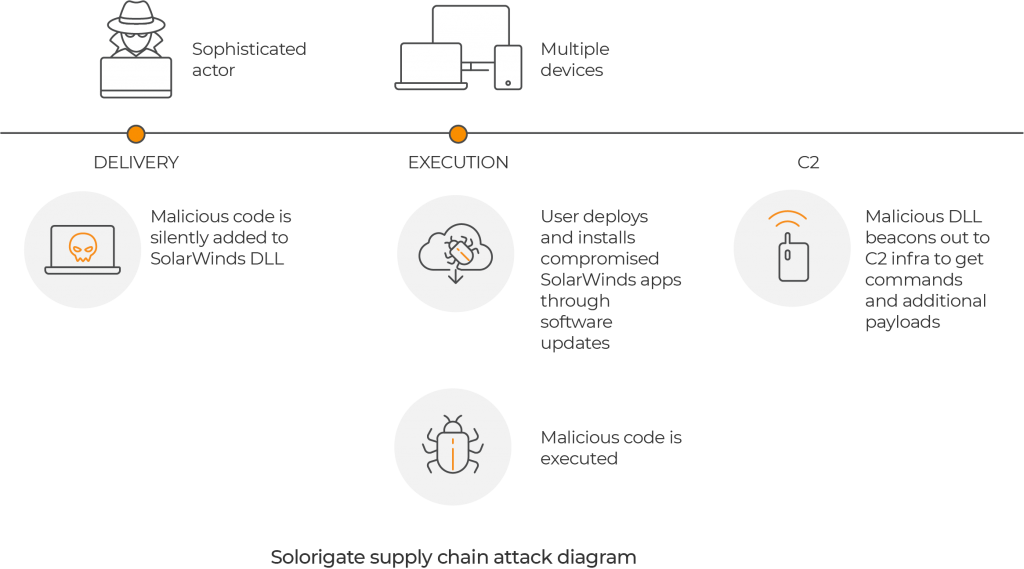
On December 13th, information was released about an attack on the U.S. Treasury and Department of Commerce. The SolarWinds hack is a large-scale breach that likely included a wide range of other federal government agencies and private enterprises. The cybercriminals were able to compromise the systems through a malicious software update introduced on Orion, a platform of SolarWinds. The malicious code was able to open a backdoor in affected systems from as far back as March. A SolarWinds spokesman said, “we believe that this vulnerability is the result of a highly sophisticated, targeted, and manual supply chain attack by a nation state.”
What you should know
- SolarWinds is a software vendor that provides infrastructure, service management products, and network and application.
- SolarWinds discovered a manual supply chain attack on SolarWinds Orion Platform for versions 2019.4 HF 5 through 2020.2.1, released between March 2020 and June 2020.
- SolarWinds has more than 300,000 customers including 425 of the US Fortune 500 companies.
- An emergency directive issued by the U.S. government calls on all federal civilian agencies to disconnect or power down SolarWinds Orion
- “The compromise of SolarWinds’ Orion Network Management Products poses unacceptable risks to the security of federal networks,” said CISA Acting Director Brandon Wales.
What you can do
- If you use SolarWinds Orion in your organization, you should follow the recommendations of this advisory.
- If your organization is affected, don’t just mitigate. You must eradicate compromise as soon as possible.
- You should be very careful hunting for and removing any permanent mechanism the attackers may have implanted.
- Some caution has to be used in the eradication process as the attacker could have implanted time bombs to encrypt or destroy the victim’s data to maximize damage.
- If you are a U.S government agency you should follow these guidelines.
- Nation-state cyberattacks are on the rise. We suggest reading and following these recommendations.
Lumu’s Take
- This incident reiterates the importance of intentionally and continuously searching for the adversary.
- It is not a surprise at this point after all the breaches that we witnessed in 2020, but when we say that attacks evolve infinitely, we mean it.
- At this moment it is difficult to know the real damage that this attack will have in organizations around the globe, the key message here is always assuming you’re compromised and prove otherwise.
- With high-impact attacks like this one, one of our predictions for the coming year begins to materialize, “Cyberattacks to impact everyday people”.
How Lumu helps
Lumu’s Illumination Process combines IOCs with ML and AI to identify when your organization’s network is “talking” to adversarial infrastructure, including those that were part of the Solarwinds hack. It is worthwhile to note that this attack could deliver additional payloads and commands. If this happens, Lumu can detect any such compromises by alerting any adversarial contacts in real time. If you already have a Lumu account you can check your latest compromises here. If you don’t have a Lumu account you can open one today here.




