Introducing Lumu to potential customers is always a rewarding experience. Customer Engagement Specialist Crystle-Day Villanueva frequently gets to show Lumu to prospective clients. We asked her what they find to be the top 5 pleasantly surprising features.
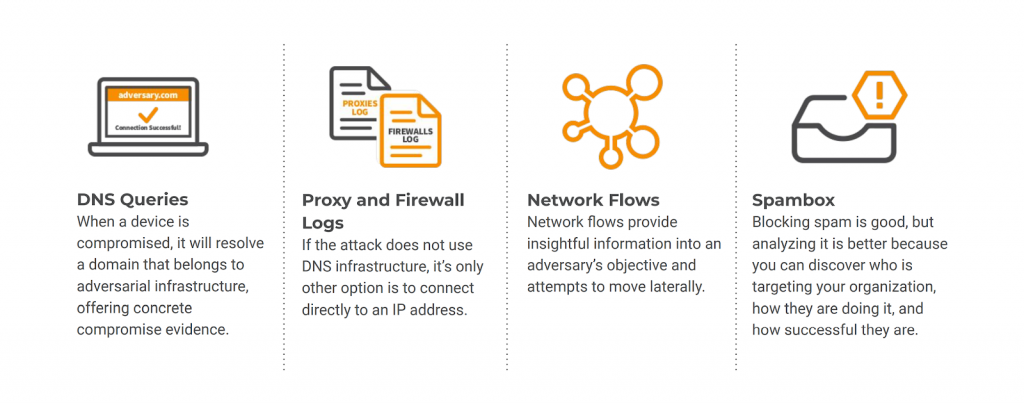
Leveraging Network Metadata
Customers love that Lumu makes use of metadata. It’s something every organization produces, but doesn’t make use proper use of. Unlocking the value of metadata from a wide range of sources—including DNS, Network Flows, Proxy logs, Firewall Logs and spam—means Lumu can assess compromise continuously without being resource-intensive. The elegance of the solution is clear to see.
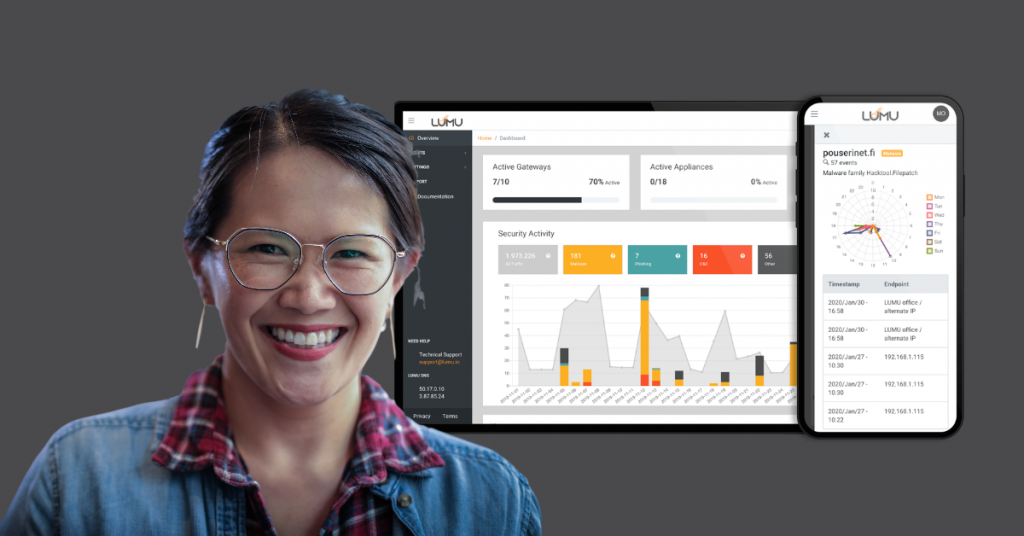
Straightforward Portal
Lumu was designed with the end-user in mind. In a world where the skills and time of cybersecurity analysts are in huge demand, our portal demands less of either. With its intuitive navigation, no special training is required. Even the newest inductees to the world of cybersecurity can see how the Lumu portal immediately shows value.

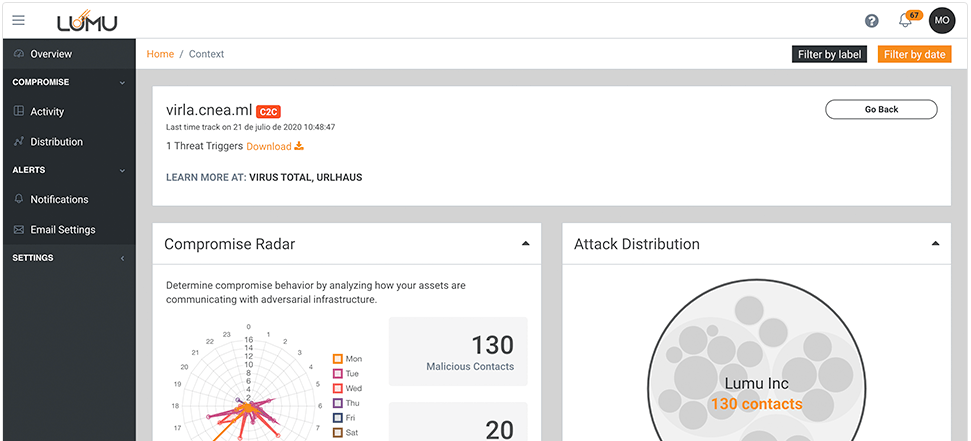
Providing Context on Compromises
When most solutions identify a compromise, the question ‘What’s next?’ is left hanging in the air. With Lumu, customers can see the information needed for answering that question at speed. Each compromise is contextualized with visualizations that reveal its behavior patterns as well as internal and external resources that highlight the severity of the threat
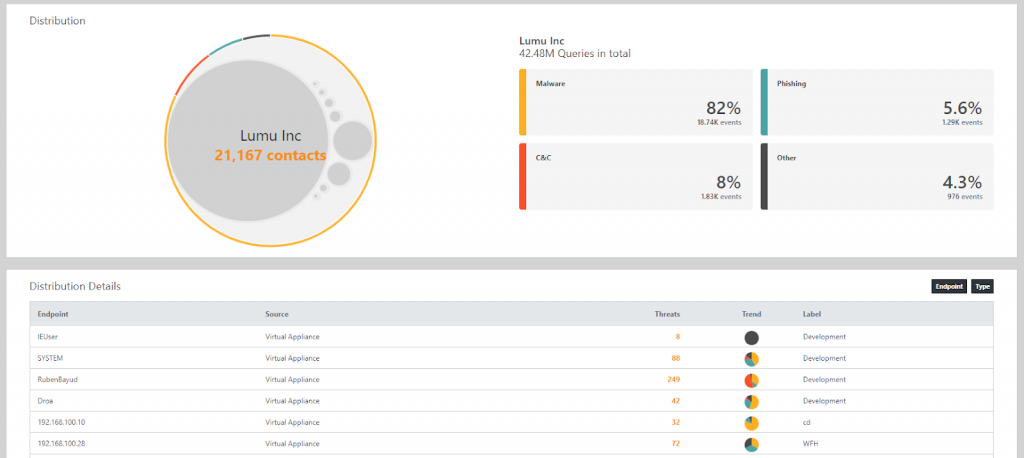
Organized Gateways
With lumu you can group your network traffic gateways into different labels. Each label can represent a department, geographic region or office, as makes the most sense for your unique network infrastructure. Being able to take special care of critical assets or assign certain users to different areas is clearly transformative.
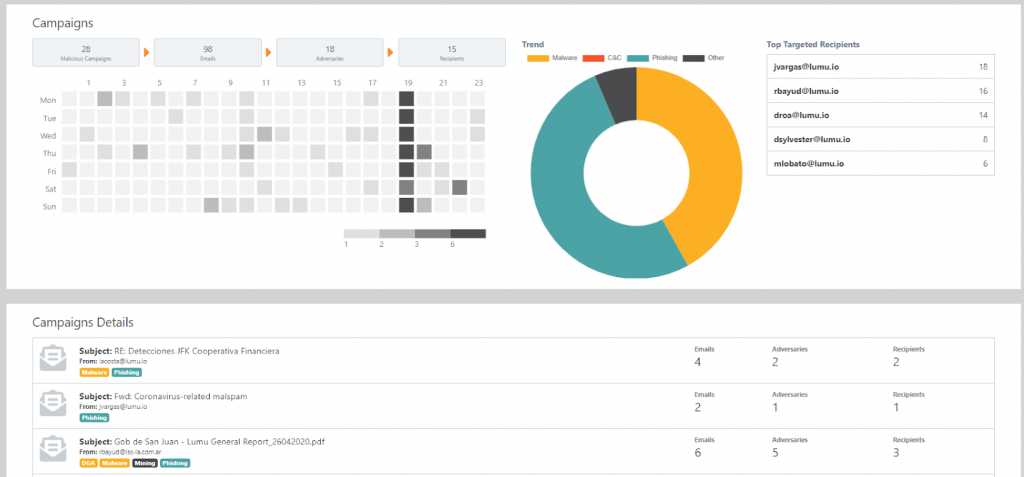
Spambox Is a Game Changer
One customer said: “I can’t believe I was only blocking spam, when it offers so much intel.” Blocking Spam is good, but analyzing it is better. Lumu correlates spam metadata with other threat sources to clearly show users how their organization is being targeted, who the attackers are, and how successful they are.
Experience the Lumu Portal for yourself when you open a Lumu Free account.