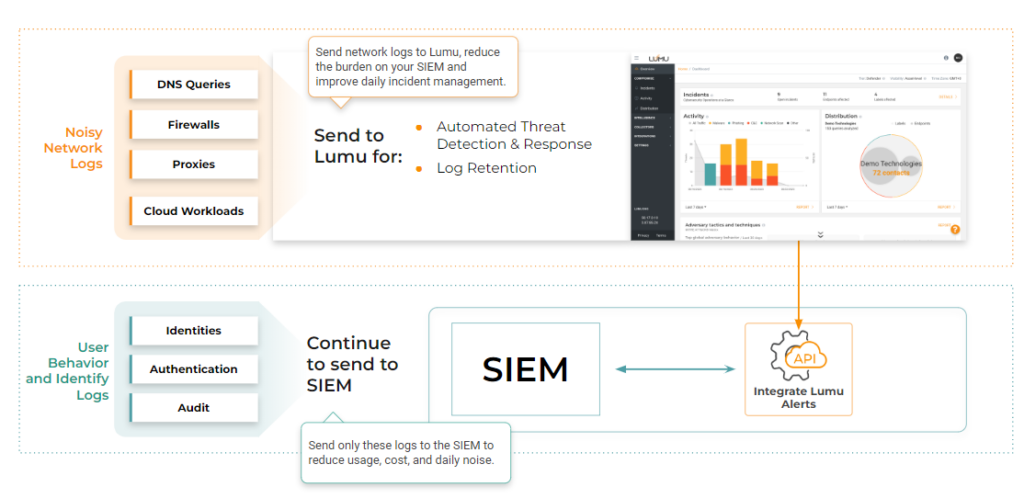
Now, instead of sending noisy network logs to the SIEM, organizations can send these logs to Lumu, including:
- DNS Queries
- Firewalls
- Proxies
- Cloud Environments
By following this model, organizations can continue sending their lower-volume logs to the SIEM like Identities, Authentication, and Audit Logs as shown in the diagram above. Offloading high-volume network logs to Lumu results in a significant reduction of data ingestion (EPS) and removes the storage burden on the SIEMs.
This workflow enables a more manageable day to day SecOps experience with less noise, less alerts, and more effective incident management. Since Lumu can store network logs, analyze them, and take action on any malicious findings, organizations can spend less time managing and maintaining their SIEM, freeing up resources to focus on more critical tasks.
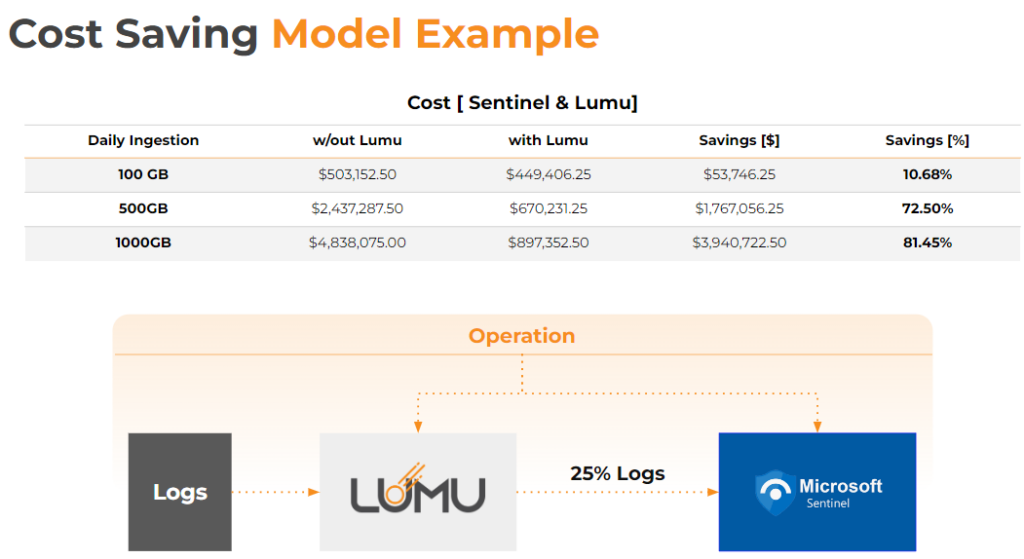
A Cost-Saving Analysis with Lumu
Sending your network logs to Lumu results in significant savings. This cost saving model is an example of how companies can experience significant savings in log storage requirements by sending and storing their network logs with Lumu.
This is one specific use case by an anonymous customer who uses Microsoft Sentinel and decided to send network logs to Lumu to optimize their SecOps capabilities.
Querying Security Logs with Lumu
A key complaint from organizations that have SIEMs is the complexity and delays involved in obtaining historical data when required. Lumu’s security log storage provides up to 2 years of log retention for the network metadata you can query in near real-time.
- 2 Years of threats Incidents via Lumu’s customer portal
- 2 Years of threat incidents exported directly on Lumu’s customer portal
In addition, for compliance purposes, the following information is available on-demand via a support ticket.
For Forensic Investigations
When conducting forensic investigations, Lumu allows you to query historical traffic data from the last two years to understand the behavior of a suspicious endpoint. This enables you to identify all the contacts initiated by specific endpoints over a selected period of time, helping you trace its actions and connections.
To query this data, you can ask: “What was the traffic for this endpoint during this specific period of time in the last two years of using Lumu?”
This is essential when uncovering the scope of a potential compromise or analyzing the endpoint’s involvement in malicious activities.
Threat Hunting Exercises
Identifying all endpoints that have communicated with a suspicious destination is critical during Threat Hunting exercises, allowing security teams to detect hidden threats and uncover potential compromises.
To query this data, you can ask: “Who in my network contacted this destination during this timeframe in the last two years of using Lumu?”
This prompt is particularly useful at the start of a threat-hunting process, where identifying all points of contact with a suspicious destination is crucial to determining the scope of a potential threat. This can also support forensic investigations by identifying other endpoints that may have been involved in a specific incident.
Getting Started
With a successful track of redefining cybersecurity operations anchored in automated threat detection and response, Lumu is embracing the journey of disrupting the way organizations approach log retention. This strategic shift will enable organizations to embrace a more efficient, and cost-effective security strategy. Leveraging Lumu’s log storage capabilities provides extensive visibility into network activities, ensuring compliance and reducing operational burdens.
To learn more about how to use this feature, reach out to your Customer Relationship Manager or reach out to [email protected]. Our team is here to help you get started.