Table of Contents
As small and medium-sized organizations continue to turn to MSPs to support them with cybersecurity efforts, the MSP is now facing an incredible growth opportunity.
Over the month of October, the analyst firm Enterprise Management Associates surveyed nearly 100 MSPs in North America about their view of building a cybersecurity practice and their most pressing attack-related concerns. Upon the conclusion of this research, the firm offered some actionable recommendations on how to build a security stack effectively.
Key Findings
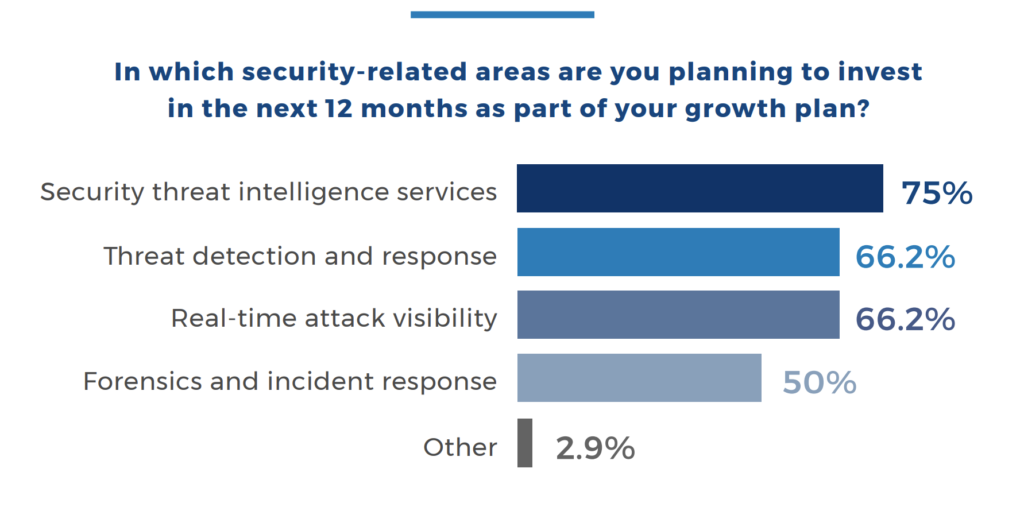
- In the next 12 months, 75% of MSPs are planning to invest in security and threat intelligence while threat detection and response as well as real-time attack visibility are also cited as priorities.
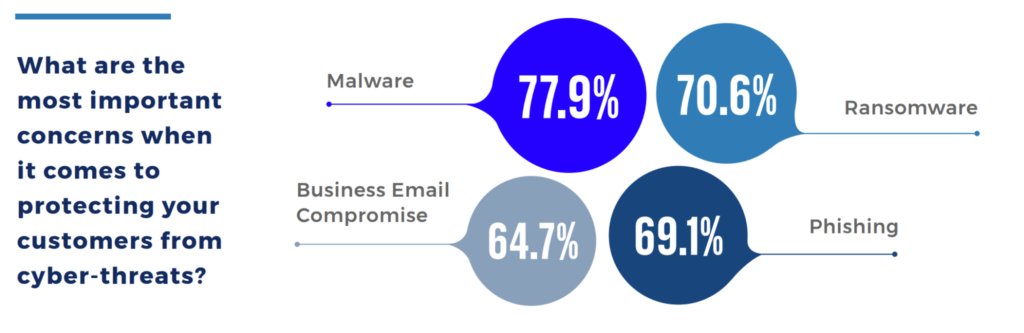
- Malware was cited as the most important concern for MSPs when it comes to protecting customers from cyber threats followed by ransomware.
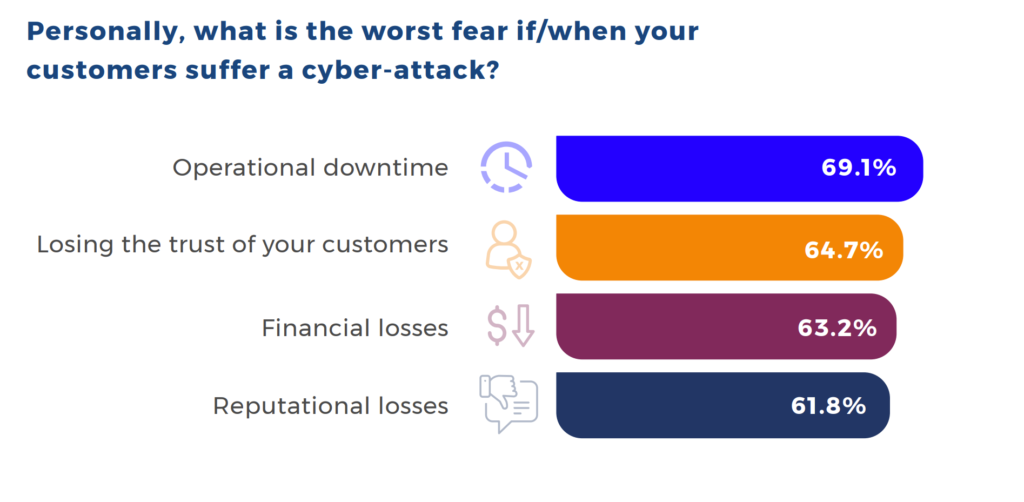
- MSPs’ top fears related to when/if customers experience a cyberattack are operational downtime (69.1%), losing the trust of your customers (64.7%), financial losses (63.2%), and reputational losses (61.8%).
Next Steps
EMA offers five key steps for MSPs who want to grow their cybersecurity practice and here are some highlights:
- Customers’ network-level threat visibility is vital: MSPs should develop methods to identify any and all traces of compromise in the network because it will help MSPs minimize damage and avoid disruption.
- Ensure scalability through effective tools: MSPs should favor SaaS-based commercially available solutions that can grow effectively with the MSP—tools built to effectively use cybersecurity talent, so they spend their time effectively.
- Leverage response automation: MSPs achieve great levels of efficiency by combining real-time attack monitoring with integration capabilities that use out-of-the-box or API techniques for data exchange and touchless response.
- Understand the pricing thoroughly: MSPs need flexible pricing that matches the services delivered to their customers to not get locked into unfavorable long-term contracts which are undesirable considering the changing threat landscape.
- Protect the human element: With phishing and other social engineering techniques increasing in sophistication and effectiveness, MSPs should train their staff and users across their customer base to identify and report these threats.
Representative Vendors
Based on the primary investment areas cited by the MSPs, EMA offers an Essentials Guide for building a cybersecurity stack that will enable MSP growth highlighting that network-level visibility will help them:
- Operationalize threat intelligence
- Automate detection and response capabilities
- Obtain real-time attack visibility
- Assist with forensics and incident response
Lastly, EMA lists 4 critical solution categories and lists representative vendors: Network level visibility, endpoint security, firewall, and email security tools. EMA lists Lumu as their vendor of choice when it comes to network-level visibility, which “serves as the blueprint of all cybersecurity offerings”
Get the The MSP Cybersecurity Market Opportunity Blueprint Report
Be sure to review the full report for the full survey results, more detailed recommendations, and the full list of representative vendors.