Table of Contents
When you think about the ideal target for a cyberattack, small businesses and/or startups may not come to mind. However, the reality is that they have become more appealing targets in recent years.
Here Are the Facts:
In a recent survey, 94% of small businesses said they have barriers in maintaining their security posture due to a lack of skilled security personnel.
Top attacks impacting startups:
- Endpoint attacks
- Malware
- Phishing
- Data Leaks
Perception:
Reality:
This is happening because cybercriminals perceive startups and smaller organizations to have little to no cybersecurity in place. They prefer to scale operations, targeting many different companies at once rather than coming up with sophisticated schemes to outsmart the cybersecurity operation of a larger company.
Where Do We Go from Here?
Allocating a security or IT budget to the right resources can be a challenge, but there are a few things to consider as a startup or small business.
Secure Remote Users
The modern workforce is distributed, but that should not add complexity to your cybersecurity operation. It’s important to have visibility and protection for roaming devices that will be accessing the network. Visibility gives a complete picture of your security posture and ensures coverage across all assets. Endpoint protection ensures secure remote access. Both are important elements of a proficient cybersecurity operation.
Orchestration and Automation
When working with limited resources, orchestration and automation are game-changers. Employees are experiencing burnout from trying to manage multiple tools and keep security practices in place. Orchestration allows you to easily prompt actions from different security tools so that they can work together and automation allows you to block threats in real-time. This enables a quick and precise response while freeing up time and resources for your organization.
Integrations
You can’t have orchestration and automation without integrations. This is an integral component of cyber-resiliency. Cybersecurity solutions should have the ability to integrate with other tools in your IT stack. This removes the gaps in security and ensures that orchestration workflows can do what you want them to do.
Start with Your Network
Cybersecurity is complex, but it doesn’t have to be. A good place to start for any organization is within the network. It paints a good picture of what is happening and gives the context needed to take appropriate action.
Here’s what the modern small business’ IT infrastructure looks like (without Lumu):
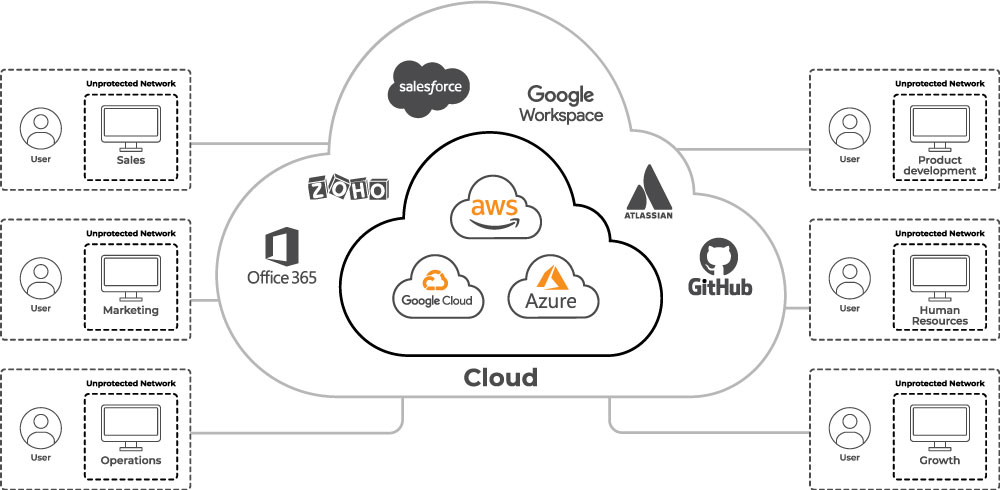
A network that is compromised behaves differently than one that is not. But how do you know if your network is compromised? Users are connecting to the network, but there is generally little to no visibility into whether there is adversarial contact taking place. This presents a significant risk to small businesses and a huge advantage to cybercriminals. It’s important to be able to quickly identify adversarial activity within the network. What starts out as precursor malware can very quickly become a full-blown ransomware attack with devastating effects.
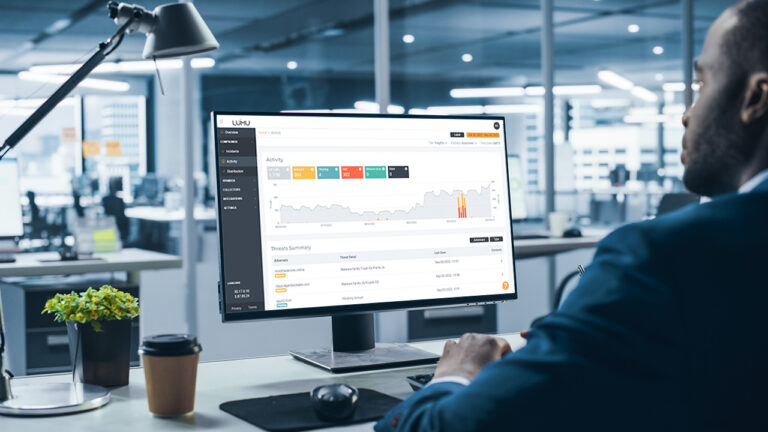
The Power of Lumu
When adding Lumu to your cybersecurity stack, you get a full picture of exactly what is happening and how it’s impacting your network.

With Lumu in place, cybersecurity operations can be automated. In this example, AWS and Google Cloud integrations are applied to the network and there is added visibility across all of the devices connecting.
Lumu gives visibility across the entire network to understand exactly who was impacted, what happened, when, and how. This gives cybersecurity operators the tools they need surrounding the nature of the attack and how to prevent future incidents.
Lumu seamlessly integrates with various security solutions to support orchestration workflows and automated, real-time incident response. Integrations are easy to implement with various out-of-the-box and API options available.
Want to learn more about how Lumu can help your business strengthen cybersecurity operations? Open a free account today.