Table of Contents
The recent onslaught of the Clop Ransomware group’s cyberattack blitz has shaken the cybersecurity landscape, bringing to mind the now-disbanded REvil group’s campaigns of 2021. Clop Ransomware’s menacing resurgence poses a significant threat to organizations worldwide. Crucially, Clop Ransomware exploits a zero-day vulnerability in GoAnywhere’s file-sharing services, enabling them to infiltrate susceptible servers and unpatched GoAnywhere MFT (managed file transfer) instances.
The History of Clop Ransomware
Clop is a Ransomware as a Service (RaaS) organization that emerged around February 2019. It is part of the CryptoMix family of ransomware. Initially, Clop emerged as a relatively simple ransomware strain, focusing on encrypting individual files and appending the “.Clop” extension to them.
Over time, Clop operators began shifting their focus from individual users to businesses and entire networks. In 2020, data exfiltration capabilities were added. At that point, Clop became more infamous and started targeting large organizations, across the United States, Canada, Latin America, Asia Pacific, and Europe.
In June 2021, Ukrainian authorities arrested 6 people tied to Clop Ransomware. Despite these takedown attempts, Clop Ransomware survived to allegedly breach 130 organizations in February 2023 through a GoAnywhere zero-day exploit. This means it’s likely that the individuals who were arrested were not key figures in the malware’s operation.
How Clop Exploits the GoAnywhere Vulnerability
Clop exploits CVE-2023-0669, a vulnerability with a CVSS score of 7.2, which is related to a pre-authentication command injection in GoAnywhere MFT, affecting version 7.1.1 for Windows and 7.0.3 for Linux and its earlier versions. The issue arises when GoAnywhere MFT deserializes data without proper validation, enabling attackers to execute unauthorized commands remotely. As a result, confidentiality and integrity are impacted.
The attack targets the ‘LicenseResponseServlet’ Java Servlet, specifically the ‘com.linoma.license.gen2.BundleWorker.unbundle(String, KeyConfig)’ method within the servlet. When a packet is received from a user request, it is passed to the ‘LicenseAPI.getResponse()’ method. However, the ‘package’ parameter passed to this method is not properly validated, allowing an attacker to exploit the vulnerability using a specially crafted package.
Based on information shared by the Office of Information Security, Clop’s ransomware code was written to target Windows systems, and some reporting samples showcase that it is a Win32 executable written in C++. The executable packet is compressed, which helps hide its functionality. The ransomware encrypts files with an RSA 1024-bit public key with RC4 that uses 117 bytes of the public key.
According to a Sentilabs report, a new variant of Clop Ransomware, called ELF Cl0p, has been detected. This Linux version has minor differences from the Windows version, mostly related to API calls, and seems to be in its early development stages since some functionalities present in the Windows version are currently missing. A decryptor has been created for this variant by researchers of SentinelLabs
Operating Systems Targeted by Clop Ransomware | |||
Windows | MacOS | Linux | Android |
Yes | No | Recently, Yes | No |
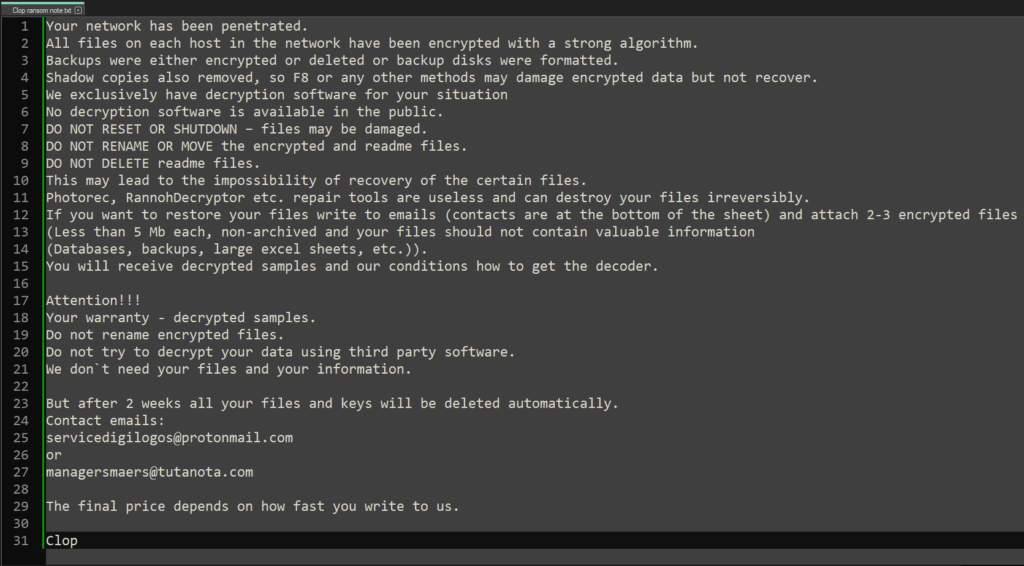
It has been observed that Clop uses remote desktop protocols and that it deploys Cobalt Strike to aid in lateral movement, right after a successfully compromised network. Once the encryption is complete, the victim is able to access a README.TXT and the encrypted file’s extension will be changed to “Clop”. The ransomware notes often state that the Shadow Volume Copies have been deleted.
Why Does Clop Ransomware Matter to You?
Clop has been one of the most active RaaS organizations during the last few years, targeting almost any kind of organization. They have been connected to attacks affecting public and private organizations from different sectors (manufacturing, healthcare, education, energy, and others). Just to give a sense of the scale of the impact, our threat intelligence team found that as of the end of March, Shodan shows 1264 instances of GoAnywhere exposed to the internet—while not all of them are vulnerable, they are visible to attackers. In addition to this, there are some factors that make this threat something to care about.
- EDR evasion: The ransomware also attempts to disable Windows® Defender and uninstall Microsoft® Security Essentials.
- Anti-detection techniques: The malware includes anti-analysis and anti-virtual-machine (VM) techniques to ensure the file will not execute if it finds it is running in an emulated environment.
- Legitimate appearance: The binary is signed, giving the malicious file the appearance of legitimacy. But if you look closer, you’ll find that the signing certificate has been revoked, so it is no longer valid
- Process killing and encryption capabilities: Clop ransomware attempts to stop over 600 Windows® processes. By freeing up these processes, files running on them are no longer locked and can be encrypted by Clop. Security researcher Vitali Kremez provides a full list of the processes killed by Clop in his GitHub repository.
- Disruption capabilities: Clop disables Windows repair features so the system cannot be easily restored
- Double extortion risk: Sensitive data is first exfiltrated from the target before their files are encrypted. The attackers created a .onion website on the dark web called “Cl0p^_- Leaks” to serve as a platform to publicly leak confidential data belonging to victims who refused to pay their ransom.
- Spreading capabilities: Clop has claimed that the techniques performed on this kind of attack allow them to move laterally across the organization’s networks, enabling them to deploy ransomware payloads and increase the number of endpoints that could be controlled and encrypted by this group.
List of Victims as of the End of March 2023
Victim | Country |
Bissell | USA |
Emerald | USA |
Caja Popular San Rafael | Mexico |
Tasmanian Government Services | Australia |
Enerjisa Üretim | Turkey |
Intellicare | Philippines |
Crescent Hotels & Resorts | USA |
Columbia Machine, Inc | USA |
Investorcom | Canada |
Imagine360 | USA |
The Cyprinus | Spain |
Spi Group | South Africa |
Detech Information Technologies | Turkey |
Grupo Floraplant | Mexico |
Alto | USA |
Government Of Goa | India |
Inter Terminals | UK |
Global Farm | Argentina |
Atos | France |
Derk Ingenieria Y Geologia Limitada | Chile |
Red Box | UK |
Progression | India |
The University Of Melbourne | Australia |
Crown Resorts | Australia |
Bridgeway Communication System | Philippines |
The Link Group | USA |
Phoenix Technology | USA |
Sodales Solutions | USA |
Nationsbenefits | USA |
Scholastic | USA |
Vumacam | South Africa |
Cloudmed | USA |
Dp World | United Arab Emirates |
Solpac | Japan |
Virgin | UK |
Legacy Technologies | Germany |
Oshco | Saudi Arabia |
Gray Television | USA |
Orca | Canada |
Colombia Lab | Colombia |
Paybox App | Israel |
Verra Mobility | USA |
Bunzl | UK |
First Central Group | UK |
Alivia Health | Puerto Rico |
Hormel Foods | USA |
Crosby | USA |
Munich Re | Germany |
Gas Natural Sa Esp | Colombia |
Volaris | Mexico |
Accuzip | USA |
Sepire | USA |
World Vision International | USA |
Zo Skin Health | USA |
Tropical Texas Behavioral Health | USA |
Humangood | USA |
Kannact | USA |
Cineplex | Canada |
Amerijet International, Inc | USA |
Gdi Integrated Facility Services | Canada |
Hampton Roads Transit | USA |
Pluralsight | USA |
Pension Protection Fund | USA |
Lasotel | France |
Procter & Gamble | USA |
Crossville | USA |
Leslie & S | USA |
Saks Fifth Avenue | USA |
Jay Mart Public | Thailand |
Service Stream | Australia |
Cost Plus World Market | USA |
Wildfire Defense Systems | USA |
Sweeping Corporation Of America | USA |
Tuebora | USA |
Ratelinx | USA |
Ferguson | USA |
Accreditation Commission For Education In Nursing | USA |
Wellbe Senior Medical | USA |
Brightline | USA |
Hitachi Energy | Switzerland |
Sae | USA |
Avidxchange | USA |
Galderma | Switzerland |
Neo Energy | UK |
Medex | USA |
Investissement Quebec | Canada |
Rio Tinto | UK |
Intellihartx | USA |
Homewood Health | Canada |
Allied Benefit Systems | USA |
Us Wellness | USA |
Rubrik | USA |
Onex | Canada |
Axis Bank | India |
People Corporation | Canada |
Medminder Systems | USA |
Cornerstone Home Lending | USA |
How to Mitigate the Risk of Clop Ransomware
According to TechTarget, GoAnywhere’s software vendor Fortra (formerly known as HelpSystems) became aware of a zero-day vulnerability in late January and warned its users of an “active exploitation and the dangers of keeping the administrative console exposed on the Internet”. Here are some actions that organizations can take to mitigate against the threat posed by Clop Ransomware
- Patching is your top priority: Fortra provided an update patch (7.1.2) for Windows Systems that should be applied as soon as possible to avoid any system compromise, especially all customers running an administration portal exposed to the Internet.
- Intentionally look for connections to C&C: after closing the publicly known door to the attackers is important to detect if they managed to enter the organization. The proficient way is doing it intentionally through the analysis of network metadata.
- Stay aware of lateral movements: in case attackers are inside your organization they will try to spread through the network infecting as many endpoints as they can. You can stop them on time by having visibility of this anomalous behavior. Analyzing netflows is usually the easiest way.
- Update access credentials: as the ultimate goal of attackers is to take control over the administrator console, they always try to compromise access credentials that’s why you need to avoid the risk of having any of your admin panels (not only GoAnywhere’s but any other integrated system) accessible to adversaries.
- Limit the surface attack: implement risk mitigation controls such as whitelisting entry connections, inspect any recent installation of apparently legitimate applications (such as cobaltStrike), creation of unusual administrator users, and disable the built-in licensing server system
To get to know your risk of being exposed to a ransomware attack, be sure to take Lumu’s Ransomware Quiz.